How to View Docker Container Logs - A Complete Step-by-Step Guide
Docker containers generate critical telemetry data through their logs, but accessing and analyzing this information efficiently can be challenging without the right approach. Whether you're debugging a failing deployment, monitoring application performance, or investigating security incidents, understanding Docker's logging capabilities is fundamental to maintaining healthy containerized systems.
This guide walks you through Docker container logging from basic commands to production-ready strategies, including integration with observability platforms for comprehensive log analysis.
Understanding Docker's Logging Architecture
Docker captures all output from containerized applications that write to standard output (stdout) and standard error (stderr). This follows the twelve-factor app principle where applications should treat logs as event streams written to the console rather than managing log files internally.
When containers generate output, Docker automatically captures this data using configurable logging drivers. The system stores logs with metadata including timestamps, stream origin (stdout/stderr), and message content. By default, Docker uses the json-file driver, storing logs as JSON-formatted files in /var/lib/docker/containers/<container-id>/<container-id>-json.log.
Important: While json-file remains the default for backward compatibility, Docker now recommends the local driver for production environments. The local driver provides better performance, built-in log rotation, and more efficient disk usage.
Basic Docker Log Commands
Let's start with a practical example. Create a test container to follow along:
docker run -d --name test-nginx nginx:latest
To list all running containers:
docker ps
Viewing Container Logs
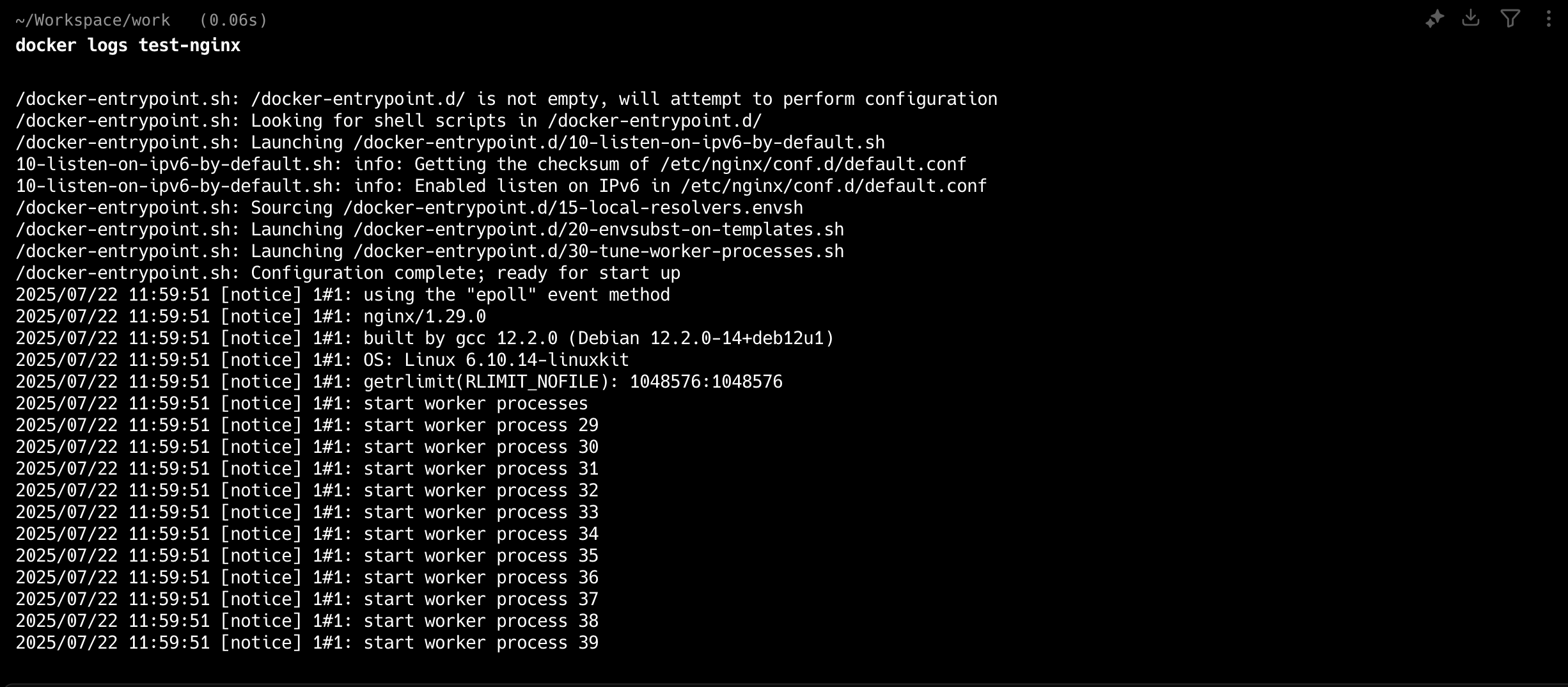
The most basic command retrieves all available logs:
docker logs test-nginx
You can use either container names or IDs:
docker logs 1a2b3c4d5e6f
Real-Time Log Streaming
For active monitoring, use the --follow flag to stream logs as they're generated:
docker logs --follow test-nginx
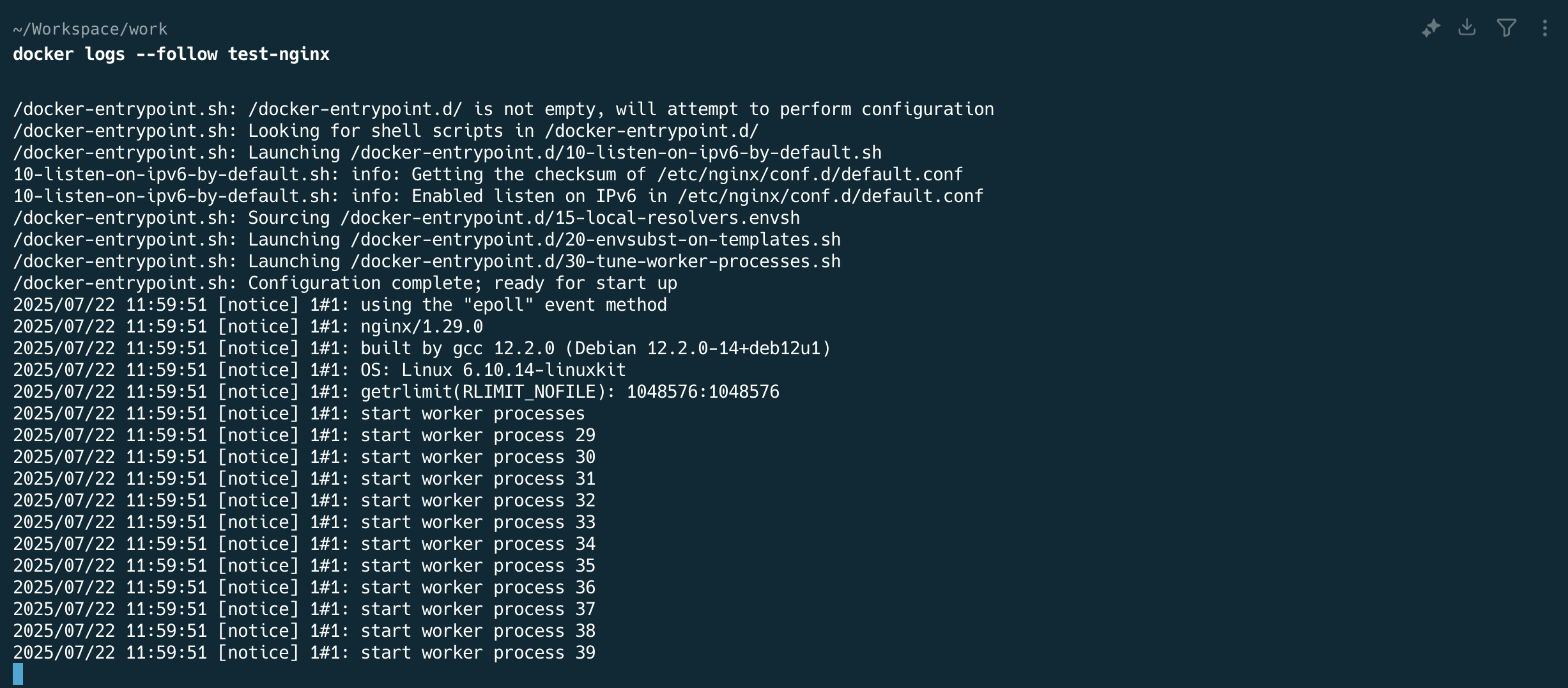
This is essential for troubleshooting active issues or monitoring deployments. Press Ctrl+C to stop streaming.
Limiting Log Output
Use --tail to view only recent entries:
docker logs --tail 50 test-nginx
Combine with --follow for continuous monitoring of recent activity:
docker logs --tail 20 --follow test-nginx
Advanced Log Filtering and Analysis
Docker provides powerful filtering options for precise log analysis, particularly valuable in production environments with high log volumes.
Time-Based Filtering
Filter logs for specific time windows to investigate incidents or analyze patterns:
docker logs --since "2025-01-20T10:00:00" --until "2025-01-20T12:00:00" test-nginx
Docker accepts ISO 8601 timestamps and relative time specifications:
docker logs --since "24h" test-nginx # Last 24 hours
docker logs --since "2h30m" test-nginx # Last 2 hours and 30 minutes
docker logs --since "15m" test-nginx # Last 15 minutes
Pattern Matching and Text Processing
Combine docker logs with Unix text processing tools for powerful analysis:
docker logs test-nginx | grep -i "error" # Case-insensitive error search
docker logs test-nginx | grep -E "(error|warning)" # Multiple patterns
docker logs test-nginx | grep -B 5 -A 5 "timeout" # Context around matches
Chain multiple filters for sophisticated analysis:
docker logs --since "1h" test-nginx | grep "POST" | wc -l # Count POST requests in last hour
Exporting Logs
Save logs for offline analysis or sharing:
docker logs test-nginx > nginx_logs.txt # Save all logs
docker logs --since "24h" test-nginx > recent_logs.txt # Save recent logs
docker logs test-nginx 2>&1 | tee analysis.log # Save while viewing
The 2>&1 redirection captures both stdout and stderr, while tee displays logs on screen while saving to file.
Multi-Container Analysis
For complex applications, analyze logs across multiple containers using Docker Compose:
docker-compose logs # All services
docker-compose logs web database # Specific services
docker-compose logs --tail=100 --follow # Real-time monitoring
Troubleshooting Common Logging Issues
Empty or Missing Logs
Application writes to files instead of console: Many applications log to files inside containers rather than stdout/stderr. Docker only captures console output.
Solution: Configure applications to log to stdout/stderr, or use symbolic links:
# Inside Dockerfile
RUN ln -sf /dev/stdout /var/log/nginx/access.log
RUN ln -sf /dev/stderr /var/log/nginx/error.log
Output buffering: Programming languages often buffer output, preventing immediate log visibility.
Solution: Disable buffering through environment variables:
docker run -e PYTHONUNBUFFERED=1 my-python-app
Incorrect logging driver: Some drivers don't support docker logs command.
Solution: Check the logging driver and enable dual logging if needed:
docker inspect container_name --format='{{.HostConfig.LogConfig.Type}}'
Log Rotation Issues
Insufficient retention: Default settings may rotate logs too aggressively.
Solution: Adjust rotation parameters in /etc/docker/daemon.json:
{
"log-driver": "local",
"log-opts": {
"max-size": "50m",
"max-file": "10"
}
}
No rotation: Some configurations lack proper rotation, leading to disk exhaustion.
Solution: Always configure appropriate log rotation and monitor disk usage.
Permission Problems
Use sudo when necessary or add your user to the docker group (consider security implications):
sudo docker logs container_name
Docker Logging Configuration
Logging Driver Options
json-file (Default): Stores logs as JSON files. Simple but lacks advanced features.
local (Recommended): Optimized file-based driver with better performance, compression, and efficient storage.
syslog: Integrates with system logging services for centralized management.
journald: Forwards logs to systemd journal on supported systems.
fluentd: Routes logs to Fluentd collectors for flexible processing.
awslogs: Directly sends logs to AWS CloudWatch.
Global Configuration
Configure default logging behavior in /etc/docker/daemon.json:
{
"log-driver": "local",
"log-opts": {
"max-size": "25m",
"max-file": "5",
"compress": "true"
}
}
Restart Docker after configuration changes:
sudo systemctl restart docker
Per-Container Configuration
Override defaults for specific containers:
docker run -d \
--log-driver local \
--log-opt max-size=10m \
--log-opt max-file=3 \
--name custom-logs \
nginx:latest
For Docker Compose:
version: '3.8'
services:
web:
image: nginx:latest
logging:
driver: local
options:
max-size: "15m"
max-file: "7"
compress: "true"
Production Best Practices
Storage Management
Monitor Docker log directories and implement alerting:
# Monitor log directory usage
du -sh /var/lib/docker/containers/
# Automated cleanup (use carefully)
find /var/lib/docker/containers/ -name "*-json.log*" -mtime +30 -delete
Configure appropriate rotation balancing retention needs with storage:
{
"log-driver": "local",
"log-opts": {
"max-size": "25m",
"max-file": "5"
}
}
Security Considerations
- Ensure applications don't log sensitive data (passwords, API keys, PII)
- Restrict access to log directories and consider encryption
- Implement clear log retention policies for compliance
Performance Optimization
- Choose appropriate logging drivers based on requirements
- Configure applications with suitable log levels for production
- Use asynchronous logging frameworks to prevent bottlenecks
Centralized Logging Strategy
Standardize log formats: Use structured logging (JSON) for better machine readability:
// Example structured logging
console.log(JSON.stringify({
timestamp: new Date().toISOString(),
level: 'info',
service: 'web-api',
message: 'User authentication successful',
userId: 'user123',
requestId: 'req-456'
}));
Implement correlation: Use correlation IDs to connect related log entries across containers.
Centralized Log Management with SigNoz
For production environments, centralized log management platforms like SigNoz provide advanced analysis capabilities beyond basic Docker logging commands.
SigNoz offers comprehensive log management built on OpenTelemetry standards, providing fast log ingestion, advanced querying, and correlation with metrics and traces in a unified interface.
Key Features for Docker Environments
OpenTelemetry-native collection: Avoids vendor lock-in while supporting extensive log ingestion from Docker containers through the OpenTelemetry Collector.
High-performance storage: ClickHouse-based backend provides fast log analysis capable of handling large volumes with quick query responses.
Advanced query builder: Intuitive interface for searching and filtering logs with dropdown-based filters, aggregations, and mathematical functions for complex analysis.
Setting Up Docker Log Collection
SigNoz collects Docker logs through a pre-configured setup using the OpenTelemetry Collector:
- Clone the repository:
git clone https://github.com/SigNoz/docker-container-logs
- Configure environment variables in the
.envfile:
OTEL_COLLECTOR_ENDPOINT=ingest.<region>.signoz.cloud:443
SIGNOZ_INGESTION_KEY=<your-ingestion-key>
- Start the collector:
docker compose up -d
This setup automatically forwards all Docker container logs to SigNoz with minimal configuration changes to your existing deployments.
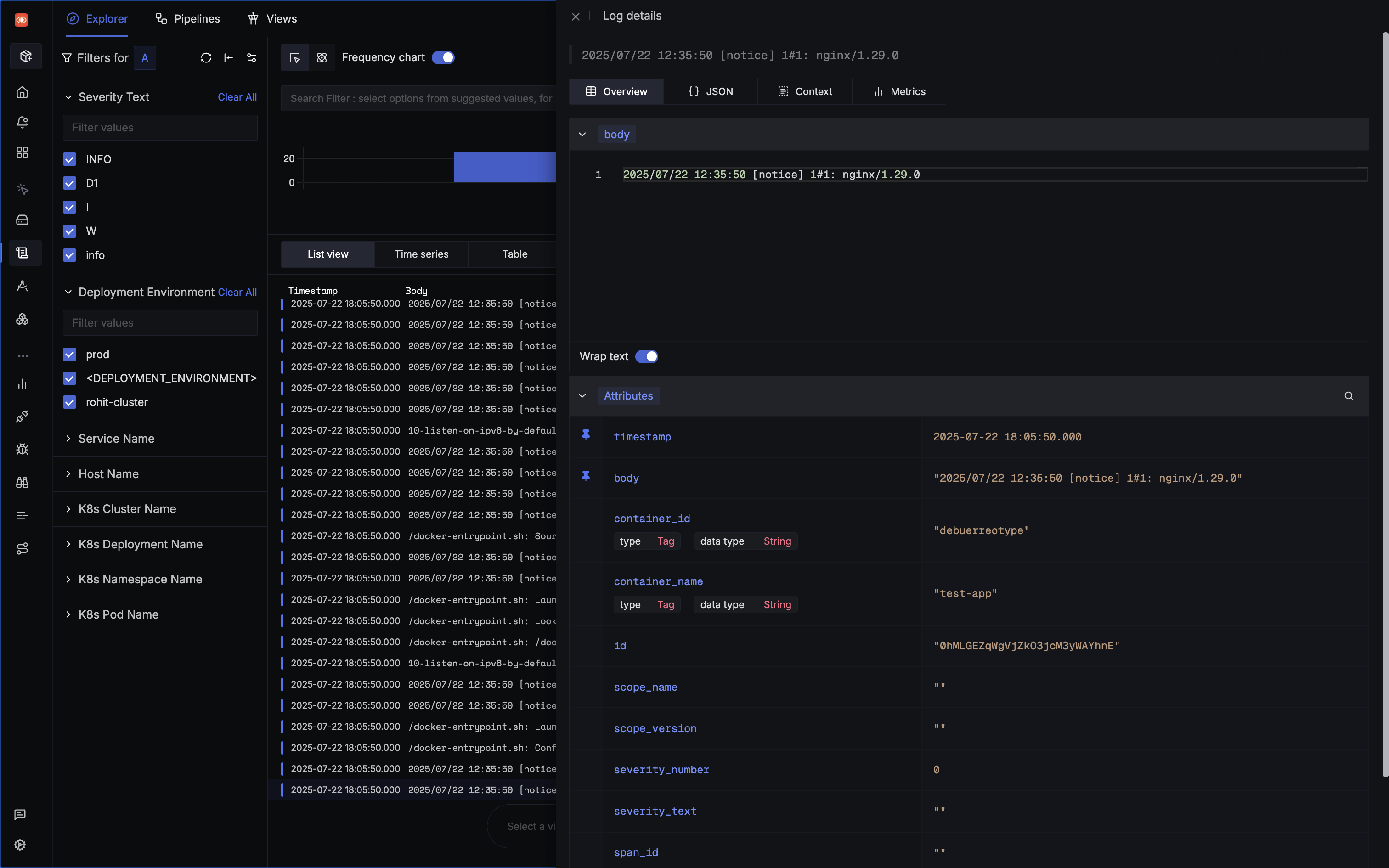
Advanced Capabilities
- Create saved views for common troubleshooting scenarios
- Build custom dashboards correlating logs with metrics and traces
- Set up dynamic alerting based on log patterns
- Use powerful query capabilities with both PromQL and ClickHouse syntax
Get Started with SigNoz
SigNoz provides comprehensive log management capabilities with its advanced query builder for Docker environments. The platform offers fast log ingestion, correlation with metrics and traces, and powerful visualization features.
You can choose between various deployment options in SigNoz. The easiest way to get started with SigNoz is SigNoz cloud. We offer a 30-day free trial account with access to all features.
Those who have data privacy concerns and can't send their data outside their infrastructure can sign up for either enterprise self-hosted or BYOC offering.
Those who have the expertise to manage SigNoz themselves or just want to start with a free self-hosted option can use our community edition.
Hope we answered all your questions regarding Docker container logging. If you have more questions, feel free to use the SigNoz AI chatbot, or join our slack community.
Key Takeaways
Effective Docker logging requires understanding the architecture, using appropriate commands for different scenarios, and implementing production-ready configurations. Key points to remember:
- Use the
localdriver for most production environments - Configure appropriate log rotation to prevent storage issues
- Implement structured logging with correlation IDs for better analysis
- Consider centralized logging solutions like SigNoz for advanced capabilities
The combination of Docker's native logging capabilities with advanced observability platforms provides comprehensive visibility into your containerized applications, enabling faster troubleshooting and better operational insights.
