15 Best Docker Alternatives for 2026: Complete Guide with Pros, Cons & Migration
For years, Docker has been the go-to tool for containerization, but the landscape is evolving. Today, many developers and organizations are exploring Docker alternatives to address concerns around security, cost, and complexity.
Modern alternatives often feature a daemonless architecture, meaning they don't rely on a single, continuously running background service (a daemon) that can become a bottleneck or security risk. Many are also rootless, allowing them to run without requiring the highest level of system privileges ("root"), which significantly improves security. Others are Kubernetes-native, designed from the ground up to work seamlessly with Kubernetes, the industry-standard container orchestrator.
This guide will walk you through 15 of the best Docker alternatives, breaking down their strengths, weaknesses, and ideal use cases so you can make an informed decision for your projects.
Why Look for a Docker Alternative?
While Docker made containers popular, some of its design choices have led users to seek other options:
Security Risks: Docker's architecture relies on a central daemon that runs with root privileges. If this daemon is ever compromised, an attacker could gain control over every container on the system, creating a single point of failure.
Licensing Costs: Docker Desktop, the popular version of Docker for Windows and macOS, now requires a paid subscription for use in larger businesses. This has pushed many to look for free, open-source alternatives.
Resource Usage: The Docker daemon can be resource-intensive, consuming memory and CPU that could otherwise be used by applications. In large-scale deployments, this overhead can add up.
Will My Existing Images Still Work with Docker Alternatives?
Yes, almost certainly. The good news is that you won't have to rebuild all your container images from scratch. This is thanks to the Open Container Initiative (OCI), which creates open standards for container technology. Think of the OCI as a set of rules that ensures containers are portable and work consistently across different tools.
Because Docker and all the major alternatives follow these OCI standards, you can use the same container images you built with Docker on a different runtime. This prevents vendor lock-in and makes switching tools much easier.
Top 15 Docker Alternatives

1. Podman - A Secure, Daemonless Alternative
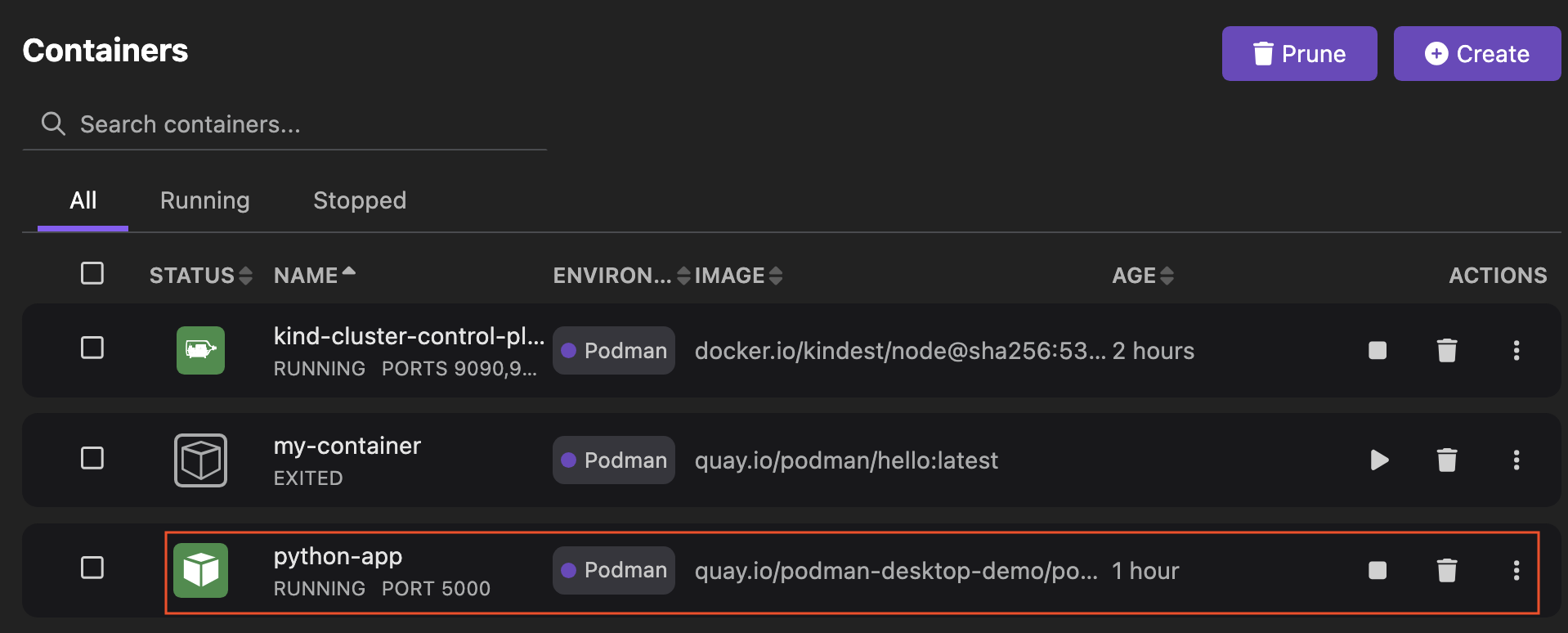
Podman is a popular Docker alternative that was designed with security as a top priority. Its main advantage is that it is daemonless, meaning it runs containers without a central background service. This, combined with its ability to run in rootless mode, makes it one of the most secure container runtimes available.
Architecture: Podman runs containers as direct child processes of the user's session. This simple design eliminates the central daemon, which is a common attack vector in Docker.
Key Features:
- Rootless by Default: Runs containers as a regular user, not as the powerful "root" user.
- Pod Support: Can manage groups of related containers together in "pods," similar to Kubernetes.
- Docker CLI Compatibility: You can often use
podmanas a drop-in replacement for thedockercommand. - Systemd Integration: Works well with
systemd, the standard service manager on many Linux systems. - Docker Compose Support: Can run multi-container applications defined in
docker-compose.ymlfiles.
Pros:
- More secure because it has no central daemon and runs without root privileges.
- Uses less memory than Docker.
- Integrates well with modern Linux systems.
- Easy to migrate to, thanks to its Docker-compatible command line.
- Backed by Red Hat, ensuring long-term support.
Cons:
- Networking in rootless mode can be slower in some high-performance scenarios.
- Does not support Docker Swarm.
- Support for Windows is still catching up to Docker Desktop.
Migration Complexity: Easy. For many users, simply creating a command-line alias (alias docker=podman) is enough to get started.
Best Use Cases: Security-conscious environments, production systems that use systemd, and as a more secure replacement for Docker on developer machines.
2. Containerd - The Engine Under the Hood
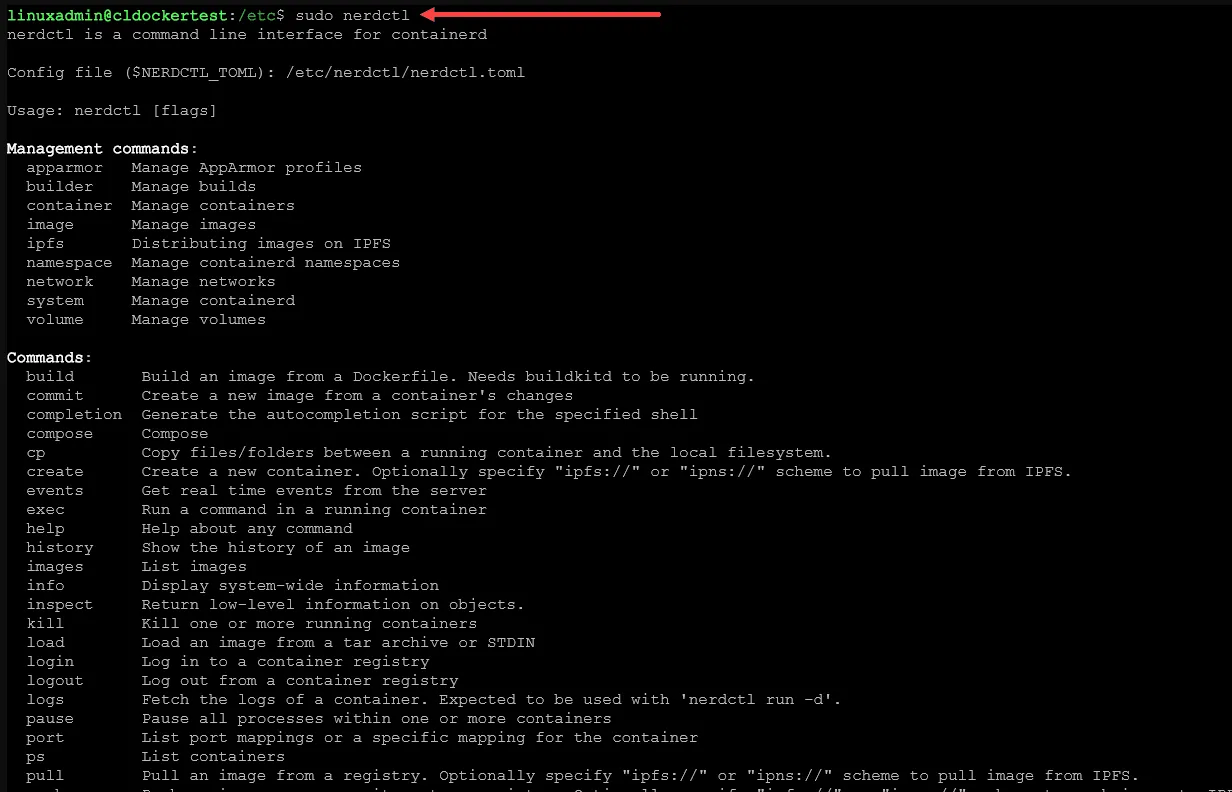
containerd is the core container runtime that was originally extracted from the Docker project. Today, it is the industry-standard engine that powers many container platforms, including Docker itself, as well as major Kubernetes services from Google, AWS, and Microsoft.
Architecture: A minimal, efficient runtime focused on the core tasks of managing the container lifecycle (starting, stopping, etc.). It is designed to be embedded into larger systems.
Key Features:
- Minimal and Efficient: A streamlined runtime with a small resource footprint.
- The Kubernetes Standard: The default container runtime for most Kubernetes distributions.
- OCI Compliant: Fully supports the OCI standards for images and runtimes.
- Pluggable: Can be extended with plugins for different kinds of storage or runtimes.
- Industry-Standard: Used and trusted by all major cloud providers.
Pros:
- Very lightweight and fast, with low resource usage.
- Proven to be stable and reliable in massive production environments.
- Backed by the Cloud Native Computing Foundation (CNCF).
- Integrates seamlessly with Kubernetes without any extra layers.
Cons:
- Not designed to be user-friendly on its own; it lacks a built-in command-line interface like Docker's.
- To use it directly, you need an additional tool like
nerdctlto provide a familiar experience. - Has fewer high-level features than a full-featured tool like Docker or Podman.
Migration Complexity: Moderate. While powerful, using it directly requires installing and learning a separate client tool like nerdctl.
Best Use Cases: Kubernetes deployments, cloud-native applications, and any environment where performance and minimal overhead are top priorities.
3. LXC/LXD - Full Linux System Containers
LXC and its management layer, LXD, create system containers, which are different from Docker's application containers. A system container behaves like a lightweight virtual machine, running a full Linux operating system inside. This is useful for legacy applications that expect a traditional OS environment.
Architecture: Uses Linux kernel features (namespaces and cgroups) to provide OS-level virtualization, isolating a complete operating system instead of just a single application.
Key Features:
- Full OS Containers: Run complete Linux distributions with their own init systems.
- Unprivileged Mode: Can run without root privileges for better security.
- Live Migration: Move running containers between different machines with no downtime.
- Advanced Storage: Integrates with ZFS and Btrfs for features like snapshots.
- REST API: LXD provides a modern API for management and clustering.
Pros:
- Performance is close to a native installation, with less overhead than a full VM.
- Strong isolation between the container and the host system.
- Ideal for moving older applications into a container-like workflow.
- Mature and stable technology with a long history.
Cons:
- A different approach from Docker, which may require a mindset shift.
- Steeper learning curve for those accustomed to application containers.
- Primarily focused on Linux, with limited support for other platforms.
Migration Complexity: Hard. Migrating from Docker requires rethinking your application's architecture to fit the system container model.
Best Use Cases: Running legacy applications, creating full development environments, and situations where you need the isolation of a VM with better performance.
4. CRI-O - A Runtime Built for Kubernetes
CRI-O is a lightweight container runtime created specifically for Kubernetes. It implements the Container Runtime Interface (CRI), a standard that lets Kubernetes communicate with any compatible container runtime. CRI-O includes only the features Kubernetes needs, making it minimal and efficient.
Architecture: A lean implementation of the CRI that uses OCI-compliant runtimes like runc to launch containers. It is designed to be a simple bridge between Kubernetes and the container runtime.
Key Features:
- Kubernetes Native: Built from the ground up to work with Kubernetes.
- Minimalist Design: Strips out any features not required by Kubernetes, reducing its footprint.
- Multi-Runtime Support: Can use different OCI runtimes as its backend.
- Strong Security: Supports standard Linux security features like SELinux and AppArmor.
- CNCF Project: Maintained by the Cloud Native Computing Foundation, ensuring community support.
Pros:
- Highly optimized for Kubernetes, resulting in lower resource usage and faster performance.
- A smaller attack surface because it has fewer features.
- Strong security model with support for various security policies.
- Avoids features that could lead to vulnerabilities.
Cons:
- Only works within a Kubernetes environment; it cannot be used as a standalone tool.
- Lacks the user-friendly management tools found in Docker.
- Requires Kubernetes to be useful.
Migration Complexity: Easy (for Kubernetes users). If you're already using Kubernetes, switching to CRI-O is a straightforward configuration change in your cluster.
Best Use Cases: Production Kubernetes clusters, especially in security-conscious environments where a minimal runtime is preferred.
5. Buildah - A Tool for Building Container Images
Buildah is a specialized tool that focuses on one thing: building OCI-compliant container images. Unlike Docker, it does not require a daemon to run, which makes it more secure and flexible, especially in automated environments like CI/CD pipelines.
Architecture: A daemonless command-line tool that lets you build images from a Dockerfile or from scratch using shell scripts. It gives you fine-grained control over the image layers.
Key Features:
- Daemonless Building: Builds images without needing a background service.
- Scriptable: Can be easily integrated into automated scripts for complex builds.
- Fine-Grained Control: Allows you to mount a container's filesystem and modify it directly.
- Rootless Building: Can build images without requiring root privileges.
- Multi-Architecture Support: Can build images for different CPU architectures.
Pros:
- More secure because it runs without a daemon and can operate in rootless mode.
- Highly flexible, allowing for complex build logic through scripting.
- Uses fewer resources compared to Docker's build process.
- Integrates well with CI/CD systems.
Cons:
- Only builds images; it does not run or manage containers.
- Can have a learning curve, especially for its advanced scripting features.
- Primarily for Linux, with no native support for Windows or macOS.
Migration Complexity: Moderate. While it can use existing Dockerfiles, migrating CI/CD pipelines may require rewriting build scripts.
Best Use Cases: Building container images in CI/CD pipelines, creating custom build workflows, and in secure environments where a daemon is not desirable.
6. Rancher Desktop - A Docker Desktop Alternative with a GUI
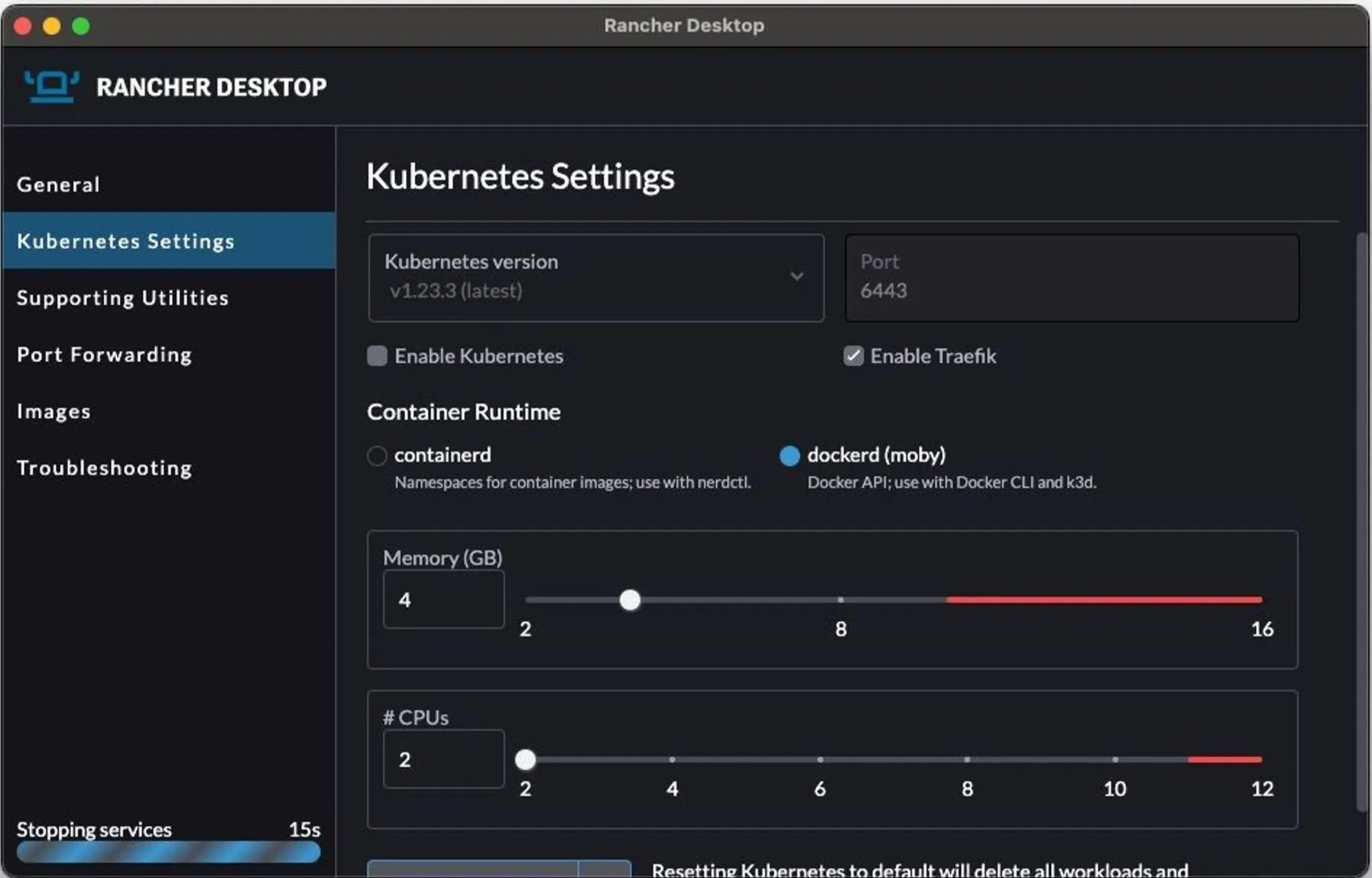
Rancher Desktop is a free and open-source application for Mac, Windows, and Linux that provides a graphical user interface (GUI) for container management. It's a popular alternative to Docker Desktop, especially for developers.
Architecture: A desktop application that manages container runtimes like containerd and provides a built-in Kubernetes cluster (K3s) for local development.
Key Features:
- Intuitive GUI: A user-friendly interface for managing containers and Kubernetes.
- Choice of Runtimes: Lets you choose between
containerdand Docker's Moby engine. - Local Kubernetes: Includes the lightweight K3s distribution for easy local Kubernetes development.
- Cross-Platform: Works on Windows, macOS, and Linux.
- Extensible: Supports extensions for adding more functionality.
Pros:
- Easy to learn, especially for those who prefer a graphical interface.
- No commercial licensing fees, unlike Docker Desktop.
- Simplifies local Kubernetes development.
- Actively developed and supported by a strong community.
Cons:
- Best suited for local development, not production.
- The reliance on a GUI makes it less suitable for automation.
- Uses more resources than command-line-only tools.
Migration Complexity: Easy. The familiar interface makes it a simple switch for Docker Desktop users.
Best Use Cases: Local development, replacing Docker Desktop, and for developers who prefer a GUI for managing containers and Kubernetes.
7. Red Hat OpenShift - An Enterprise-Grade Kubernetes Platform
OpenShift is a comprehensive container platform built on top of Kubernetes. It is designed for large organizations and includes features for security, CI/CD, and developer productivity. Think of it as Kubernetes with batteries included, tailored for enterprise use.
Architecture: An extended version of Kubernetes that adds a suite of integrated tools, including a container registry, automated build pipelines (Source-to-Image), and advanced security policies.
Key Features:
- Built on Kubernetes: Starts with a standard Kubernetes core and adds enterprise features.
- Integrated CI/CD: Provides built-in tools for continuous integration and deployment.
- Security-First: Implements strict security policies and role-based access control (RBAC) by default.
- Developer-Friendly: Offers a web console, command-line tools, and IDE integrations.
- Multi-Cloud Support: Can be deployed consistently across different cloud providers and on-premise data centers.
Pros:
- A complete, all-in-one platform with commercial support from Red Hat.
- Strong security features suitable for regulated industries.
- Streamlines both development and operations workflows.
- Access to professional training and certification.
Cons:
- Can be expensive, with significant licensing costs.
- May be too complex for smaller projects or teams.
- Requires more system resources than a standard Kubernetes installation.
- Has a learning curve due to its additional features.
Migration Complexity: Hard. Moving to OpenShift is a major architectural decision that involves adopting a new platform, not just a new tool.
Best Use Cases: Large enterprises, government agencies, and organizations that need a fully supported, secure, and integrated container platform.
8. runC - The Core Container Runtime
runC is a low-level container runtime that implements the OCI Runtime Specification. It is not a full-featured Docker alternative but rather a fundamental building block. Most other container tools, including Docker, containerd, and Podman, use runC under the hood to actually run containers.
Architecture: A minimal command-line tool that creates and runs containers according to the OCI standard. It focuses solely on the container's lifecycle and does not include features like image management or networking.
Key Features:
- OCI Standard: The official reference implementation of the OCI Runtime Specification.
- Lightweight: Has a very small footprint and minimal dependencies.
- Core Component: Serves as the foundation for most higher-level container platforms.
- Secure: Supports standard Linux security features like namespaces and cgroups.
Pros:
- Extremely low resource usage and minimal attack surface.
- Proven in production as the core of major container platforms.
- Offers direct control over how containers are executed.
- High performance with almost no overhead.
Cons:
- Not intended for direct use by most developers; it requires significant expertise.
- Lacks user-friendly features for image or network management.
- Requires custom tooling to be used effectively.
Migration Complexity: Very Hard. Using runC directly would require building your own container management platform from scratch.
Best Use Cases: Developing custom container platforms, for use in embedded systems, or in research environments that require precise control over container execution.
9. HashiCorp Nomad - A Flexible Workload Orchestrator
Nomad is a workload orchestrator from HashiCorp, the creators of Terraform and Vault. It is an alternative to Kubernetes and Docker Swarm that is known for its simplicity and flexibility. Unlike Kubernetes, which only orchestrates containers, Nomad can also manage VMs, standalone applications, and batch jobs.
Architecture: A single binary that can be run as a server or a client. It is designed for multi-region and multi-cloud deployments and uses a flexible scheduling algorithm.
Key Features:
- Multi-Workload Support: Can orchestrate containers, virtual machines, and other applications.
- Simple Architecture: Consists of a single binary, making it easy to deploy and manage.
- Multi-Region Federation: Natively supports connecting clusters across different regions.
- Flexible Scheduling: Offers advanced options for placing workloads on your infrastructure.
- HashiCorp Ecosystem: Integrates seamlessly with other HashiCorp tools like Consul and Vault.
Pros:
- Simpler to set up and manage than Kubernetes.
- Highly efficient in its resource usage.
- Well-suited for multi-region and edge computing scenarios.
- A single tool for orchestrating diverse types of workloads.
Cons:
- Has a smaller community and ecosystem than Kubernetes.
- Fewer third-party tools and integrations are available.
- Requires learning HashiCorp-specific concepts.
- Some advanced features are only available in the enterprise version.
Migration Complexity: Moderate. Migrating from Kubernetes or Docker Swarm requires rewriting your orchestration logic for Nomad's job specification format.
Best Use Cases: Environments with a mix of workloads (containers, VMs, etc.), edge computing, hybrid cloud setups, and for organizations already invested in the HashiCorp ecosystem.
10. Lima - Containers on macOS
Lima (short for Linux on Mac) is a tool that simplifies running containers on macOS. It automatically creates and manages a lightweight Linux virtual machine, providing a seamless way to use container runtimes like containerd and Podman on a Mac.
Architecture: A command-line tool that sets up a Linux VM with automatic file sharing and port forwarding, making it easy to run containers on macOS without the overhead of a full desktop application.
Key Features:
- Automatic VM Management: Handles the creation and configuration of the Linux VM.
- Multi-Runtime Support: Works with
containerd, Docker, and Podman. - Seamless Integration: Provides file sharing and port forwarding between macOS and the VM.
- Apple Silicon Support: Works on both Intel and Apple Silicon (M1/M2) Macs.
Pros:
- A lightweight and open-source alternative to Docker Desktop for macOS.
- No commercial licensing fees.
- Good performance, especially on Apple Silicon Macs.
- Simple to configure and use.
Cons:
- Only for macOS users.
- Still has the overhead of a VM, unlike native Linux containers.
- A smaller community and feature set compared to Docker Desktop.
Migration Complexity: Easy (for macOS users). It is a straightforward replacement for Docker Desktop for most development tasks.
Best Use Cases: macOS developers looking for a free and simple alternative to Docker Desktop, especially those using Apple Silicon Macs.
11. AWS Finch - A Container Client for macOS from AWS
Finch is an open-source command-line tool from Amazon Web Services (AWS) for container development on macOS. It bundles several other open-source tools (like Lima and nerdctl) to create a simple and unified experience, similar to the Docker command line.
Architecture: An integrated client that uses Lima to manage a Linux VM, containerd as the runtime, and nerdctl to provide a Docker-compatible CLI.
Key Features:
- Backed by AWS: Maintained and supported by Amazon Web Services.
containerdInside: Uses the industry-standardcontainerdruntime.- Docker-Compatible CLI: The
nerdctlcomponent provides a familiar command-line experience. - Optimized for macOS: Designed specifically for container development on macOS.
Pros:
- Strong backing from AWS ensures its continued development.
- Good performance on macOS.
- Easy to learn for those already familiar with Docker commands.
- Potential for future integration with AWS services.
Cons:
- Only for macOS users.
- A relatively new tool with a smaller community.
- Primarily for development, not production.
Migration Complexity: Easy (for macOS developers). It is a simple replacement for Docker Desktop, especially for those who use AWS.
Best Use Cases: Developers on macOS who are building applications for AWS, and teams looking for a simple Docker Desktop alternative.
12. Firecracker - Micro-VMs for Serverless Computing
Firecracker is a Virtual Machine Monitor (VMM) that creates ultra-lightweight virtual machines called micro-VMs. It was developed by AWS to provide strong security isolation for serverless products like AWS Lambda and AWS Fargate. It is designed for speed and efficiency.
Architecture: A specialized VMM that launches minimal micro-VMs with extremely fast boot times and low memory overhead. It provides hardware-level isolation, which is more secure than traditional containers.
Key Features:
- Micro-VMs: Creates lightweight VMs that are more efficient than traditional VMs.
- Fast Startup: Can launch a micro-VM in under a second.
- Hardware Isolation: Provides strong security by using hardware virtualization.
- Minimalist: Has a small trusted computing base (TCB), which reduces the attack surface.
- Used by AWS: Powers major AWS services, proving its stability at scale.
Pros:
- Extremely fast boot times (under 100ms).
- Strong security isolation, making it ideal for running untrusted code.
- Very low resource usage per micro-VM.
- Battle-tested in AWS's production environments.
Cons:
- Only works on Linux with KVM virtualization.
- Requires specialized knowledge to implement and manage.
- Focused on serverless and function-based workloads, not general-purpose containers.
Migration Complexity: Very Hard. Adopting Firecracker requires a fundamental shift to a serverless architecture.
Best Use Cases: Building serverless platforms, function-as-a-service (FaaS) implementations, and multi-tenant systems that require strong security isolation.
13. gVisor - A Secure Application Kernel
gVisor is a security-focused tool from Google that adds an extra layer of isolation to containers. It does this by creating a special user-space kernel for each container, which intercepts and handles system calls from the application. This prevents the container from interacting directly with the host system's kernel.
Architecture: A user-space kernel that acts as a middleman between the container and the host OS. It filters system calls to limit the container's privileges and reduce the host's attack surface.
Key Features:
- User-Space Kernel: An application-specific kernel that runs in user space for better isolation.
- System Call Interception: Catches and handles system calls made by the container.
- OCI Compatible: Works with existing container tools like Docker and Kubernetes.
- Defense in Depth: Adds another layer of security to your container setup.
- Developed by Google: Actively maintained and used by Google.
Pros:
- Significantly improves security by isolating the container from the host kernel.
- Reduces the attack surface of the host system.
- Compatible with existing container workflows.
- Backed by Google, ensuring its quality and longevity.
Cons:
- Can introduce performance overhead because it has to process every system call.
- May not be compatible with applications that need direct access to specific kernel features.
- Can make debugging more complex.
Migration Complexity: Moderate. It can be added to an existing container setup, but it requires changes to the container runtime configuration.
Best Use Cases: Running untrusted code, in multi-tenant environments, and in any situation where security is more important than raw performance.
14. Colima - Simple Containers for macOS and Linux
Colima (Container Linux Machines) is a command-line tool that provides a simple way to run containers on macOS and Linux. It focuses on a minimal setup and a user-friendly experience for developers.
Architecture: A simple tool for managing container runtimes. It can be configured to use Docker, containerd, or even Kubernetes as its backend.
Key Features:
- Minimal Setup: Designed to be easy to install and configure.
- Multiple Backends: Supports different container runtimes.
- Resource Management: Allows you to configure CPU, memory, and disk space.
- Developer-Focused: Optimized for local development workflows.
Pros:
- Very simple to set up and use.
- Good performance with low resource overhead.
- No licensing fees or restrictions.
- Actively developed by the community.
Cons:
- Primarily for development, not production.
- Has a smaller community and feature set than larger projects.
- Documentation is not as extensive as some alternatives.
Migration Complexity: Easy. It is a straightforward replacement for Docker Desktop for local development.
Best Use Cases: Local development, as a simple alternative to Docker Desktop, and for developers who want a minimal and easy-to-use setup.
15. Kata Containers - VM-Level Security for Containers
Kata Containers is a project that combines the security of virtual machines with the speed and manageability of containers. It runs each container in its own lightweight VM, providing strong, hardware-level isolation.
Architecture: An OCI-compliant runtime that launches each container in a dedicated micro-VM. This provides hardware isolation while still using standard container APIs and workflows.
Key Features:
- VM-Based Isolation: Uses hardware virtualization for strong security.
- Standard Container Interface: Works with existing container tools and orchestrators.
- Multiple Hypervisors: Supports different VMMs, including QEMU and Firecracker.
- OCI Compliant: Can be used as a runtime in Docker and Kubernetes.
- Backed by OpenInfra Foundation: Supported by a major open-source foundation.
Pros:
- Provides the strongest security isolation available for containers.
- Suitable for running untrusted or sensitive applications.
- Compatible with existing container management tools.
- Backed by a strong open-source community.
Cons:
- Uses more system resources due to the overhead of running a VM for each container.
- Slower container startup times compared to traditional containers.
- Can be complex to set up and configure.
Migration Complexity: Moderate. It can be integrated into an existing setup by changing the container runtime configuration, but it requires careful planning.
Best Use Cases: High-security environments, regulated industries, multi-tenant platforms, and any scenario where you need to run untrusted code with maximum isolation.
Performance and Resource Comparison
Here is a general comparison of how these alternatives perform. Actual performance will vary based on your specific workload and hardware.
Container Startup Performance
- Fastest: LXC, CRI-O,
containerd(typically under 200ms) - Moderate: Docker, Podman (typically 200-300ms)
- Specialized: Firecracker (very fast for micro-VMs), Kata Containers (slower due to VM overhead)
Memory Footprint (Idle)
- Minimal: Buildah, Podman, CRI-O (under 70MB)
- Efficient:
containerd,runC(under 100MB) - Higher: Docker, OpenShift (150MB+)
CPU Efficiency
- Near-Native:
runC, LXC (very little overhead) - Optimized:
containerd, CRI-O, Podman (efficient for most workloads) - Overhead: Docker (due to the daemon), gVisor (due to system call interception)
How to Choose the Right Alternative
Choosing the best Docker alternative depends on your specific needs. Here are some recommendations based on common use cases:
For Security-Focused Environments
- Podman: Best for general-purpose, secure containers due to its rootless design.
- gVisor: Ideal for running untrusted code with an extra layer of isolation.
- Kata Containers: Use when you need the strongest possible isolation, with hardware-level security.
For Kubernetes Production Deployments
containerd: The industry standard, offering a good balance of features and performance.- CRI-O: A minimal and efficient choice if you are running exclusively on Kubernetes.
For Development Workflows
- Rancher Desktop: A great all-in-one GUI tool, especially if you need a local Kubernetes cluster.
- Lima/Colima: Lightweight and simple options for macOS and Linux developers.
- Podman Desktop: A good choice for developers who want a GUI but also prioritize security.
For Performance-Critical Applications
containerd: A high-performance runtime for Kubernetes environments.runC: Offers maximum performance if you are willing to build your own tooling.- LXC: Provides near-native performance for full system containers.
Monitoring Your Container Environment
No matter which container runtime you choose, monitoring is essential for understanding performance, security, and for troubleshooting issues. A modern observability platform can help you collect and analyze metrics, logs, and traces from your entire containerized environment.
Get Started with SigNoz for Container Observability
SigNoz provides comprehensive container monitoring specifically designed for modern containerized environments. Whether you're running Podman, containerd, Kubernetes with CRI-O, or any OCI-compliant runtime, SigNoz offers:
- Multi-Runtime Support: Monitor Docker, Podman, containerd, and Kubernetes environments through unified OpenTelemetry-based instrumentation and dashboards
- Container Performance Metrics: Track CPU utilization, memory consumption, network I/O, and storage performance across all container runtimes with detailed resource analysis
- Rootless Container Monitoring: Full observability support for rootless environments like Podman without compromising security models or requiring elevated privileges
- Kubernetes-Native Integration: Seamless monitoring for containerd, CRI-O, and other Kubernetes runtimes with automatic service discovery and pod-level insights
- Distributed Tracing: End-to-end request tracing across containerized microservices to identify performance bottlenecks and service dependencies
- Custom Alerting: Intelligent alerts based on container resource thresholds, application performance metrics, or custom business logic
For implementation details, explore the SigNoz Docker monitoring guide and Kubernetes monitoring with OpenTelemetry documentation.
You can choose between various deployment options in SigNoz. The easiest way to get started with SigNoz is SigNoz cloud. We offer a 30-day free trial account with access to all features.
Those who have data privacy concerns and can't send their data outside their infrastructure can sign up for either enterprise self-hosted or BYOC offering.
Those who have the expertise to manage SigNoz themselves or just want to start with a free self-hosted option can use our community edition.
Hope we answered all your questions regarding Docker alternatives. If you have more questions, feel free to use the SigNoz AI chatbot, or join our slack community.
Key Takeaways
- Security is Key: Modern alternatives like Podman address major security concerns in Docker by removing the need for a root daemon.
- Kubernetes Has Its Own Needs: Runtimes like
containerdand CRI-O are optimized for Kubernetes and offer better performance in orchestrated environments. - The Best Tool Depends on the Job: The right choice depends on whether you are in development or production, and what your priorities are (e.g., security, performance, ease of use).
- OCI Standards Make Migration Possible: Thanks to the Open Container Initiative, you can use the same container images across different runtimes.
- Plan Your Migration: A successful move to a new tool requires careful planning, testing, and a gradual rollout.
Frequently Asked Questions
What makes Podman more secure than Docker?
Podman is generally considered more secure because it is daemonless and rootless. This means it doesn't require a central service running with root privileges, which reduces the attack surface. Containers run under your user account, so they only have the permissions that you have.
Can I use my existing Docker images with these alternatives?
Yes. Most of the popular alternatives (like Podman, containerd, and CRI-O) are OCI-compliant, which means they can run standard Docker images without any changes.
Which alternative is best for Kubernetes?
containerd is the most common choice and the default for most major Kubernetes services. CRI-O is also an excellent option, as it was designed specifically for Kubernetes and is very lightweight.
How do I handle networking when migrating from Docker?
Networking can be one of the trickier parts of a migration. Podman has a networking stack that is similar to Docker's, but rootless networking can have some limitations. For containerd and CRI-O, networking is typically handled by a CNI plugin, which is standard in Kubernetes.
Is there a performance difference with rootless containers?
Rootless containers have come a long way, and for most workloads, the performance is very similar to rootful containers. There can be some overhead in high-throughput networking scenarios, but this is often a worthwhile trade-off for the improved security.
Are there any licensing costs with these alternatives?
Most of the tools discussed here (Podman, containerd, CRI-O, etc.) are open-source and free to use. Some enterprise platforms like Red Hat OpenShift have commercial licensing and support costs.
How hard is it to migrate my CI/CD pipelines?
This depends on the tool you choose. For Podman, you can often just create an alias (alias docker=podman) and your existing scripts will work. For other tools like Buildah, you may need to modify your build scripts. It is important to test your pipelines thoroughly during the migration.
Which alternative is best for production?
- For Kubernetes production,
containerdor CRI-O are the top choices. - For non-Kubernetes production, Podman is a strong, secure option.
- For enterprise needs, Red Hat OpenShift provides a fully supported platform.
