SNMP Monitoring - A Comprehensive Guide for Network Admins
SNMP monitoring forms the backbone of effective network management. As a network admin, you must understand this protocol to maintain optimal network performance. This guide delves into the intricacies of SNMP monitoring, covering everything from its basic principles to advanced implementation techniques.
What is SNMP Monitoring?
Simple Network Management Protocol (SNMP) is a standardized method for monitoring and managing network devices. It enables network admins to collect data from various network components—routers, switches, servers, and more.
SNMP is pivotal in network management because it monitors network performance, detects faults, and ensures smooth operation of network devices.
SNMP (Simple Network Management Protocol) is used to collect data from network devices like routers, switches, and servers. The collected data is then used to monitor and manage these devices to ensure network health and performance.
.webp)
SNMP Monitoring
SNMP's history dates back to 1988 when it was introduced to address the growing complexity of network management. Since then, it has evolved through several versions, each improving on its predecessor's capabilities and security features.
Key Benefits of Implementing SNMP Monitoring
- Proactive Network Management: Early detection of issues helps in preventing network downtime.
- Efficient Resource Utilization: Real-time data collection aids in optimal resource allocation.
- Enhanced Security: SNMPv3 provides robust security features, ensuring secure data transmission.
- Scalability: SNMP supports a vast array of devices, making it scalable for large networks.
How SNMP Monitoring Works: A Deep Dive
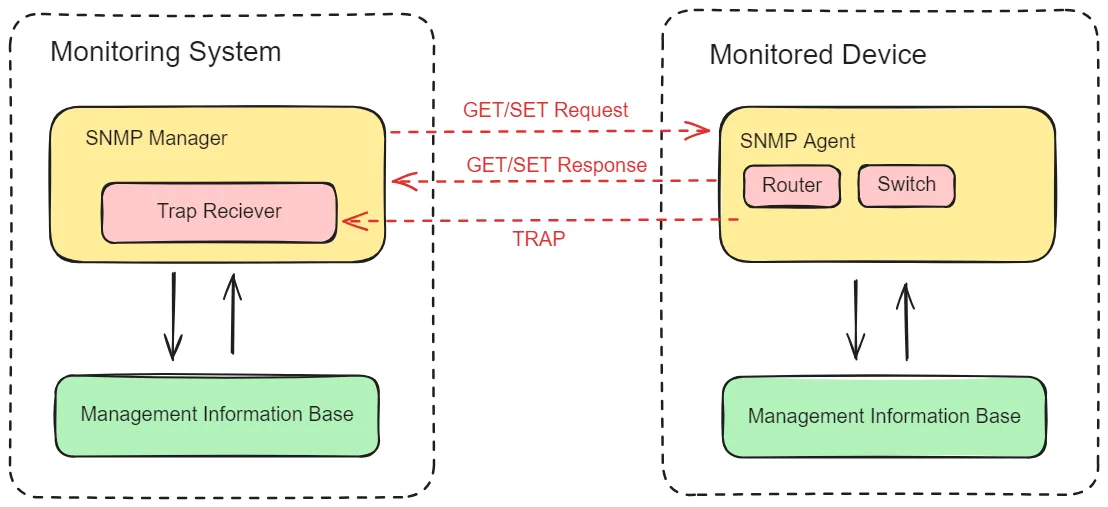
SNMP (Simple Network Management Protocol) operates on a manager-agent model, designed to facilitate efficient network management and monitoring. This model consists of three primary components:
- SNMP Manager: This central system collects and processes data from various network devices. It serves as the command center for network monitoring, where data from different sources is aggregated and analyzed.
- SNMP Agents: These are software modules installed on network devices (such as routers, switches, and servers). Agents are responsible for gathering data about the device’s performance and status and transmitting this information to the SNMP Manager.
- Management Information Base (MIB): The MIB is a hierarchical database that defines the structure of management data. It serves as a reference model, outlining how data is organized and accessed. The MIB allows the SNMP Manager to interpret the data collected by the SNMP Agents accurately.
SNMP Operations
SNMP relies on three primary operations to manage and monitor network devices:
- GET: This operation retrieves specific information from a device. For example, if the SNMP Manager needs to check the CPU usage of a network router, it sends a GET request to the router’s SNMP Agent.
- SET: The SET operation allows the SNMP Manager to modify device settings or configurations. This can be used to change configurations, such as adjusting network thresholds or updating device settings.
- TRAP: Unlike GET and SET, TRAP allows devices to send unsolicited notifications to the SNMP Manager. This means that the SNMP Agent can alert the Manager about significant events or issues, such as a sudden increase in network traffic or a device failure.
The overall working of SNMP monitoring can be understood using the architecture diagram below:
SNMP Data Organization
Data in SNMP is organized using Object Identifiers (OIDs). These are unique numerical strings that represent specific attributes or variables of a device. For instance, an OID might represent the number of packets transmitted or the amount of free memory on a device.
OIDs are crucial for querying and interpreting SNMP data accurately. They enable the SNMP Manager to request specific pieces of information from the SNMP Agents and ensure that the data retrieved is precise and relevant.
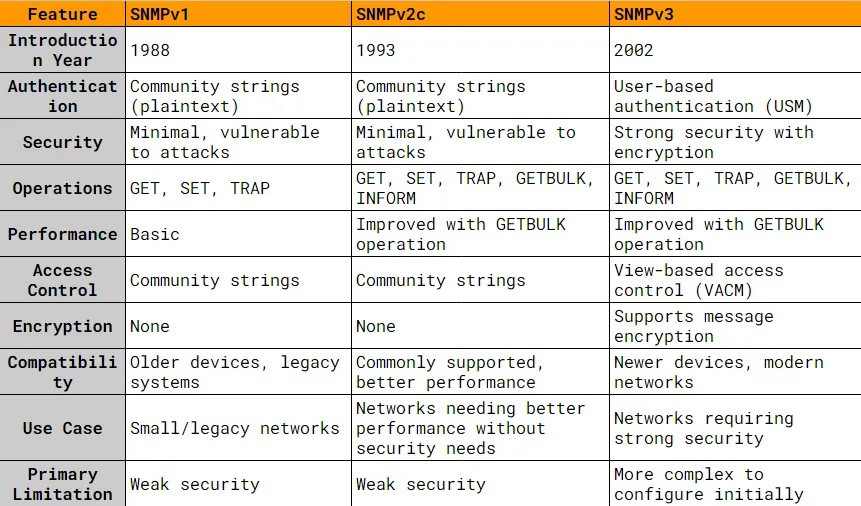
SNMP Versions Compared: v1, v2, and v3
SNMP has evolved significantly since its inception. Here's a comparison of the three main versions:
SNMPv1
SNMPv1, the original version of SNMP, was introduced in 1988. It provided a basic framework for network management and monitoring.
Key Features:
- Simple Authentication: Utilizes community strings for authentication, which are essentially passwords sent in plaintext.
- Basic Operations: Supports basic operations such as GET, SET, and TRAP.
- Limited Security: Due to its plaintext community strings, SNMPv1 has minimal security features and is vulnerable to eavesdropping and unauthorized access.
Use Case: Primarily used in small, less security-sensitive networks or legacy systems that do not support newer versions.
SNMPv2c
SNMPv2, introduced in 1993, aimed to improve upon the limitations of SNMPv1. The most commonly used variant is SNMPv2c, which stands for "Community-Based Simple Network Management Protocol Version 2."
Key Features:
- Enhanced Operations: Introduces new operations such as GETBULK for efficient data retrieval and INFORM for acknowledging receipt of TRAP messages.
- Improved Performance: GETBULK operation reduces the number of requests needed to retrieve large amounts of data, enhancing performance.
- Still Uses Community Strings: Continues to use community strings for authentication, similar to SNMPv1, which means it still lacks strong security measures.
Use Case: Suitable for environments where performance improvements are needed but where security is not a critical concern, or where upgrading to SNMPv3 is not feasible.
SNMPv3
SNMPv3, released in 2002, focuses on addressing the security shortcomings of its predecessors. It incorporates robust security features, making it the most secure and preferred version for modern networks.
Key Features:
- User-Based Security Model (USM): Provides authentication and privacy through encryption and user-based access control.
- View-Based Access Control Model (VACM): Allows fine-grained control over access to MIB objects, ensuring that only authorized users can view or modify specific data.
- Message Integrity and Encryption: Ensures that messages are not tampered with during transit and that sensitive information is protected from eavesdropping.
Use Case: Recommended for most modern networks, especially those requiring stringent security measures. Ideal for enterprises and organizations that need to protect sensitive network management data.
Choosing the Right SNMP Version for Your Network
- Security Needs: If security is a primary concern, SNMPv3 is the clear choice due to its encryption and authentication capabilities.
- Device Compatibility: Evaluate the devices in your network. If some only support SNMPv1 or SNMPv2c, you may need to accommodate them, possibly using a mixed environment.
- Performance Requirements: SNMPv2c may be preferred in environments where performance improvements are needed but security is less critical.
When choosing an SNMP version, consider your network's security requirements and the compatibility of your devices. For most modern networks, SNMPv3 is recommended due to its enhanced security features.
Security Considerations in SNMP Monitoring
Security is a critical aspect of SNMP monitoring due to the sensitive nature of the data being transmitted. Some of the key security measures include.
- Community Strings: Used in SNMPv1 and SNMPv2c for basic authentication. They are like passwords and should be configured securely.
- Encryption: Supported in SNMPv3, ensuring that data in transit is secure.
- Access Control: Implemented using Access Control Lists (ACLs) and View-based Access Control Model (VACM) in SNMPv3.
- User-based Security Model (USM): Used in SNMPv3 for strong authentication and privacy.
SNMPv3 offers significant security improvements with user-based authentication, encryption, and access control, addressing the vulnerabilities present in SNMPv1 and SNMPv2c.
Essential SNMP Metrics for Comprehensive Network Monitoring
SNMP allows you to monitor a wide range of network metrics. Here are some essential ones:
- CPU usage: Tracks processor utilization across devices
- Network interface statistics: Monitors data throughput, errors, and discards
- Memory utilization: Keeps tabs on available and used memory
- Disk space: Alerts you to storage capacity issues
- Environmental metrics: Monitors temperature, fan speeds, and power supply status
.webp)
SNMP metrics for network monitoring
By tracking these metrics, you can preemptively identify potential issues and optimize network performance.
Implementing SNMP Monitoring: Best Practices
Listed below are some of the best practices for setting up effective SNMP monitoring:
- Enable SNMP agents on all network devices
- Configure SNMP managers with appropriate polling intervals
- Establish secure SNMP communities or user accounts
- Implement access control lists (ACLs) to restrict SNMP traffic
- When troubleshooting SNMP issues:
- Verify network connectivity between the manager and agents
- Check SNMP community strings or authentication credentials
- Ensure firewall rules allow SNMP traffic
- Review device logs for SNMP-related errors
SNMP Monitoring Tools
As networks grow in complexity and size, the task of monitoring and managing all connected devices becomes increasingly challenging. Manual monitoring is not only impractical but also prone to errors and oversight. This is where SNMP monitoring tools come into play, providing automated and comprehensive oversight of your network's health and performance.
There are various SNMP monitoring tools available to help network administrators.
- Nagios: Offers comprehensive monitoring with extensive plugin support.
- Zabbix: Provides a scalable monitoring solution with SNMP support.
- PRTG Network Monitor: User-friendly interface with SNMP monitoring capabilities.
- SolarWinds: A robust suite of network management tools including SNMP monitoring.
While these tools provide a solid foundation for SNMP monitoring, there are advanced techniques that can further enhance your monitoring strategy.
Advanced SNMP Monitoring Techniques
You can use the advanced techniques listed below to take your SNMP monitoring to the next level:
- Automated device discovery: Use SNMP to scan your network and automatically add new devices to your monitoring system.
- SNMP traps for proactive alerting: Configure devices to send SNMP traps when specific events occur, enabling faster response times.
- Capacity planning: Analyze long-term SNMP data trends to forecast future network needs and plan upgrades accordingly.
- Integration with other protocols: Combine SNMP with protocols like NetFlow or sFlow for more comprehensive network visibility.
Enhancing SNMP Monitoring with Modern Observability Tools
While SNMP is a fundamental protocol for network monitoring, it has its limitations, especially in today’s complex and distributed environments. To address these gaps, modern observability tools offer additional capabilities that complement SNMP monitoring:
- Distributed Tracing: Allows you to track requests as they traverse through multiple services and microservices, providing deeper insights into application behavior and interactions.
- Real-time Analytics: Delivers immediate insights into both network and application performance, enabling quick identification and resolution of issues.
- Advanced Visualization: Converts complex data into user-friendly visual formats, making it easier to interpret and act upon network and application metrics.
SigNoz, an open-source observability platform, is an excellent example of how these modern tools can enhance traditional SNMP monitoring. By integrating end-to-end visibility into applications and infrastructure, SigNoz complements SNMP’s device-level data with comprehensive service-level performance insights.
SigNoz Cloud is the easiest way to run SigNoz. Sign up for a free account and get 30 days of unlimited access to all features.
You can also install and self-host SigNoz yourself since it is open-source. With 24,000+ GitHub stars, open-source SigNoz is loved by developers. Find the instructions to self-host SigNoz.
You can leverage the power of SigNoz alongside SNMP, you gain a more holistic view of your network and applications.
Key Takeaways
- SNMP monitoring is essential for effective network management
- Understanding SNMP versions helps in choosing the right security level for your network
- Proper configuration and security measures are crucial for SNMP implementation
- Combining SNMP with modern observability tools like SigNoz provides comprehensive network insights
FAQs
What are the main differences between SNMP v2c and v3?
SNMPv2c improves on v1 with better performance and the GetBulk operation. SNMPv3 adds significant security enhancements, including encryption and user-based authentication.
How can I secure SNMP communications in my network?
Use SNMPv3 with its built-in security features, implement strong passwords or community strings, restrict SNMP access using ACLs, and consider using a separate management VLAN for SNMP traffic.
What are some alternatives to SNMP for network monitoring?
Alternatives include NetFlow, sFlow, RMON, and newer protocols like NETCONF and RESTCONF. However, SNMP remains widely supported and is often used alongside these technologies.
How does SNMP monitoring impact network performance?
SNMP typically has minimal impact on network performance when configured correctly. However, excessive polling or poorly optimized MIBs can increase network load. Monitor SNMP traffic and adjust polling intervals as needed to balance monitoring needs with performance.
