Overview
This guide walks you through setting up SAML (Security Assertion Markup Language) authentication between Okta and SigNoz.
What you'll accomplish:
- Configure Okta as an identity provider (IdP) for SigNoz
- Enable your team to access SigNoz using their existing Okta accounts
Prerequisites
Before starting, ensure you have:
- Okta account with administrative access
- SigNoz account (Cloud or Self-Hosted with License) with administrative access
- Your SigNoz instance URL (e.g.,
https://signoz.example.com)
Configuration Steps
Step 1: Create SAML Application in Okta
- Log in to Okta and create a new SAML application.
Step 2: Configure SAML Settings
- From the Admin page, go to Applications > Applications > Create App Integration
- Select SAML 2.0, and hit Next
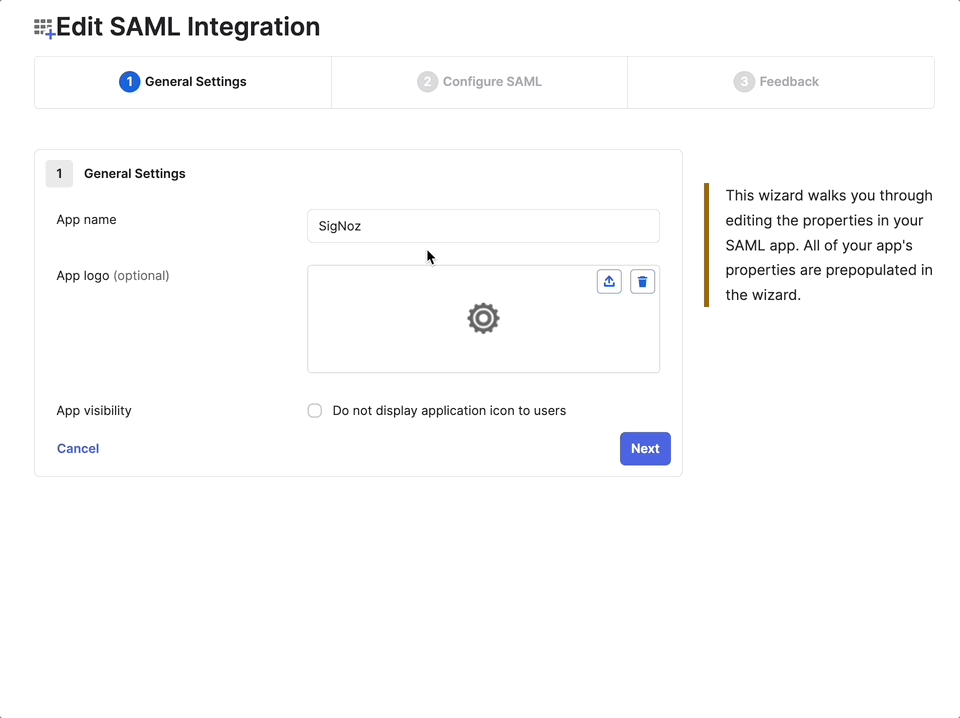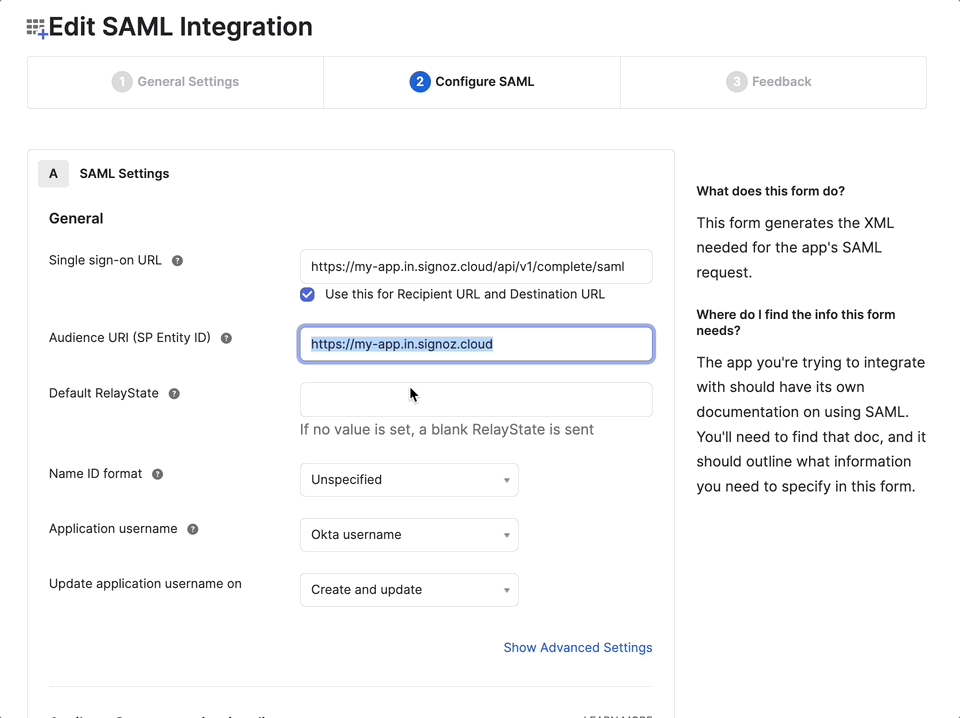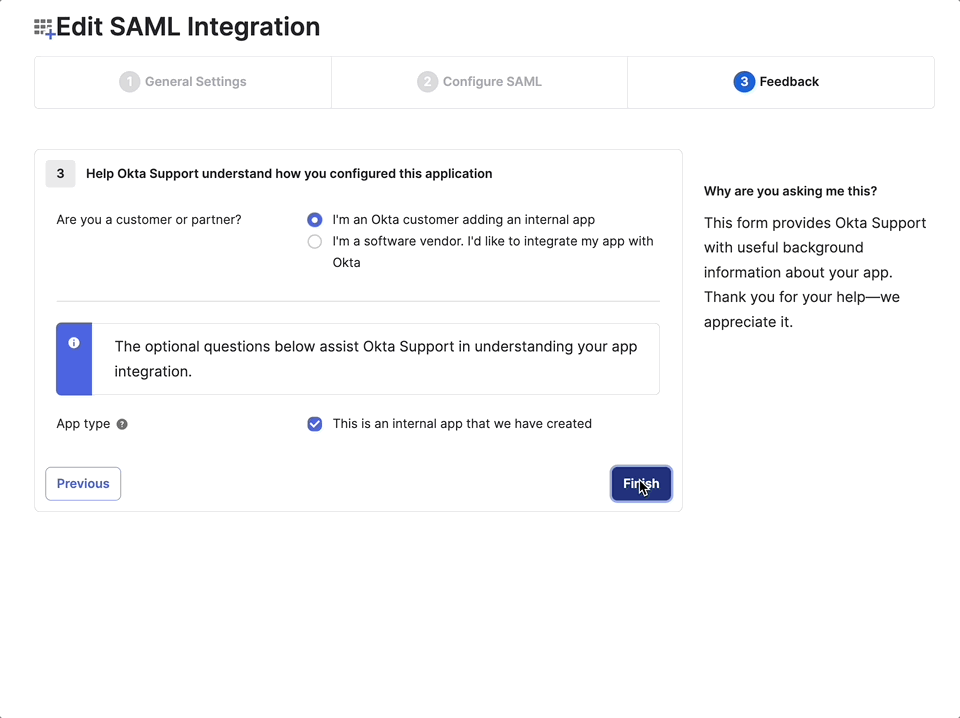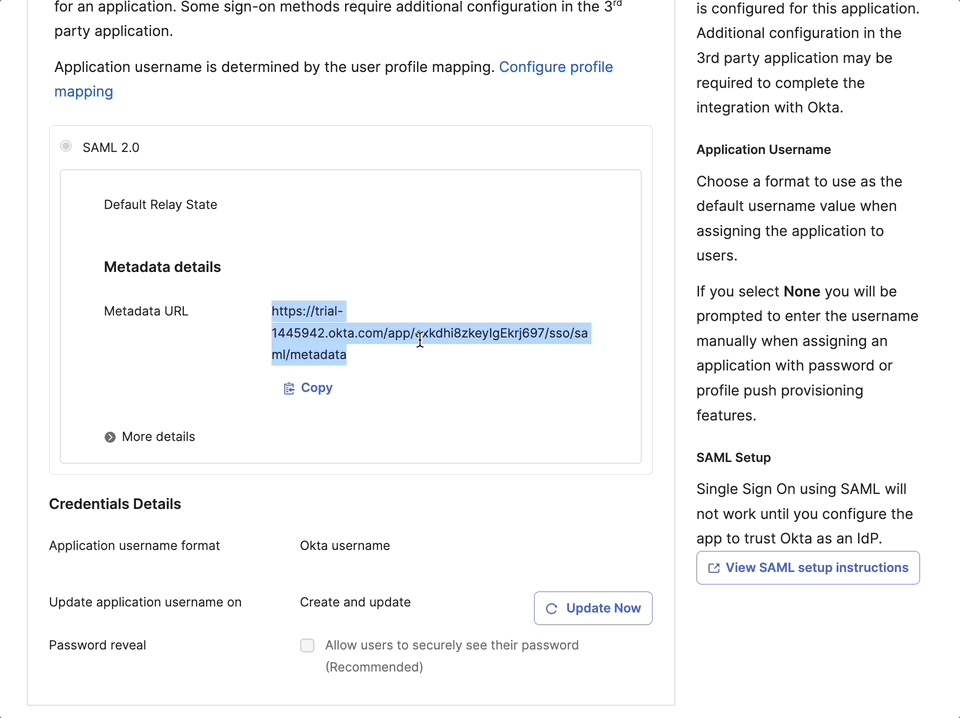
- On the SAML Integration page, enter the following:
- Application Name:
SigNoz - Single Sign-on URL:
<your-instance-url>/api/v1/complete/saml - Audience URI (SP Entity ID):
<your-instance-url>
- Application Name:
- Click Save to create the application integration
Step 3: Export Metadata
- Visit the Metadata URL in Okta to get the following information:
The metadata file contains important configuration details like:
- Okta's signing certificate
- Single Sign-On service URLs
- Entity identifiers
Example metadata file structure:
<md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" entityID="http://www.okta.com/exk...697">
<md:IDPSSODescriptor WantAuthnRequestsSigned="false" protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol">
<md:KeyDescriptor use="signing">
<ds:KeyInfo xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
<ds:X509Data>
<ds:X509Certificate>cert</ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
</md:KeyDescriptor>
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="<idp-url>"/>
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="<idp-url>"/>
<md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified</md:NameIDFormat>
<md:SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="<idp-url>"/>
<md:SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="<idp-url>"/>
</md:IDPSSODescriptor>
</md:EntityDescriptor>
Step 5: Assign Users to Application
- From Admin page, go to Directories > People or Groups
- Select the specific people or groups
- Go to Applications > Assign applications
- Select SigNoz application > Assign > Hit Done
Step 6: Configure SigNoz for SAML Authentication
Now you'll configure SigNoz to accept authentication from Okta:
Navigate to SigNoz Settings:
- Go to your SigNoz dashboard
- Click on Settings in the left sidebar
- Navigate to Organization Settings
- Click on Authenticated Domains
Add New Domain:
- Click Add Domain
- Enter the domain that your users would login with (e.g., if your user emails are in format
john@example.com, enterexample.com)
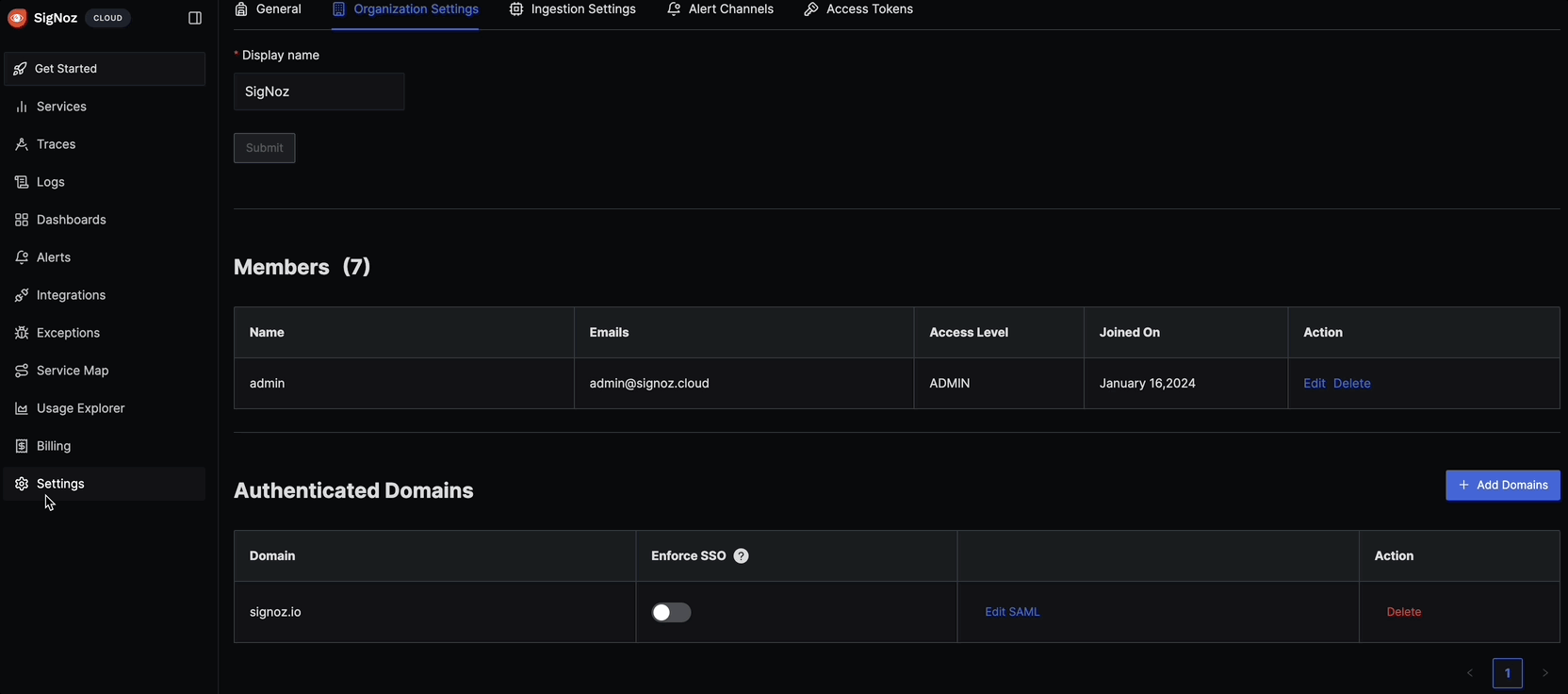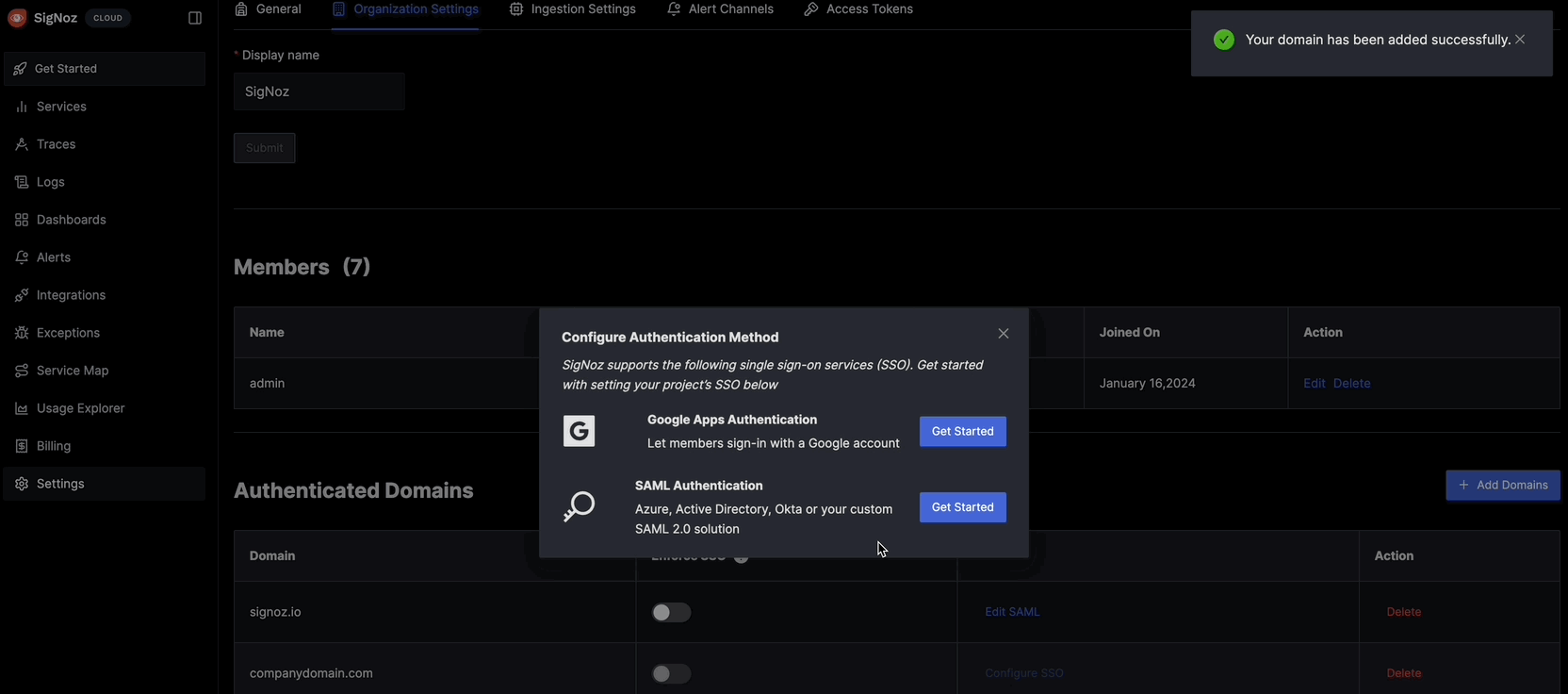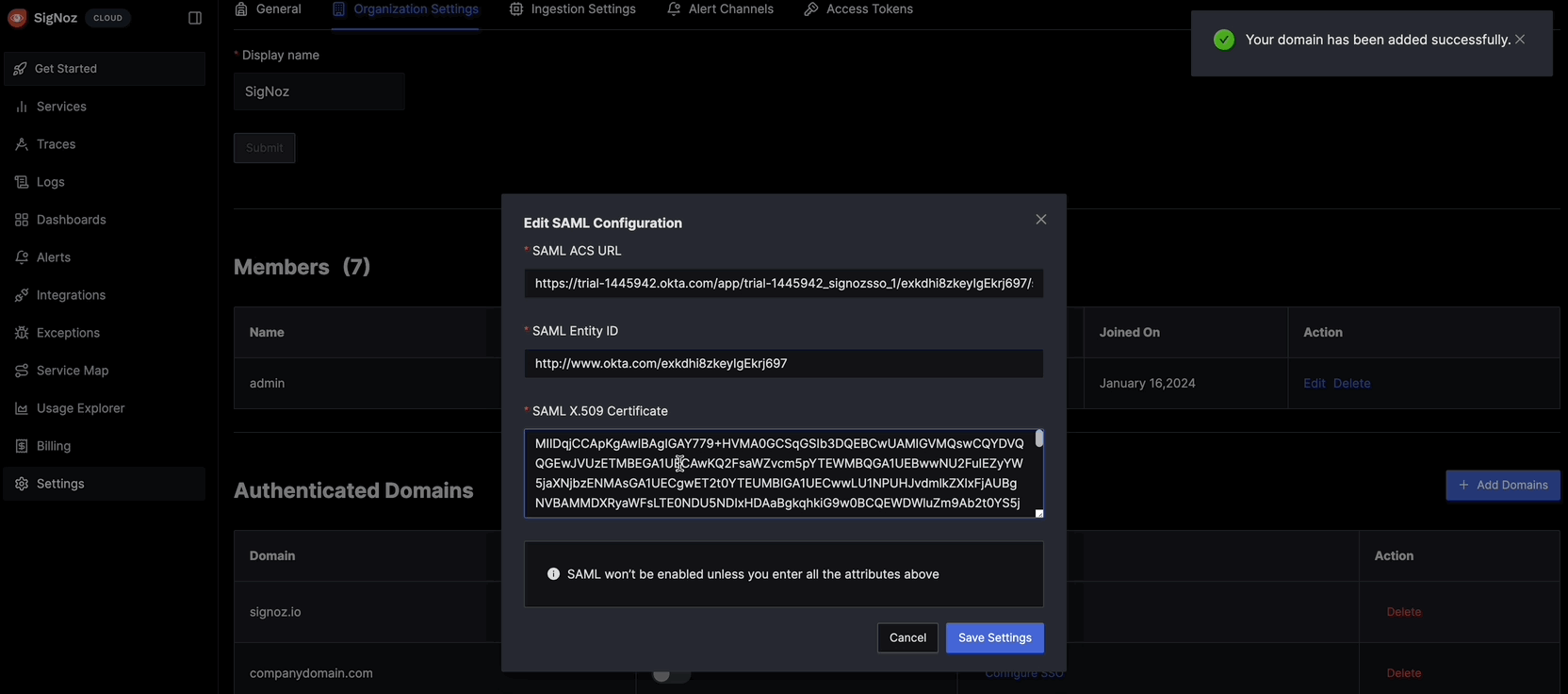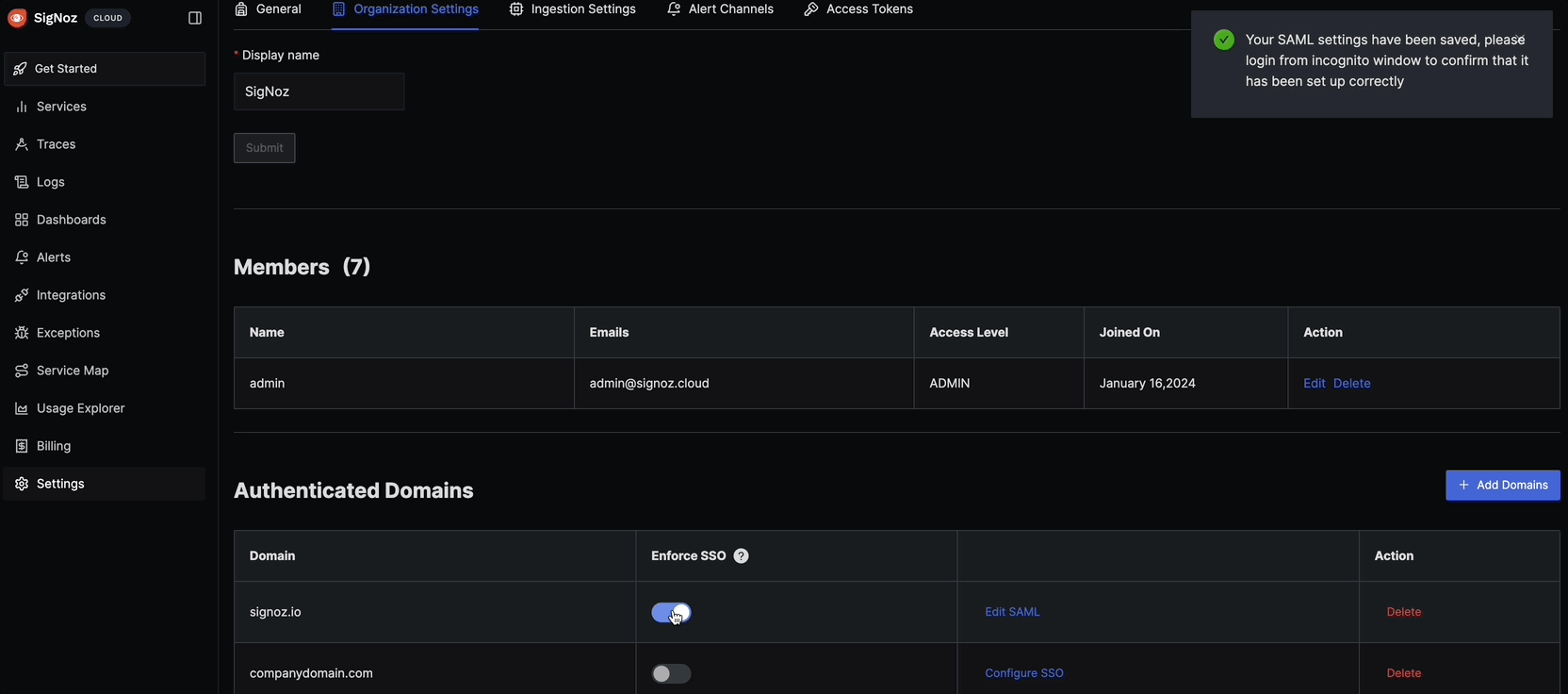
Enter Configuration Details:
Domain: example.com SAML ACS URL/SAML IDP URL: <idp-url> SAML X.509 Certificate: <some-certificate-data> SAML Entity ID: <entity-id> Skip AuthN Requests Signed: FalseWhere to find these values:
- Domain: The email domain for users who should use SSO (e.g.,
example.comfor users with@example.comemails) - SAML ACS URL/SAML IDP URL: The ACS URL from the metadata file (between
<md:SingleSignOnService Location="...">tags) - SAML X.509 Certificate: The certificate content from the metadata file (between
<ds:X509Certificate>tags) - SAML Entity ID: The
entityIDvalue from the metadata file
- Domain: The email domain for users who should use SSO (e.g.,
Save Configuration:
- Click Save to apply the SAML configuration
Step 7: Test the Integration
- Log out of SigNoz if you're currently logged in
- Navigate to your SigNoz login page
- Try logging in with an Okta user email
- Verify that you're redirected to Okta for authentication
- Complete the Okta login process
- Confirm you're successfully logged into SigNoz
Troubleshooting
Common issues and solutions:
- "Authentication failed" error: Check that the redirect URI exactly matches
<your-instance-url>/api/v1/complete/samlin Okta - Locked out?: If you're unable to login because of faulty setup, use password authentication by appending
?password=Yto your login URL:<your-instance-url>/login?password=Y
