Docker Syslog - Configuring Logging for Containers
Logs are useful for troubleshooting and identifying issues in applications, as they provide a record of events and activities. However, managing log data can be challenging due to the large volume of log events generated by modern applications, as well as the need to balance the level of detail in the logs and the impact on the application's performance.
Collecting logs from Docker can be challenging when running a large number of containers or running Docker on multiple hosts. These challenges include managing a large volume of logs, accessing logs from multiple hosts, ensuring the security of logs, and getting a comprehensive view of container and application behavior. A centralized logging system can help address these challenges by allowing you to store and manage all of your logs in a single location.
Docker Syslog is a built-in logging system provided by Docker that allows you to centralize and manage the logs produced by your Docker containers. In this article, we will delve into the capabilities of Docker Syslog, discuss how to configure and use it as a centralized logging solution for your Docker containers and demonstrate how it can be utilized to effectively manage and analyze your Docker logs.
Understanding Syslog
Syslog stands for System Logging Protocol. Syslog is a logging protocol that enables the collection and management of log messages from various devices and systems in a central location for monitoring and resolving issues on servers and networks. It is also the standard protocol used to send system logs or event messages to a specific server called a Syslog server.
A Syslog server is a network server that collects and stores log messages from devices and applications in a centralized location. It uses the Syslog protocol to receive log messages from various sources and store them in a database or log file for further analysis and management.
Syslog servers are commonly used to monitor and troubleshoot issues, as well as to comply with regulatory and security requirements. There are many Syslog servers available, including open-source options such as Rsyslog, Syslog-ng, and commercial solutions like Syslog-server.
What is Docker Syslog and Why It Matters
Docker Syslog is a logging driver for Docker that allows you to send container logs to a Syslog server. It is an integral part of the Docker engine, providing a native and reliable way to manage the logs from your Docker containers.
With Docker Syslog, you can centralize and manage the logs from your Docker containers in a single place, making it easier to monitor and troubleshoot issues. This means that when Docker runs applications, the log messages produced by those applications can be sent to the Syslog server for centralized storage and analysis.
Docker Syslog integrates with Syslog servers, allowing you to use the tools provided by them to manage and analyze the logs. It also offers customization options, such as the ability to specify the log format and Syslog facility, allowing you to tailor the logging behavior to fit your specific needs.
Key benefits of using Docker Syslog include:
- Centralized log collection: Aggregate logs from all containers in one place.
- Standardized log format: Syslog provides a consistent structure for log entries.
- Scalability: Easily handle logs from hundreds or thousands of containers.
- Integration: Compatible with various log analysis and monitoring tools.
Docker Syslog fits seamlessly into the Docker ecosystem, providing a reliable method for capturing and managing container logs without modifying application code.
Understanding Syslog in the Context of Docker
Syslog, a protocol for message logging, has been a staple in system administration for decades. It allows separation of software that generates messages, systems that store them, and software that analyzes them. Docker implements Syslog as a logging driver, adapting this time-tested protocol for container environments.
Key differences between traditional Syslog and Docker Syslog:
- Source identification: Docker Syslog includes container-specific metadata.
- Configuration: Logging options are set through Docker, not system-wide Syslog configs.
- Dynamic nature: Container logs are ephemeral, requiring different retention strategies.
The Docker Syslog logging driver consists of:
- Docker daemon: Configures and manages the Syslog driver.
- Logging driver: Captures container output and formats it for Syslog.
- Syslog server: Receives and stores logs (can be local or remote).

How to Configure Docker Syslog Logging Driver
The Syslog logging driver can be set up for both the Docker daemon and containers.
Setting up Syslog Logging driver for Docker Daemon
To configure the Docker Daemon to the Syslog driver:
Step 1: Go to the Docker daemon configuration file location: On Linux: /etc/docker/daemon.json directory
On Windows: C:\\\\ProgramData\\\\docker\\\\config\\\\daemon.json
To use the Syslog driver as the default logging driver for Docker on Linux, you need to set the log driver and log-opt.
Step 2: Setup the logging driver
{
"log-driver": "syslog"
}
Step 3: Add options for the Syslog logging driver by including the log-opts key. These options may include Syslog-address, Syslog-facility, and Syslog-format. This will set the Syslog driver as the default logging driver for the Docker daemon. The Docker daemon's logs will be written to the Syslog server according to the specified configuration.
An example is shown below,
{
"log-driver": "syslog",
"log-opts": {
"syslog-address": "tcp://127.0.0.1:514",
}
}
The log-driver and log-opt options are used to configure the logging driver for Docker. The logging driver determines how Docker handles log messages from containers and how it stores or forwards them.
- The
log-driveroption specifies the logging driver to use - The
log-optsoption allows you to pass additional options to the logging driver. In the above configuration, the additional option passed is thesyslog-addressoption. - The
syslog-addressoption is used to specify the address of a Syslog server. Docker will send the container's log output to the specified Syslog server.
There are more log-opts options that can be applied to fit your specific needs
{
"log-driver": "syslog",
"log-opts": {
"syslog-address": "tcp://127.0.0.1:514",
"syslog-facility": "daemon",
"syslog-format": "rfc5424micro"
}
}
To view a complete list of the log-opts options available, visit the official docker documentation page.
Step 4: Configure and save the daemon.json file, then restart the Docker daemon to apply the changes.
sudo systemctl daemon-reload
sudo systemctl restart docker
Setting up Syslog Logging driver for Docker Containers
If you decide to configure the Syslog driver for individual or specific containers, you can use the log-driver and log-opt options when starting the container.
Examples as shown below
docker run \\\\
--log-driver syslog \\\\
--log-opt syslog-address=udp://1.2.3.4:1111 \\\\
alpine echo hello world
docker run \\\\
--log-driver syslog \\\\
--log-opt syslog-address=tcp://syslog_server_host:514 \\\\
--log-opt syslog-facility=daemon \\\\
--log-opt syslog-format=json image_name
- The
syslog-facilityoption is used to specify the Syslog facility value that should be associated with the container's log messages. The Syslog facility value is a numeric or symbolic value that identifies the source of the log message and is used to categorize and filter the log data. Sample values that can be used includeauth,cron,daemon,kern, etc. - The
syslog-formatoption is used to specify the format in which the container's log messages should be sent to the Syslog server. Examples of more formats that could be used in Docker includejson,rfc3164,rfc5424,text, etc.
Best practices for Docker Syslog configuration:
- Use TCP instead of UDP for more reliable log transmission.
- Implement log rotation to manage disk space.
- Set appropriate log levels to balance verbosity and performance.
- Use tags to categorize logs from different applications or environments.
Advanced Syslog Configuration Options
To fine-tune your Docker Syslog setup, consider these advanced options:
- Tagging: Use tags to organize logs by application or environment:
{
"log-opts": {
"tag": "{{.Name}}/{{.ID}}"
}
}
- Log rotation: Implement size-based log rotation:
{
"log-opts": {
"syslog-facility": "daemon",
"max-size": "10m",
"max-file": "3"
}
}
- Severity levels: Set appropriate Syslog severity levels:
{
"log-opts": {
"syslog-facility": "local0",
"syslog-format": "rfc5424micro"
}
}
- Secure transmission: Use TLS for encrypted log transmission:
{
"log-opts": {
"syslog-address": "tcp://192.168.0.42:6514",
"syslog-tls-cert": "/path/to/cert.pem",
"syslog-tls-key": "/path/to/key.pem",
"syslog-tls-ca-cert": "/path/to/ca.pem"
}
}
These advanced options allow for a more tailored and secure Docker Syslog implementation.
Limitations of Docker Syslog
Using Docker with the syslog logging driver has several limitations that users should be aware of:
- No Built-in Log Rotation: By default, the syslog driver does not handle log rotation on the Docker host. This can result in log files growing indefinitely, potentially consuming significant disk space over time.
- Decompression Overhead: Reading log information from rotated and compressed log files requires decompression, temporarily increasing disk usage and CPU load. This can impact system performance, especially under heavy logging activities.
- Limited Metadata: The syslog logging driver may include less metadata about the Docker containers compared to other logging drivers, such as the name, ID, or labels of the container. This can limit the ability to filter and search logs effectively.
Troubleshooting Common Docker Syslog Issues
Even with proper configuration, you may encounter issues with Docker Syslog. Here are some common problems and their solutions:
- Connection problems:
- Verify Syslog server address and port.
- Check firewall rules allowing traffic.
- Ensure the Syslog server is running and accepting connections.
- Log format errors:
- Confirm Syslog server supports the chosen format (RFC3164 or RFC5424).
- Verify tag formatting in Docker configuration.
- High-volume logging:
- Implement log sampling or filtering at the container level.
- Increase Syslog server resources or distribute logs across multiple servers.
- Performance impacts:
- Monitor Docker host CPU and network usage.
- Adjust log verbosity levels for non-critical containers.
- Consider asynchronous logging options for high-throughput applications.
To debug Syslog issues, use Docker's built-in logging commands:
docker logs <container_id>
docker inspect <container_id>
These commands provide insights into container logging configuration and output.
Docker Logs analysis with SigNoz
While traditional log management tools offer valuable insights, modern observability platforms like SigNoz provide a more comprehensive approach to container monitoring.
SigNoz is a full-stack open-source Application Performance Monitoring tool that you can use for monitoring logs, metrics, and traces. One key aspect of observability is log management, and SigNoz provides a range of tools for collecting, analyzing, and visualizing Docker logs.
It uses ClickHouse, a columnar database, to efficiently store and provide access to log data for analysis.
SigNoz complements Docker Syslog by offering:
- Real-time log analysis: Instantly search and filter logs across all containers.
- Correlation with metrics and traces: Connect logs to application performance data.
- Advanced visualization: Create custom dashboards for log data.
- Anomaly detection: Automatically identify unusual log patterns.
SigNoz uses OpenTelemetry for instrumenting applications. OpenTelemetry, backed by CNCF, is quickly becoming the world standard for instrumenting cloud-native applications.
The logs tab in SigNoz has advanced features like a log query builder, search across multiple fields, structured table view, JSON view, etc.
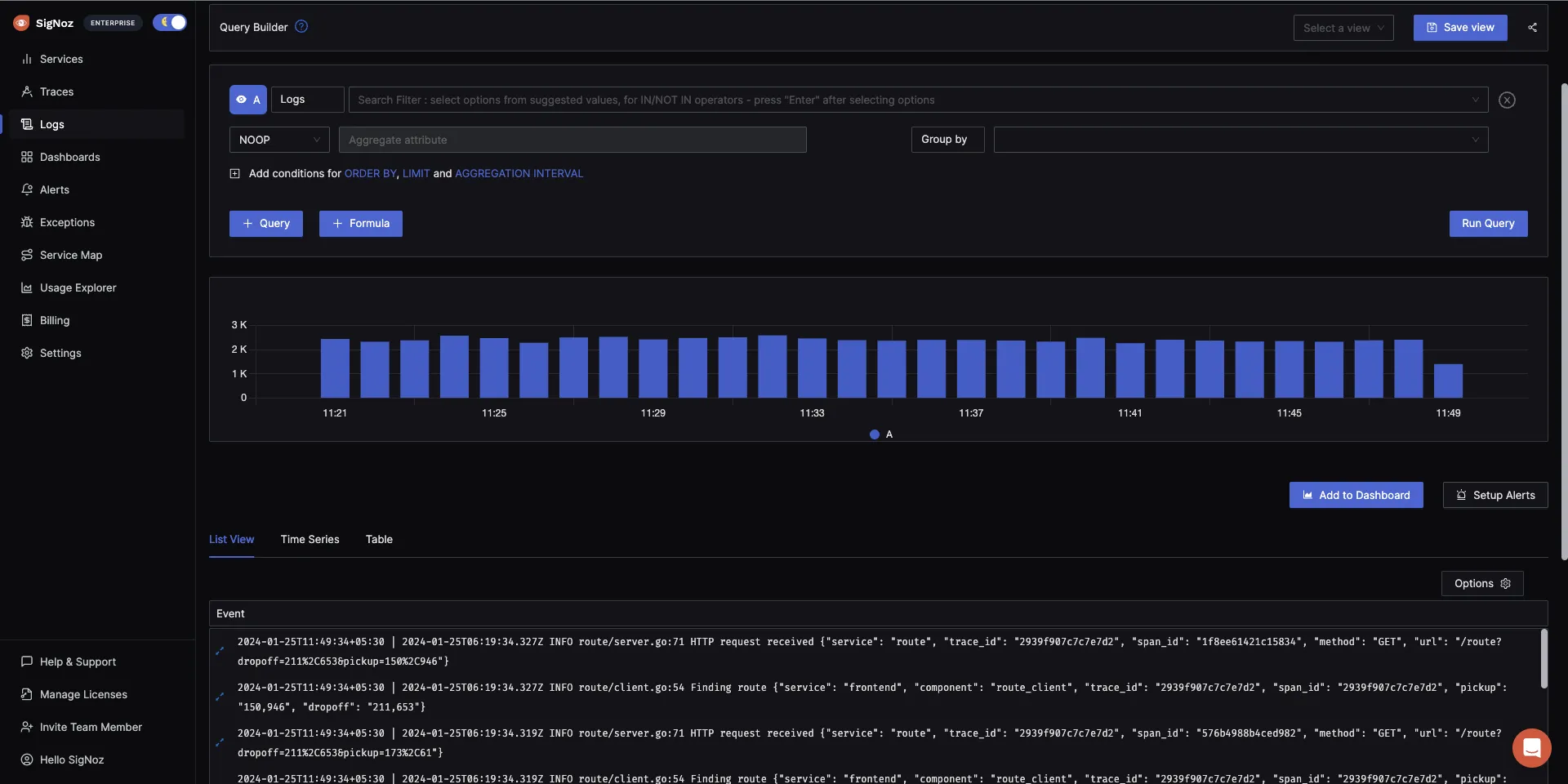
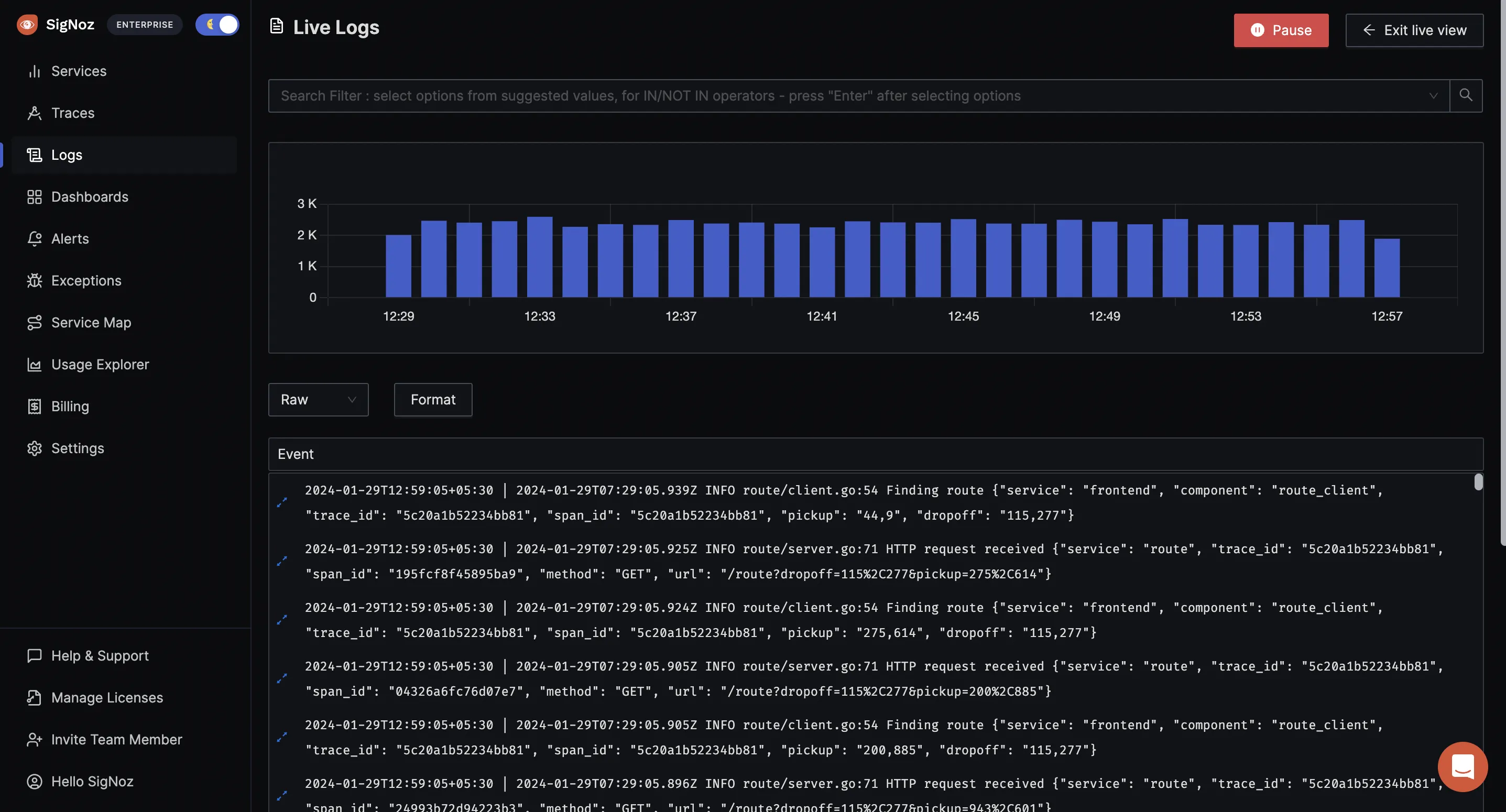
SigNoz offers real-time analysis of logs, enabling you to search, filter, and visualize them as they are generated. This can assist in identifying patterns, trends, and problems in the logs and resolving issues efficiently.
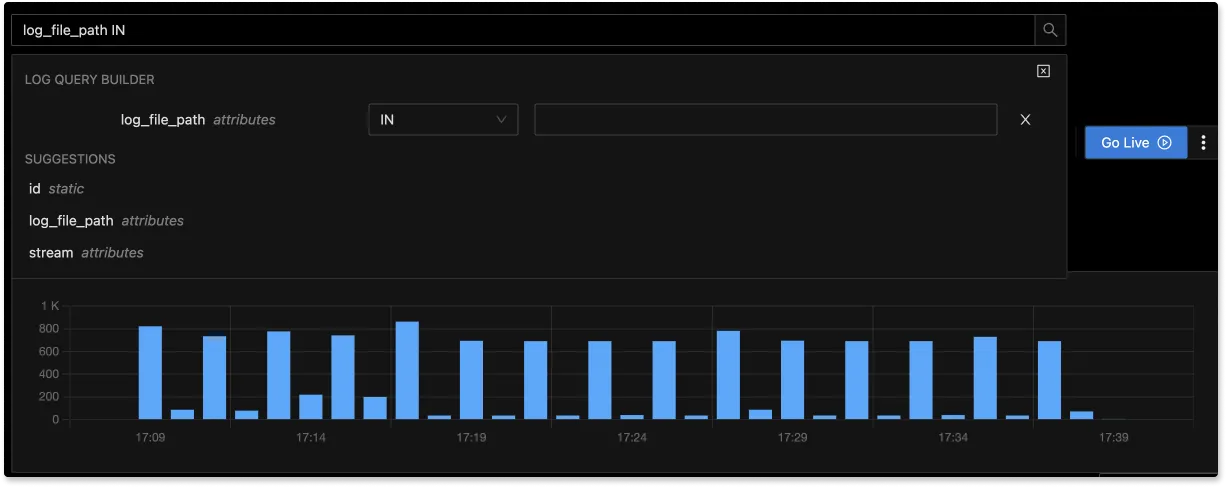
With the advanced Log Query Builder, you can filter out logs quickly with a mix and match of fields.
Getting Started with SigNoz
SigNoz Cloud is the easiest way to run SigNoz. Sign up for a free account and get 30 days of unlimited access to all features.
You can also install and self-host SigNoz yourself since it is open-source. With 24,000+ GitHub stars, open-source SigNoz is loved by developers. Find the instructions to self-host SigNoz.
Best Practices for Docker Syslog Implementation
To maximize the benefits of Docker Syslog, follow these best practices:
- Structure log messages: Use JSON logging for easier parsing and analysis.
- Implement log retention policies: Balance storage costs with compliance requirements.
- Monitor logging performance: Watch for increased latency or resource usage.
- Use environment variables: Externalize logging configuration for flexibility.
- Implement log sampling: Reduce volume for high-throughput applications.
- Secure log transmission: Use TLS encryption for sensitive log data.
- Regularly audit logging setup: Ensure all critical containers are logging correctly.
- Implement alerting: Set up notifications for critical log events.
By following these practices, you'll create a robust, scalable logging infrastructure for your Docker environment.
Final Thoughts
In this article, we discussed Syslog, Docker Syslog as a logging driver, and how to set it up for Docker daemon and containers.
It is important to have a separate log management platform that provides additional capabilities and flexibility for managing and analyzing the Syslog logs from your Docker containers.
A centralized log management tool can also help to ensure that you have a robust and scalable solution for log analytics that meets your specific needs and requirements, as the Syslog server or logging driver may not have the necessary features or capabilities to fully manage and analyze the logs. For example, you may want to perform complex log parsing, filtering, or transformation operations that are not possible with the Syslog server or logging driver.
An advanced centralized logging platform/tool for collecting your logs is SigNoz - an open source log management solution.
Key Takeaways
- Docker Syslog provides centralized logging for containerized applications.
- Proper configuration is essential for effective log management.
- Advanced options allow for customized and secure logging setups.
- Integration with tools like SigNoz enhances log analysis capabilities.
- Best practices ensure optimal performance and compliance.
FAQs
How does Docker Syslog differ from other logging drivers?
Docker Syslog uses the standardized Syslog protocol, making it compatible with a wide range of log management tools. Other drivers like JSON-file or Fluentd offer different features — JSON-file stores logs locally, while Fluentd provides more flexibility in routing logs to various destinations.
Can I use Docker Syslog with orchestration platforms like Kubernetes?
Yes, Docker Syslog can be used with Kubernetes. However, Kubernetes has its own logging architecture, and you may need to configure it to work with Syslog. Many users opt for solutions like Fluentd or Logstash in Kubernetes environments for more flexibility.
What are the performance implications of using Docker Syslog?
Docker Syslog generally has minimal performance impact. However, high log volumes or network latency to remote Syslog servers can affect container performance. Monitor your setup and consider log sampling or local buffering for high-throughput scenarios.
How can I ensure my Docker Syslog configuration is secure?
To secure your Docker Syslog setup:
- Use TLS encryption for log transmission.
- Implement access controls on the Syslog server.
- Regularly update Docker and Syslog server software.
- Use separate Syslog facilities for different security levels of logs.
- Implement log rotation and secure storage practices.
What is Docker Syslog and how does it work?
Docker Syslog is a logging driver that allows you to send container logs to a centralized Syslog server. It captures log output from containers and formats it according to the Syslog protocol before sending it to a configured Syslog server for storage and analysis.
What are the main benefits of using Docker Syslog?
The key benefits include centralized log collection, standardized log format, scalability to handle logs from many containers, and easy integration with existing log analysis tools. It allows you to aggregate and manage logs from all your containers in one place.
How do I configure Docker to use the Syslog logging driver?
You can configure Syslog logging for the Docker daemon by editing the daemon.json file and specifying "log-driver": "syslog" along with any log-opts. For individual containers, use the --log-driver and --log-opt flags when running the container.
What are some best practices for implementing Docker Syslog?
Some best practices include using TCP instead of UDP for reliability, implementing log rotation, setting appropriate log levels, using tags to categorize logs, encrypting log transmission with TLS, and regularly auditing your logging setup.
What are the limitations of Docker Syslog?
The main limitations are lack of built-in log rotation, potential performance overhead from log decompression, and limited container metadata compared to some other logging drivers. It also does not support SSL/TLS connections to remote Syslog servers out of the box.
Related Posts
Docker Logging Complete Guide - Configuration and Logging Strategies
