This guide walks you through installing the sidecar container to collect metrics, traces, and logs from your ECS Serverless infrastructure.
Prerequisites Check
Before starting, verify you have:
- ECS cluster with any launch type (Fargate)
- AWS CLI configured with appropriate permissions
- SigNoz Cloud account or self-hosted SigNoz instance
- Access to AWS Parameter Store and CloudWatch Logs
Installation Steps
Step 1: Create SigNoz OtelCollector Config
The OpenTelemetry Collector configuration defines what data to collect and where to send it.
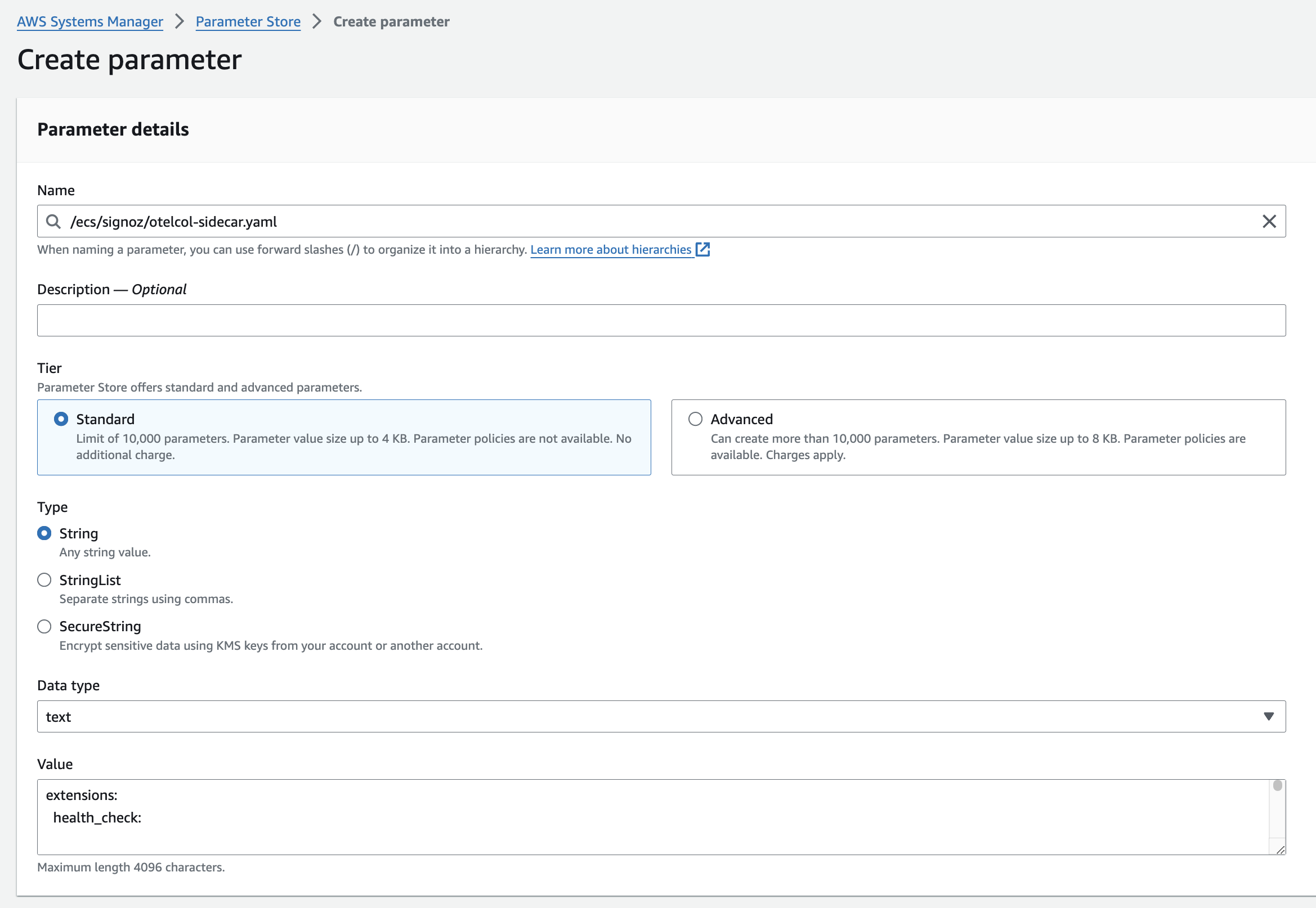
Navigate to AWS Parameter Store and create a new parameter named
/ecs/signoz/otelcol-sidecar.yaml.Copy the following configuration and paste it into the value field of the
/ecs/signoz/otelcol-sidecar.yamlparameter:extensions: health_check: receivers: awsecscontainermetrics: collection_interval: 30s otlp: protocols: grpc: endpoint: 0.0.0.0:4317 http: endpoint: 0.0.0.0:4318 fluentforward: endpoint: 0.0.0.0:8006 processors: batch: timeout: 10s filter: metrics: include: match_type: strict metric_names: - ecs.task.memory.reserved - ecs.task.memory.utilized - ecs.task.cpu.reserved - ecs.task.cpu.utilized - ecs.task.network.rate.rx - ecs.task.network.rate.tx - ecs.task.storage.read_bytes - ecs.task.storage.write_bytes - container.duration exporters: otlp: endpoint: 'ingest.{region}.signoz.cloud:443' headers: 'signoz-ingestion-key': 'SIGNOZ_INGESTION_KEY' service: extensions: [health_check] pipelines: traces: receivers: [otlp] processors: [batch] exporters: [otlp] metrics: receivers: [otlp] processors: [batch] exporters: [otlp] metrics/aws: receivers: [awsecscontainermetrics] processors: [filter] exporters: [otlp] logs: receivers: [otlp, fluentforward] processors: [batch] exporters: [otlp]Update the following placeholders in the YAML configuration:
- Replace
SIGNOZ_INGESTION_KEYwith your SigNoz Cloud ingestion key - Replace
{region}with your SigNoz Cloud region
- Replace
Navigate to AWS Parameter Store and create a new parameter named
/ecs/signoz/otelcol-sidecar.yaml.Copy the following configuration and paste it into the value field of the
/ecs/signoz/otelcol-sidecar.yamlparameter:extensions: health_check: receivers: awsecscontainermetrics: collection_interval: 30s otlp: protocols: grpc: endpoint: 0.0.0.0:4317 http: endpoint: 0.0.0.0:4318 fluentforward: endpoint: 0.0.0.0:8006 processors: batch: timeout: 10s filter: metrics: include: match_type: strict metric_names: - ecs.task.memory.reserved - ecs.task.memory.utilized - ecs.task.cpu.reserved - ecs.task.cpu.utilized - ecs.task.network.rate.rx - ecs.task.network.rate.tx - ecs.task.storage.read_bytes - ecs.task.storage.write_bytes - container.duration exporters: otlp: endpoint: '<IP of machine hosting SigNoz>:4317' tls: insecure: true service: extensions: [health_check] pipelines: traces: receivers: [otlp] processors: [batch] exporters: [otlp] metrics: receivers: [otlp] processors: [batch] exporters: [otlp] metrics/aws: receivers: [awsecscontainermetrics] processors: [filter] exporters: [otlp] logs: receivers: [otlp, fluentforward] processors: [batch] exporters: [otlp]Update
<IP of machine hosting SigNoz>with the address of your SigNoz OTelCollector in the YAML configuration.
Replace <IP of machine hosting SigNoz> with the address of SigNoz OTelCollector.
After successful setup, feel free to remove the logging exporter if it gets too noisy. To do so, simply remove the logging exporter from the exporters list in the following pipelines: traces, metrics, metrics/aws, and logs from the otelcol-sidecar.yaml file.
Step 2: Create Sidecar Collector Container
This step involves integrating the SigNoz collector into your ECS task definitions as a sidecar container. The sidecar collector container will run alongside your application container(s) within the same ECS task and will collect ECS container metrics and send them to SigNoz.
2a. Update Task Definition
In your ECS task definition, include a new container definition specifically for the sidecar container. This container will operate alongside your main application container(s) within the same task definition:
{
...
"containerDefinitions": [
...,
{
"name": "signoz-collector",
"image": "otel/opentelemetry-collector-contrib:0.139.0",
"user": "root",
"command": [
"--config=env:SIGNOZ_CONFIG_CONTENT"
],
"secrets": [
{
"name": "SIGNOZ_CONFIG_CONTENT",
"valueFrom": "/ecs/signoz/otelcol-sidecar.yaml"
}
],
"memory": 1024,
"cpu": 512,
"essential": true,
"portMappings": [
{
"protocol": "tcp",
"containerPort": 4317
},
{
"protocol": "tcp",
"containerPort": 4318
},
{
"containerPort": 8006,
"protocol": "tcp"
}
],
"logConfiguration": {
"logDriver": "awsfirelens",
"options": {
"Name": "forward",
"Host": "127.0.0.1",
"Port": "8006",
"tls": "off"
}
}
}
]
...
}
Avoid defining a healthCheck for the otel-collector container in your ECS task definition. The OpenTelemetry Collector image is based on a minimal base and does not include a shell (/bin/sh or /bin/bash). As a result, any health check command defined in the task definition will fail because AWS ECS attempts to execute it inside the container.
This failure can cause the task to remain in a UNHEALTHY state even when the collector is running correctly.
The sidecar container will run the SigNoz collector and includes essential components like the name ("signoz-collector"), image (e.g., "signoz/signoz-otel-collector:0.88.7"), and command for execution, alongside secrets for secure configuration. It also specifies memory and CPU resources, port mappings for network communication, a health check to ensure operational integrity, and log configuration for output management.
2b. Update ECS Task Execution Role
Your ECS Task Execution Role needs permission to read from SSM Parameter Store and write to CloudWatch Logs.
- Attach
AmazonSSMReadOnlyAccessandCloudWatchLogsFullAccessmanaged policies, or - Add an inline policy that allows
ssm:GetParameterfor your config and CloudWatch Logs actions.
2c. Update ECS Task Role
The ECS Task Role (not the execution role) should also have access to SSM Parameter Store and CloudWatch Logs if your app/sidecar needs it.
- Attach the same managed policies as above, or
- Use a minimal inline policy for just the required resources.
Step 3: Deploy the Task Definition
Deploy your updated ECS task definition as usual (update your service or run a new task). You should see SigNoz sidecar logs in CloudWatch Logs if everything is set up correctly.
Troubleshooting Installation
Common Issues
Task Not Starting:
- Check ECS cluster has available capacity
- Verify the container image can be pulled
- Review CloudWatch logs for the failed tasks
Parameter Store Access Issues:
- Ensure the IAM role has
ssm:GetParameterpermissions - Verify the parameter name matches exactly:
/ecs/signoz/otelcol-sidecar.yaml - Check the parameter is in the same region as your ECS cluster
Container Health Check Failures:
- Verify the health check endpoint is accessible
- Check container logs for any startup errors
- Ensure proper port mappings are configured
