Graylog vs Loki - Choosing the Right Log Management Tool
Log management is a crucial aspect of modern software observability. As your systems grow in complexity, choosing the right log management solution can significantly impact performance, cost, and reliability. This article dives into two popular open-source solutions: Graylog and Loki. We'll explore their technical foundations, compare their features, and help you make an informed decision for your log management needs.
Quick Guide: Comparing Graylog and Loki
Here's a detailed comparison table showcasing the key differences between Graylog and Loki:
| Aspect | Graylog | Loki |
|---|---|---|
| Core Difference | Built around Elasticsearch/OpenSearch for storing logs; uses Lucene-based query language; ideal for traditional enterprise log analysis. | Uses a label-based indexing system (inspired by Prometheus); optimized for cloud-native and containerized environments. |
| Use Case Snapshot | Complex enterprise environments requiring advanced dashboards, robust alerting, and large-scale indexing across multiple data types. | Cloud-native applications, Kubernetes-based deployments, and environments prioritizing cost-efficient storage and scalability. |
| Deployment Complexity | Requires setting up Graylog server(s), Elasticsearch/OpenSearch, and MongoDB; resource-intensive but powerful for complex analyses. | Involves installing Loki alongside Promtail, Fluentd, or other log shippers; streamlined for cloud environments. |
| Performance & Resource Usage | High I/O and compute usage depending on Elasticsearch indexing; scales well but can be resource-intensive. | Efficient chunk-based storage; scales horizontally with minimal overhead; excels with ephemeral log sources (e.g., containers). |
| Scalability | Designed for horizontal scalability; adding more Graylog nodes can handle increased log volumes. | Highly scalable by leveraging distributed object storage and distributed query processing; suitable for handling large volumes of log data. |
| Integration | Supports various log collection methods like syslog, GELF, and Beats; integrates with multiple data sources and destinations. | Primarily relies on log streaming agents like Promtail; integrates seamlessly with the Grafana ecosystem and other tools like Prometheus. |
| User Interface | Offers a user-friendly interface with advanced search capabilities; customizable dashboards for visualizing log data. | Provides a simplified query language inspired by PromQL; integrates with Grafana for visualization, offering a unified observability experience for metrics and logs. |
In the following discussion, we'll take a closer look at the components and features of Graylog and Loki.
What Are Graylog and Loki?
Before we dive into the comparison, let's get a quick overview of each tool.
Graylog Overview
Graylog is a centralized log management system designed for processing, storing, and analyzing log data from various sources. It provides powerful search capabilities using Lucene-based query language and supports robust alerting and dashboards for enterprise-grade log monitoring.
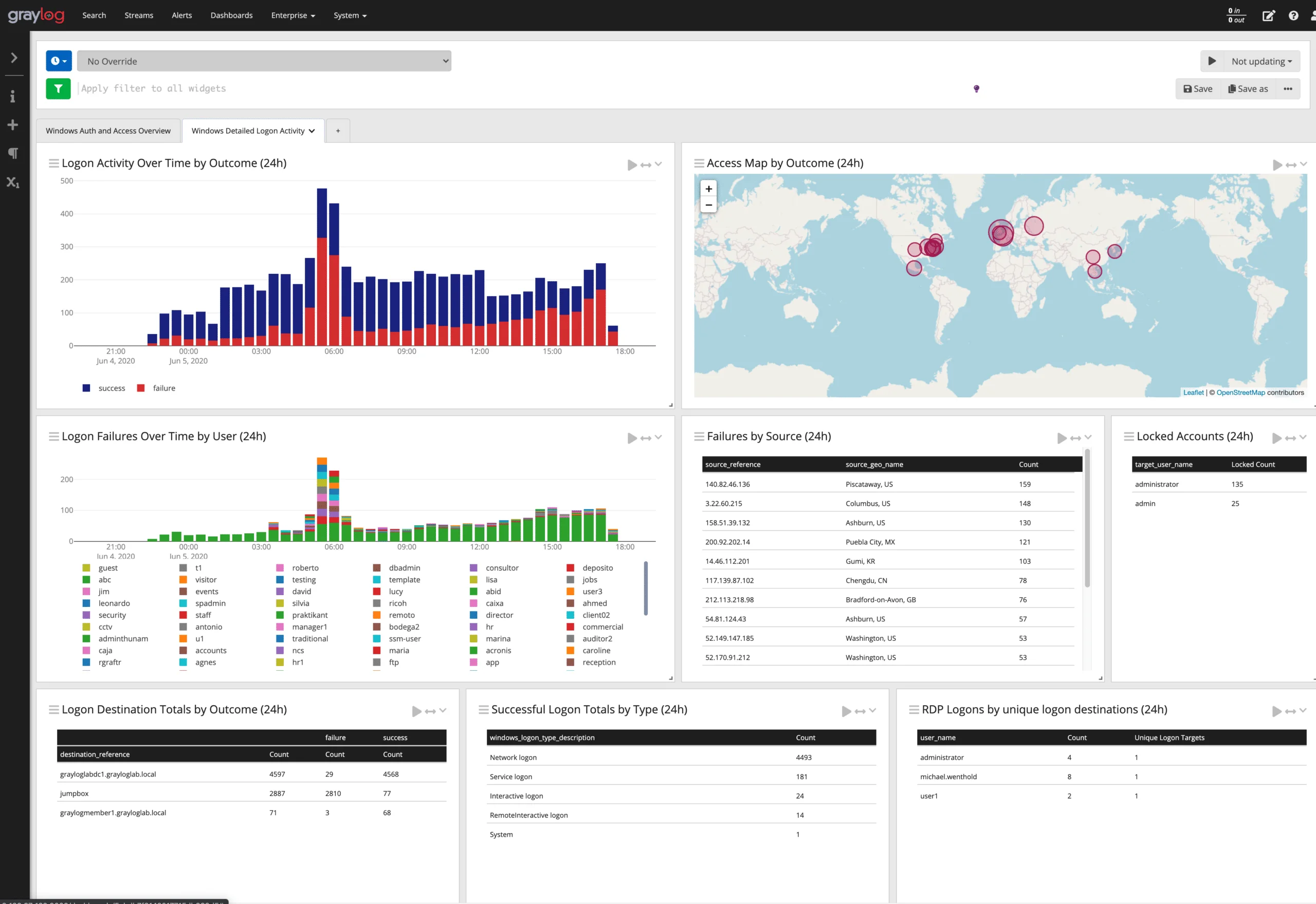
Architecture:
Think of Graylog as a traditional library system in a large institution:
- Graylog Server: Acts like the librarian, managing log data and helping users search for specific entries.
- MongoDB: This is the catalog where the librarian keeps track of the library's inventory and organizational details.
- Elasticsearch/OpenSearch: Functions like the shelves holding all the books (logs). It's highly organized with detailed indexing, so the librarian can quickly locate any book based on content, title, or author.
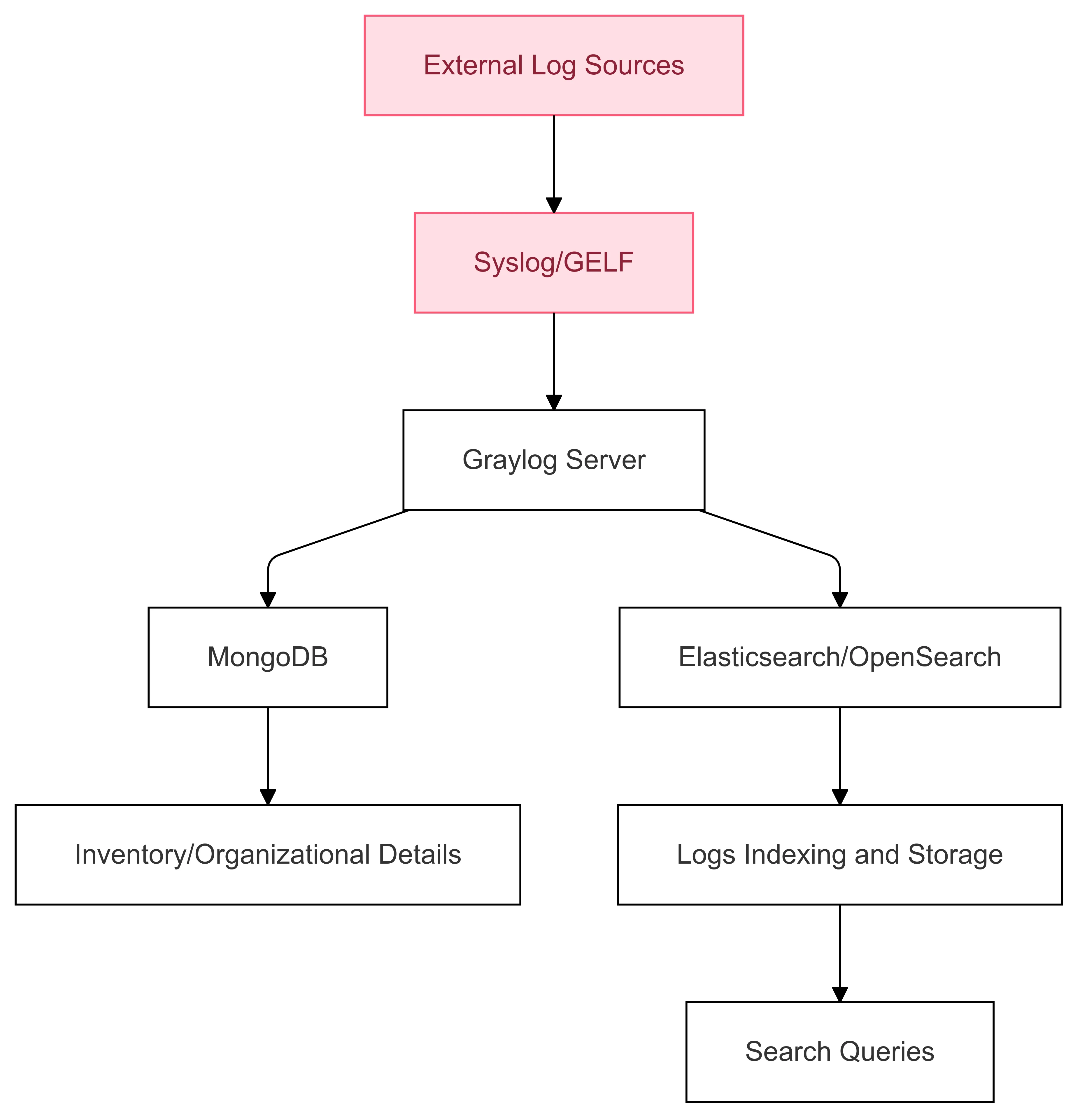
This diagram shows:
- Graylog Server: Acts as the main component, responsible for handling the log data and managing search and alerts.
- MongoDB: Manages metadata and organizational details.
- Elasticsearch/OpenSearch: Handles the actual log data storage and indexing, enabling efficient searches.
- Syslog/GELF: Represents the external log sources that feed data into Graylog for processing and analysis.
Key Features:
- Centralized Log Collection: Like gathering all books in one library to simplify access.
- Lucene-based Search Syntax: Imagine being able to search not just for "Shakespeare" but for "books mentioning Hamlet in the first 10 pages."
- Lucene is an open-source library for indexing and searching text. In Graylog, Lucene-based search allows efficient indexing and quick retrieval of log data using complex queries, similar to how a library index helps find books.
- Versatile Input Types: Accepts books (logs) from diverse sources, whether old manuscripts (syslog) or modern PDFs (GELF).
- Syslog acts like a messenger that delivers log data from different sources to a central location for storage and analysis.
- Alerting: The librarian can send an alert if a book gets misplaced or if someone tries to borrow a restricted item.
Loki Overview
Loki is a lightweight, cloud-native log aggregation system inspired by Prometheus. It emphasizes efficient storage and querying of log data using a label-based indexing system, making it ideal for containerized and ephemeral environments.
Architecture:
Imagine Loki as a cloud-based e-library tailored for fast-moving tech hubs:
- Distributor: Like an online portal where users upload new e-books (logs).
- Ingester: Converts e-books into compact formats and stores them efficiently.
- Querier: The search engine that helps users find specific books using tags (labels).
- Object Storage: Instead of traditional shelves, books are stored in cloud storage services like Google Drive or Amazon S3.
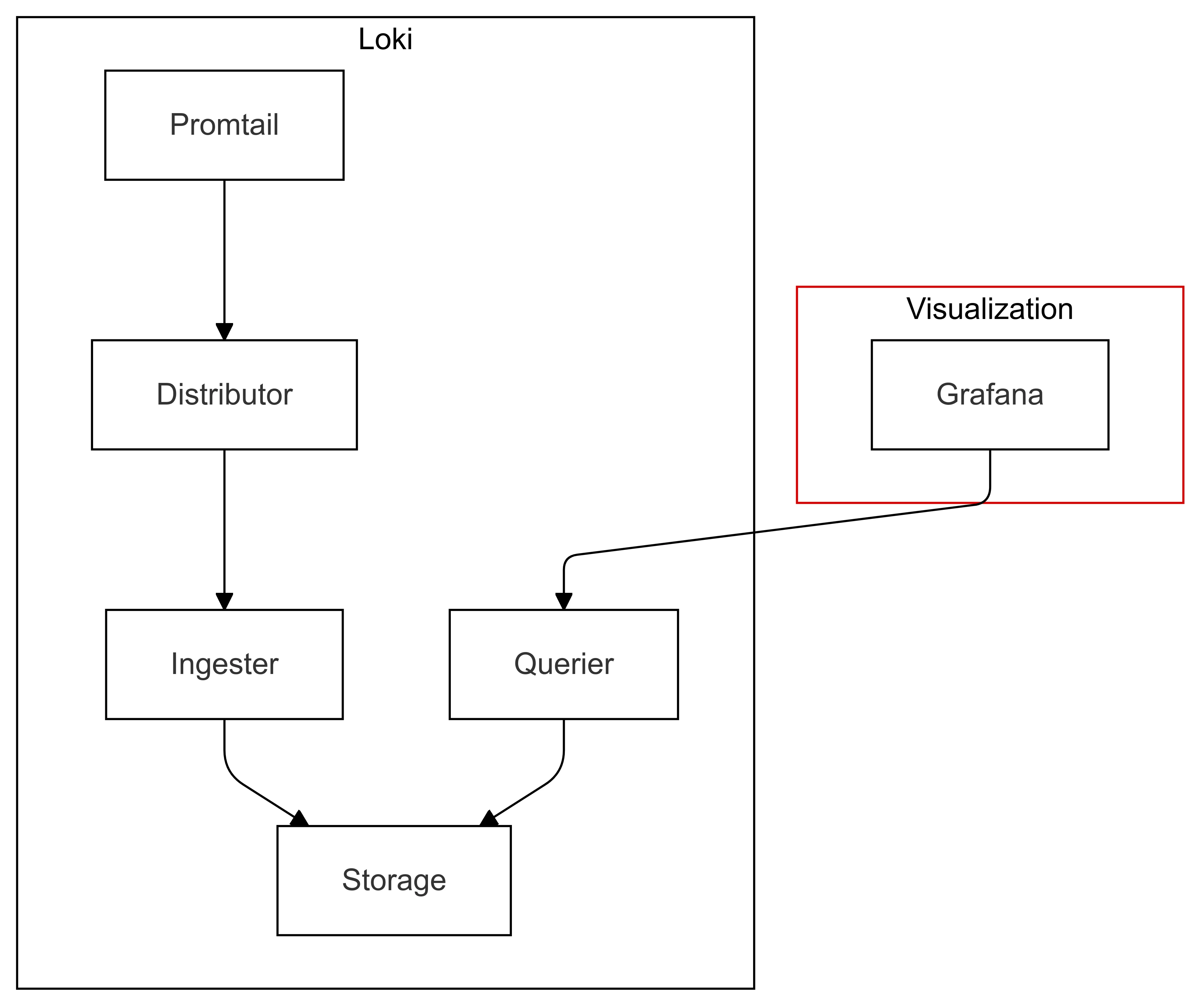
This diagram shows:
- Promtail: An agent that collects logs from various sources and forwards them to the Distributor.
- Distributor: Validates and distributes log data to the appropriate Ingester.
- Ingester: Processes and stores log data temporarily before persisting it to long-term storage.
- Storage: Long-term storage for log data, such as object storage systems.
- Querier: Handles queries from Grafana, retrieving data from both Ingester and Storage.
- Grafana: Provides visualization and querying capabilities for the log data stored in Loki.
Key Features:
- Label-based Filtering: Instead of reading every book, you find e-books based on their tags—like filtering for "Mystery" or "2023 releases."
- Efficient Storage: E-books are compressed into small chunks, saving space compared to physical libraries.
- Designed for Containers: Perfect for startups or workplaces where "books" (logs) are created and deleted quickly, as in ephemeral infrastructures.
Comparing Graylog and Loki: Core Functionalities
The fundamental difference between Graylog and Loki lies in their approach to log storage and indexing:
- Graylog: Uses Elasticsearch/OpenSearch for full-text indexing, which enables powerful search capabilities but can be resource-intensive.
- Loki: Employs a label-based indexing system, focusing on efficient storage and querying—ideal for cloud-native environments.
This core difference influences various aspects of each tool's performance, scalability, and use cases.
1. Log Ingestion Methods
How you get logs into your management system is crucial. Let's compare the ingestion methods for both tools:
Graylog Ingestion
Protocols Supported: Graylog is versatile when it comes to ingesting log data. It supports several protocols such as:
- Syslog: A standard logging protocol used to send event messages over a network. It's commonly used by various systems and devices.
- Beats: A collection of lightweight data shippers for forwarding logs. This includes Filebeat (for file logs), Metricbeat (for system metrics), and others.
- GELF (Graylog Extended Log Format): Graylog's own format designed for structured logging with advanced features like support for compression and batch processing.
- Other protocols: Graylog also supports various input plugins for different log formats and sources.
Log Collection: Graylog usually uses sidecar collectors (lightweight agents running alongside applications) or input plugins to collect logs from hosts. These sidecars or agents send logs from different systems or services into the Graylog server.
Real-World Example: Graylog Setup for Netflix-Style Streaming Service: Used for capturing high-volume events with detailed search and analytics requirements.
- User Authentication Logs: Handles ~500K events/day, collected via Beats, providing insights into login patterns or suspicious access attempts.
- Video Playback Events: Processes ~2M events/day, parsed using custom extractors to analyze playback quality metrics like buffering or resolution.
- CDN Logs: Ingests ~5M events/day to monitor content delivery performance, network latency, and regional access statistics.
Graylog excels in diverse log ingestion methods with rich protocol support, making it ideal for complex enterprise environments.
Loki Ingestion
Loki typically relies on dedicated log shippers:
- Log Shipping with Promtail: Loki, on the other hand, uses Promtail or other log shippers like Fluentd or Fluent Bit. These tools are responsible for scraping logs, adding labels (metadata), and sending them to Loki.
- Label-Based Indexing: Instead of fully indexing every log line, Loki uses labels (such as log source, log level, container name, etc.) to index the logs. This makes Loki more efficient with large volumes of ephemeral logs (especially in containerized environments) since labels are lightweight and faster to process.
- Real-World Example: Loki Setup for Netflix-Style Streaming Service: Optimized for Kubernetes-based microservices, focusing on efficient log storage with metadata labels.
- User Service Logs: Labeled
{service="user-auth", environment="prod"}to quickly filter logs related to production authentication events. - Video Service Logs: Labeled
{service="video-streaming", quality="4k"}for debugging logs associated with high-resolution streaming issues. - Log Collection: Uses Promtail to automatically scrape logs and add container-specific metadata, streamlining ingestion across multiple microservices.
- User Service Logs: Labeled
Loki's label-based indexing is optimized for cloud-native and containerized environments, ensuring efficient log ingestion.
2. Query Languages and Search Capabilities
The ability to efficiently search and analyze logs is a key factor in choosing a log management tool.
Graylog's Search Language
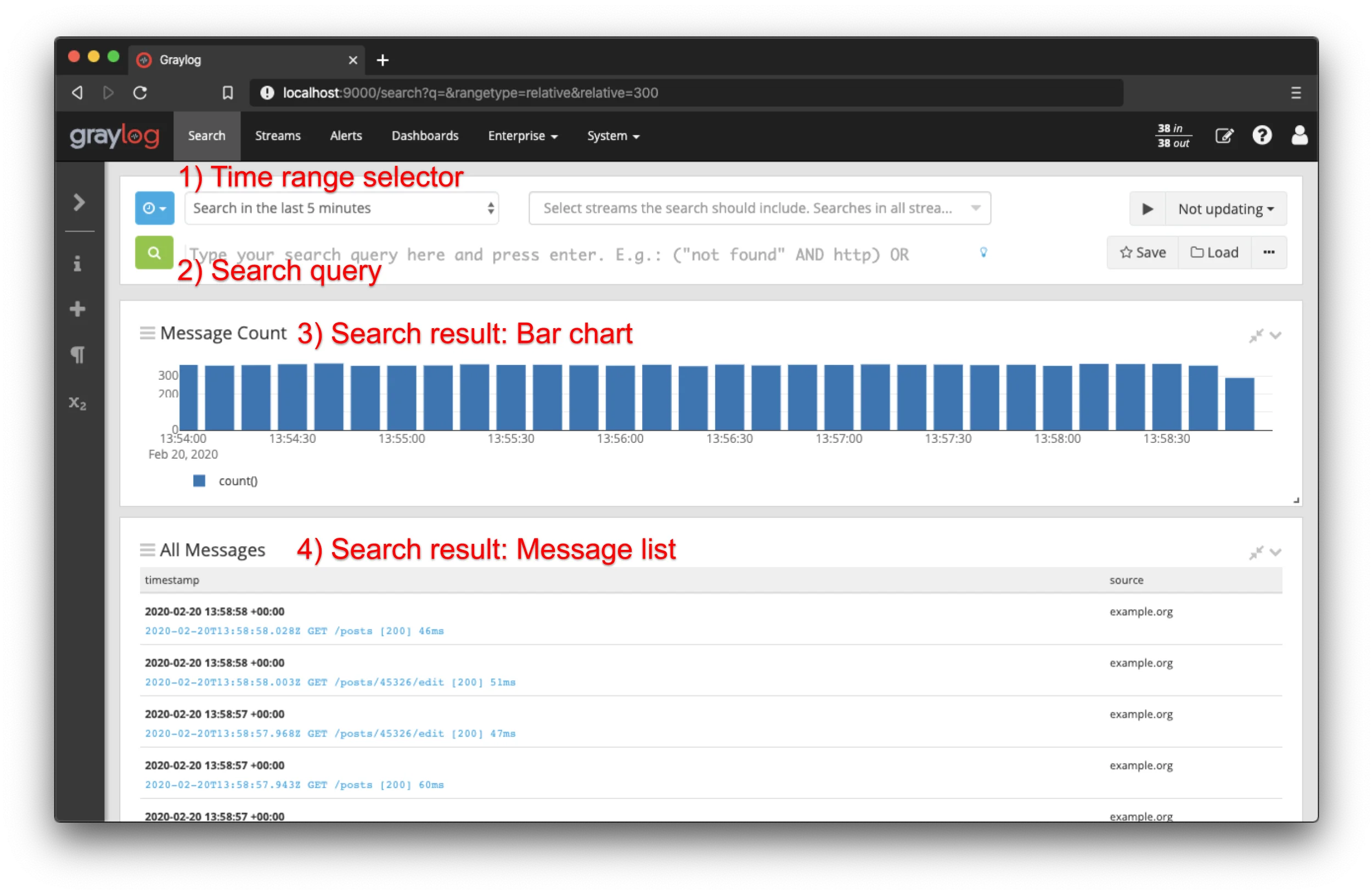
- Lucene-based Search: Graylog uses Lucene for querying logs. Lucene is a full-text search engine that allows fast and efficient searches through large volumes of data.
- Advanced Queries: Graylog allows for complex queries using Lucene's query language. You can filter, search using wildcards, fuzzy search, and range queries to find the data you need quickly. This is very useful when you have structured logs and need to perform detailed analysis or debugging.
- Example: If you need to find all error logs from the past week, you could use a query like:
level: error AND timestamp: [now-7d TO now] - Granular Searching: The Lucene-based approach is powerful and precise but can be resource-intensive, especially as the amount of log data grows.
Graylog's Lucene-based search offers unmatched precision and power for analyzing structured log data.
Loki's LogQL
- LogQL: Loki uses LogQL, a query language inspired by PromQL (Prometheus Query Language). LogQL works by combining two elements:
- Label Filters: Filters based on the metadata (labels) that were added to logs during ingestion.
- Line Filters: Filtering based on the actual content of the log line itself.
- Efficient Searching: While Loki's search capabilities are more lightweight compared to Graylog's Lucene, it excels in environments where logs are labeled well (such as in Kubernetes). However, for deeper text searching or full-text indexing, Loki may not perform as well as Graylog without additional setup or overhead.
- Example: If you want to find logs from a container with a specific label (e.g., "app=webapp"), you could use a query like:
{app="webapp"} |= "error"|= "error"is a line filter. It looks for logs that contain the string"error". The|=operator is used to search for the occurrence of the specified string (in this case,"error") in the log line.
Loki's LogQL is fast and efficient but works best when logs are labeled effectively.
3. Scalability
As your log volume grows, scalability becomes crucial. Here's how Graylog and Loki handle increasing loads:
Graylog Scalability
- Horizontal Scaling: Graylog can scale by adding more Elasticsearch nodes to handle increased indexing and search demand. As the data volume increases, Elasticsearch clusters can be expanded to distribute data and queries across multiple nodes.
- Resource Intensive: Graylog's scaling comes with a higher resource cost because Elasticsearch, the storage backend, can become resource-hungry when dealing with complex queries or large volumes of logs. This can lead to higher memory and CPU usage as the system grows.
- Use Case: Graylog is ideal for environments that require detailed log searches, complex analysis, and dashboards. But, it may not be as cost-effective when scaling for massive volumes of logs (unless fine-tuned).
Graylog is powerful for detailed analysis but scaling can be resource-intensive and costly.
Loki Scalability
- Horizontal Scaling: Loki is built to scale horizontally with minimal overhead. It uses a microservices-based design, where different components like Distributors, Ingesters, and Querier scale independently, making it easier to handle large volumes of logs.
- Efficient Storage: Loki stores logs in object storage systems like S3 or GCS, which means it doesn't rely on traditional databases like Elasticsearch for heavy indexing. This reduces storage costs and allows for efficient scaling even in cloud environments.
- Use Case: Loki is better suited for cloud-native environments, especially Kubernetes-based systems, where logs are ephemeral and the overhead of traditional indexing systems like Elasticsearch can be too high. Loki excels in environments with high-volume, short-lived logs like containerized applications.
Loki's microservices-based architecture ensures cost-effective scalability for large-scale, ephemeral log data.
4. Multi-Tenancy Support
Multi-tenancy refers to the ability of a single instance of a service to support multiple users or groups (tenants) with isolated data and configurations.
Graylog
- Role-Based Access Control (RBAC): Graylog supports role-based access control, where you can assign users to specific roles (e.g., admin, user, viewer). Each role has different permissions, allowing for fine-grained access to the logs.
- Multi-Tenant Setup: While Graylog can handle multiple users within a single instance, true multi-tenancy (i.e., isolation of different teams or customers' data) requires careful configuration, such as using separate clusters or deployments for each tenant.
- Use Case: Graylog's multi-tenancy setup works well for teams within an organization but is less suited for large managed service providers (MSPs) or scenarios where data isolation is required at a granular level.
Graylog supports basic multi-tenancy but may require additional infrastructure for robust isolation.
Loki
- Built-in Multi-Tenancy: Loki has built-in support for multi-tenancy, meaning it can separate logs by tenant without requiring separate deployments or clusters. This is done using authentication tokens that separate data streams for different tenants.
- Efficient Multi-Tenant Logging: This makes Loki ideal for environments like managed service providers (MSPs) or large teams where different departments or clients need their own isolated logs within a shared infrastructure.
- Use Case: If you are an MSP managing logs for multiple clients, Loki allows each client (tenant) to have isolated logs without the need for dedicated infrastructure for each. You can easily manage multiple tenants within the same system.
Loki's built-in multi-tenancy simplifies management and reduces infrastructure costs, making it ideal for MSPs.
Example: Managed Service Provider (MSP) for managing logs for 50 clients
- Graylog: Separate Elasticsearch indices are created for each client, leading to high infrastructure costs and complex management.
- Loki: Uses a single cluster with tenant IDs, which reduces infrastructure costs by 60% and simplifies log management without sacrificing data isolation.
Key Differences at a Glance:
| Feature | Graylog | Loki |
|---|---|---|
| Log Ingestion | Syslog, Beats, GELF, and other protocols | Promtail, Fluentd, Fluent Bit, custom shippers |
| Query Language | Lucene-based queries | LogQL (label + line filtering) |
| Scalability | Horizontal scaling with Elasticsearch | Horizontal scaling with microservices |
| Multi-Tenancy | Role-based access, separate clusters | Built-in multi-tenancy with authentication tokens |
Storage and Indexing Approaches
Storage and indexing are essential components in managing logs efficiently. Both Graylog and Loki have different strategies that affect their performance, scalability, and cost. Here's a comparison of how each handles log storage and indexing:
1. Graylog's Traditional Indexing Model
- Graylog relies on Elasticsearch/OpenSearch for storing logs, which uses inverted indexes. These indexes allow fast searches by creating a mapping of terms and their positions within documents.
- While this provides powerful text-search capabilities, it can result in higher storage overhead due to large index sizes.
- Index rotation and retention policies need to be carefully managed to avoid excessive storage costs.
2. Loki's Efficient Storage Approach
- Loki stores log data as compressed chunks in object storage like S3 or GCS. Instead of creating full-text indexes, Loki uses minimal indexes based on labels (like
app="webapp").- Chunks are fixed-size, compressed blocks of log data, typically representing a specific time range of logs from a single stream (defined by unique label combinations). They are immutable, compressed using algorithms, and stored in scalable object storage systems.
- This makes Loki more storage-efficient and allows for faster ingestion since it doesn't need to index every log line in detail. However, it offers less powerful full-text search capabilities compared to Graylog.
- Loki is particularly well-suited for environments like microservices, where logs are often ephemeral and have short retention periods.
3. Impact on Ingestion and Query Speeds
- Graylog: Query performance depends on the health of the Elasticsearch cluster and how the indexes are structured. As the data grows, the query speed may decrease unless optimized.
- Loki: Loki's ingestion is much faster due to the simplified indexing model. However, querying by label is quicker than doing full-text searches. Complex searches across large log volumes can be slower in Loki.
4. Long-Term Data Retention Considerations
- Graylog: Long-term data retention can be costly, especially as data grows. Graylog offers archiving strategies for retaining data in cheaper storage systems.
- Loki: Loki is built for cost-effective storage in cloud-based object stores, using chunk compaction to optimize long-term storage. This makes Loki ideal for scenarios where logs are retained over long periods but need to be stored efficiently.
Use Cases and Ideal Scenarios
When deciding between Graylog and Loki, it's essential to match each tool to the specific needs and characteristics of your environment. Let's break down where each tool shines and what type of use cases they best address.
1. Graylog: Best for Large Enterprise Setups
Graylog is ideal for organizations with complex log management needs, including:
- Granular Searches: Allows in-depth searches across diverse data sources (e.g., syslog, application logs, security logs). This is useful for finding specific patterns in large amounts of data.
- Complex Pipelines: Provides advanced pipelines that allow for detailed data transformations and enrichments, enabling deep analysis.
- Alerting and Dashboards: Graylog comes with built-in alerting, which can trigger notifications based on specific log conditions, and robust dashboards for data visualization.
- Plugin Ecosystem: It supports a wide range of plugins, making it easy to extend its functionality, especially in enterprise security environments.
2. Loki: Optimized for Cloud-Native and Containerized Environments
Loki is built for cloud-native applications, and is well-suited for environments where logs are generated in high volume and with short lifespans:
- Containerized Applications: Perfect for Kubernetes or Docker environments where logs are generated by ephemeral (short-lived) services.
- Minimal Indexing: Unlike Graylog, Loki doesn't index the content of logs in detail. It relies on a more lightweight labeling system, making it efficient for storing high-volume logs without overloading resources.
- Integration with Prometheus/Grafana: If you are already using Prometheus for monitoring, Loki integrates seamlessly with Grafana, offering a unified observability platform that combines metrics, logs, and traces.
3. Integration with Existing Tools
Both tools excel at integration, but they cater to different use cases:
- Graylog: Has a broad plugin ecosystem and is especially strong in environments where SIEM (Security Information and Event Management) integration is important. It also supports custom pipelines and workflows for log processing.
- Loki: Pairs effortlessly with Grafana, making it a great option if your team is already using Grafana dashboards. It's especially popular in Kubernetes environments, where logs are often dynamic and high in volume.
4. Small vs. Large Deployments
- Graylog: While Graylog can work for small setups, it's often resource-intensive and more suitable for larger, more complex systems with high indexing demands.
- Loki: Loki is highly scalable and is built to efficiently handle small to large deployments. Its horizontal scalability is beneficial for both small teams and large, distributed systems (like multi-region Kubernetes clusters).
Performance and Resource Utilization
When considering performance and resource utilization, both Graylog and Loki excel in different aspects based on their design and architecture. Understanding these differences can help you make the right choice depending on your infrastructure needs.
1. Ingestion Speeds and Query Throughput:
Graylog: Built on Elasticsearch, Graylog has faster query throughput for complex searches due to the powerful indexing capabilities of Elasticsearch. However, this comes at the cost of higher resource usage for both ingestion and querying.
Benchmark: Index size is approximately 40% of raw log size, requiring additional storage for high-volume environments.
Source: Excessive ElasticSearch Index Size
Example: A banking application collects 50,000 messages/second per node, including user login events, transaction logs, and fraud detection alerts. Graylog's Elasticsearch backend ensures 2-5 seconds query response for 1M logs, enabling auditors to perform quick searches.
- Suggestion: Use Graylog for scenarios demanding rapid and complex searches, such as financial audits or security event investigations.
Loki: Typically, Loki's log ingestion is lighter and more optimized for cloud-native environments. However, since it doesn't index logs as heavily as Graylog, performing large text searches might be slower.
Benchmark: Storage efficiency is 10-20% of raw log size after compression, making it ideal for large-scale environments.
Source: Planning system requirements and storage
Example: A Kubernetes cluster generates 100,000 lines/second, including pod logs labeled by namespace and service. Loki ingests these logs with lightweight Promtail agents, providing 0.5-2 seconds query response for label-based queries.
- Suggestion: Opt for Loki in environments with high log volumes but less need for full-text search, like cloud-native observability or monitoring containerized services.
2. Resource Requirements:
Graylog: Requires dedicated Elasticsearch/OpenSearch nodes, which can be resource-intensive, demanding high CPU, RAM, and disk space, especially when handling large log volumes.
Benchmark: Elasticsearch can handle up to 500 shards per node but becomes inefficient with high shard counts. Proper shard management is crucial.
Source: Understanding and Managing Elasticsearch Shards Limit
Example: An e-commerce platform handling 1TB/day of logs needs a cluster with 3 Elasticsearch nodes, each configured with 16 CPUs and 64GB RAM, and 1-2 Graylog servers to handle indexing and queries.
- Suggestion: Allocate resources proportionally to log volume. For cost-efficiency, set index rotation policies to archive older data to cheaper storage.
Loki: More resource-efficient, especially during ingestion. Loki offloads log data to object storage (like S3), making it more memory-friendly when dealing with large log volumes, as it avoids the heavy disk I/O operations required by Elasticsearch.
Benchmark: Loki achieves ~90% lower CPU usage compared to full-text indexing systems.
Source: Logs Performance Benchmark
Example: A streaming service handling 1TB/day of logs uses object storage (e.g., S3) to offload disk I/O. The system runs on a smaller cluster with fewer ingester and distributor nodes, saving on compute costs.
- Suggestion: Leverage object storage for large-scale log retention and reduce on-premises hardware dependencies.
3. Scalability in High-Volume Environments:
Graylog: While Graylog can scale horizontally, it requires adding more Elasticsearch/OpenSearch nodes and Graylog servers. This can get complex and costly as data volume increases.
Benchmark: Elasticsearch scaling is highly dependent on shard distribution and network throughput, with a recommended 30-50GB per shard for optimal performance.
Source: Size your shards
Example: Scaling an enterprise system from 1TB/day to 5TB/day requires adding 9 Elasticsearch nodes (up from 3) to handle indexing and query loads, plus additional Graylog servers for ingestion.
- Suggestion: Plan for high scaling costs and complexity. Use index optimization techniques like reducing shard count and replication factor to manage resource usage.
Loki: Designed for horizontal scalability in distributed systems, Loki is more efficient in handling massive log volumes, especially in Kubernetes or cloud-native environments. Its label-based indexing makes scaling easier and cheaper.
Benchmark: Loki's scalability is validated in Grafana Cloud, managing petabyte-scale logs daily while maintaining high query performance.
Source: Loki overview
Example: A Kubernetes-based application scales from 5TB/day to 10TB/day by adding distributors and ingesters without overhauling the architecture. Loki's label-based indexing ensures efficient scaling.
- Suggestion: Keep labels concise and avoid high cardinality (e.g., avoid using unique request IDs as labels) to maintain query performance at scale.
4. Optimization Techniques:
Graylog: To optimize resource usage, Graylog requires careful management of index shards, replication, and rotation settings. Tuning index retention policies and utilizing caching effectively can also improve performance.
Benchmark: Properly managed shard allocation can reduce Elasticsearch query latency by 30-50%.
Source: Reduce Elasticsearch Search Latency and Optimize Search Performance
Example: A cybersecurity system ingests 500K events/hour and uses 2 shards per index with a 7-day retention policy. Cached queries reduce response times for repeated searches.
- Suggestion: Optimize shard allocation and caching for frequently queried datasets to improve performance without overloading resources.
Loki: To optimize performance, Loki recommends minimizing cardinality by properly labeling logs. Multi-tenancy support allows for better management in environments with multiple teams. Additionally, adjusting chunk sizes helps with efficient storage and retrieval of log data.
Benchmark: Loki's chunk size tuning reduces storage costs by up to 25% while maintaining fast retrieval times.
Source: Loki Storage Optimization
Example: A DevOps team monitors 10K services using fewer than 50 unique label combinations, such as
{app="service1", env="prod"}. Adjusted chunk sizes minimize storage costs while retaining fast access.- Suggestion: Use meaningful but limited labels (e.g., app, environment, log level) to reduce label cardinality and enhance performance.
Setup and Maintenance
Setting up and maintaining a logging system requires careful attention to installation processes, regular maintenance, and community support. Let's explore how Graylog and Loki compare in these areas:
1. Initial Setup Complexity
- Graylog: Setting up Graylog involves configuring multiple components: MongoDB for metadata storage, Elasticsearch for log indexing, and the Graylog server for log processing. This can be more resource-intensive and complex, especially in large environments.
- Loki: On the other hand, Loki is often deployed in cloud-native environments, primarily using Helm charts in Kubernetes or Docker Compose for simplicity. It also requires external log shippers like Promtail to forward logs, making setup easier but still dependent on external components.
2. Ongoing Maintenance
- Graylog: Maintenance involves managing the Elasticsearch cluster, monitoring resource usage, and ensuring plugins are compatible with the latest Graylog and Elasticsearch versions. This can become time-consuming, especially with larger volumes of logs.
- Loki: Since Loki is built around a microservices architecture, maintaining it in a Kubernetes setup can be more straightforward. However, the reliability of the object storage system (e.g., S3 or GCS) is crucial, and any issues with this can affect log retrieval.
3. Community Support and Documentation
- Graylog: Being a mature tool, Graylog has an established user base and extensive community support, including forums and commercial support options. Its documentation is comprehensive, helping users through both setup and troubleshooting.
- Loki: Loki is part of the fast-growing CNCF ecosystem, supported by Grafana. Its community is expanding rapidly, and being part of the open-source ecosystem ensures vibrant discussions and documentation, though newer features might require deeper investigation for troubleshooting.
4. Upgrade Processes and Backward Compatibility
- Graylog: Upgrading Graylog involves ensuring compatibility across all components (Graylog, Elasticsearch, and MongoDB). Versioning coordination is critical to prevent breaking changes.
- Loki: Loki upgrades, especially when deployed in a containerized environment, tend to be simpler due to its microservices architecture. However, new features might require configuration changes, so careful testing is recommended during upgrades.
Cost Considerations
When choosing between Graylog and Loki, it's important to consider the long-term costs associated with deployment, scaling, and infrastructure. Both tools have open-source editions, but the infrastructure requirements, scaling approaches, and overall cost can differ significantly.
Below is a detailed breakdown of key cost factors, now with specific resource requirements and cost estimates.
1. Open-Source vs. Enterprise Editions:
- Both Graylog and Loki offer robust open-source versions. However, Graylog also has an Enterprise edition that includes advanced features like extra security options, support, and more extensive management capabilities. The Enterprise version comes with licensing fees, whereas the open-source versions are free.
2. Infrastructure Costs:
- Graylog: Since it relies on Elasticsearch for log storage, you'll need high-performance disks and more compute power to handle indexing and searching. Elasticsearch's resource-intensive nature can lead to higher infrastructure costs.
- Loki: Loki is designed for horizontal scaling and stores logs in object storage like AWS S3, GCS, etc. This approach often makes it more cost-effective in terms of infrastructure, especially in cloud-native environments.
3. Scaling Costs:
- Graylog: Scaling involves adding more Elasticsearch nodes and Graylog servers. Elasticsearch can become costly with the need for high compute and storage capacity, especially as log volumes grow.
- Loki: Loki's object storage model means you mostly pay for storage costs, with the compute resources being more flexible and often cheaper. Horizontal scaling is more efficient and cost-effective compared to adding new nodes for Elasticsearch.
4. Total Cost of Ownership (TCO):
The total cost of ownership should consider not only the infrastructure costs but also operational overhead and ongoing support.
- Graylog might incur higher TCO due to the heavy reliance on compute-intensive Elasticsearch and the additional licensing costs for enterprise features.
- Due to its reliance on Elasticsearch for log storage and indexing, Graylog typically incurs higher TCO. Compute-intensive requirements for indexing, coupled with storage and potential enterprise licensing fees, can increase costs significantly as log volumes grow.
- Loki offers a more scalable and cheaper approach, especially for cloud-native environments, with lower costs for scaling out compute and using object storage.
- Loki's efficient use of object storage and low indexing overhead makes it more cost-effective. Its horizontal scaling model ensures predictable costs, especially in cloud-native environments.
Here's the information in a concise table for system requirements:
| Aspect | Graylog | Loki |
|---|---|---|
| Open-Source vs. Enterprise | - Open-source and Enterprise versions available.- Enterprise adds advanced features but has licensing fees (~$5000/year). | - Fully open-source with optional enterprise features.- No licensing fees. |
| Storage Requirements | Relies on Elasticsearch (resource-intensive).- Storage: 300GB (with replication). | Uses object storage (cost-efficient).- Storage: 150GB (compressed logs). |
| Compute Requirements | - Elasticsearch Nodes:• Minimum: 16GB RAM, 4 CPU cores, 100GB SSD.• Recommended: 32GB RAM, 8 CPU cores, 500GB SSD.• Production: Multiple 64GB RAM nodes.- MongoDB:• Minimum: 4GB RAM, 2 CPU cores.• Production: 8GB RAM, 4 CPU cores.- Graylog Server:• Minimum: 8GB RAM, 4 CPU cores.• Production: 16GB RAM, 8 CPU cores. | - Distributor/Querier Nodes:• Small Setup: 2GB RAM, 2 CPU cores per component.• Production: 4GB RAM, 4 CPU cores per component.- Object Storage:• AWS S3: 0.023 per GB/month.• GCS: 0.020 per GB/month.- Cache (Redis/Memcached):• Minimum: 2GB RAM.• Production: 8GB RAM. |
| Scaling Costs | - Scaling requires adding Elasticsearch nodes and Graylog servers.- Monthly Costs: 500–1000 (compute and storage).- Higher costs as log volumes grow. | - Horizontal scaling with object storage is more cost-effective.- Monthly Costs: 200–400 (storage and minimal compute). |
| Total Cost of Ownership | Higher TCO due to Elasticsearch's compute-intensive nature and optional licensing fees. | Lower TCO due to efficient scaling and reliance on object storage. |
This table provides a structured and simplified view of the differences in system requirements and costs for Graylog and Loki.
Integration with Existing Tools
The ability to integrate with your current tech stack is crucial for a seamless observability pipeline. Both Graylog and Loki are designed to integrate seamlessly into your existing infrastructure, making it easier to collect, manage, and visualize logs. Below is a comparison of how each tool interacts with popular logging and monitoring solutions.
1. Compatibility with Log Shippers:
- Graylog: Graylog supports several log shippers such as Beats, Logstash, and Fluentd. While it can work with other shippers, Graylog sidecars (a small agent running alongside your application) are often used to streamline log collection.
- Loki: Primarily uses Promtail (its own log shipper) for log collection, but it also integrates with other shippers like Fluentd and Fluent Bit, offering flexibility in different environments.
2. Dashboard and Visualization Options:
- Graylog: Offers built-in dashboarding and visualization options within the Graylog UI, allowing users to create real-time dashboards for monitoring log data.
- Loki: While Loki itself does not have built-in visualization, it integrates seamlessly with Grafana for dashboarding. Grafana is widely used for querying and visualizing logs stored in Loki, making it a powerful tool for log analysis.
3. Alert Integration Capabilities:
- Graylog: Has a native alerting engine that supports a wide range of plugins, enabling real-time notifications based on custom queries. Alerts can trigger actions such as sending emails, Slack messages, or calling webhooks.
- Loki: Uses Grafana Alerting to integrate with Loki logs. It can also support alert rules directly in LogQL (Loki's query language), triggering notifications based on log patterns.
4. API Availability and Extensibility:
- Graylog: Provides a REST API that allows users to manage inputs, dashboards, and alerts programmatically, providing extensibility for integration with other tools.
- Loki: Offers an HTTP API to query logs, retrieve metadata, and manage multi-tenancy, making it easy to interact with logs stored in Loki and integrate it with external systems.
SigNoz: A Modern Alternative
SigNoz is a modern, open-source observability platform designed to give you an all-in-one solution for monitoring and troubleshooting applications. It provides insights into your logs, metrics, and traces from a single interface, making it a powerful tool for modern cloud-native environments.
SigNoz is built on popular open standards like OpenTelemetry and other CNCF (Cloud Native Computing Foundation) technologies.
Key Features
- Advanced Log Search and Filtering: SigNoz provides robust log search and filtering capabilities, enabling users to quickly locate and analyze logs using various attributes and criteria.
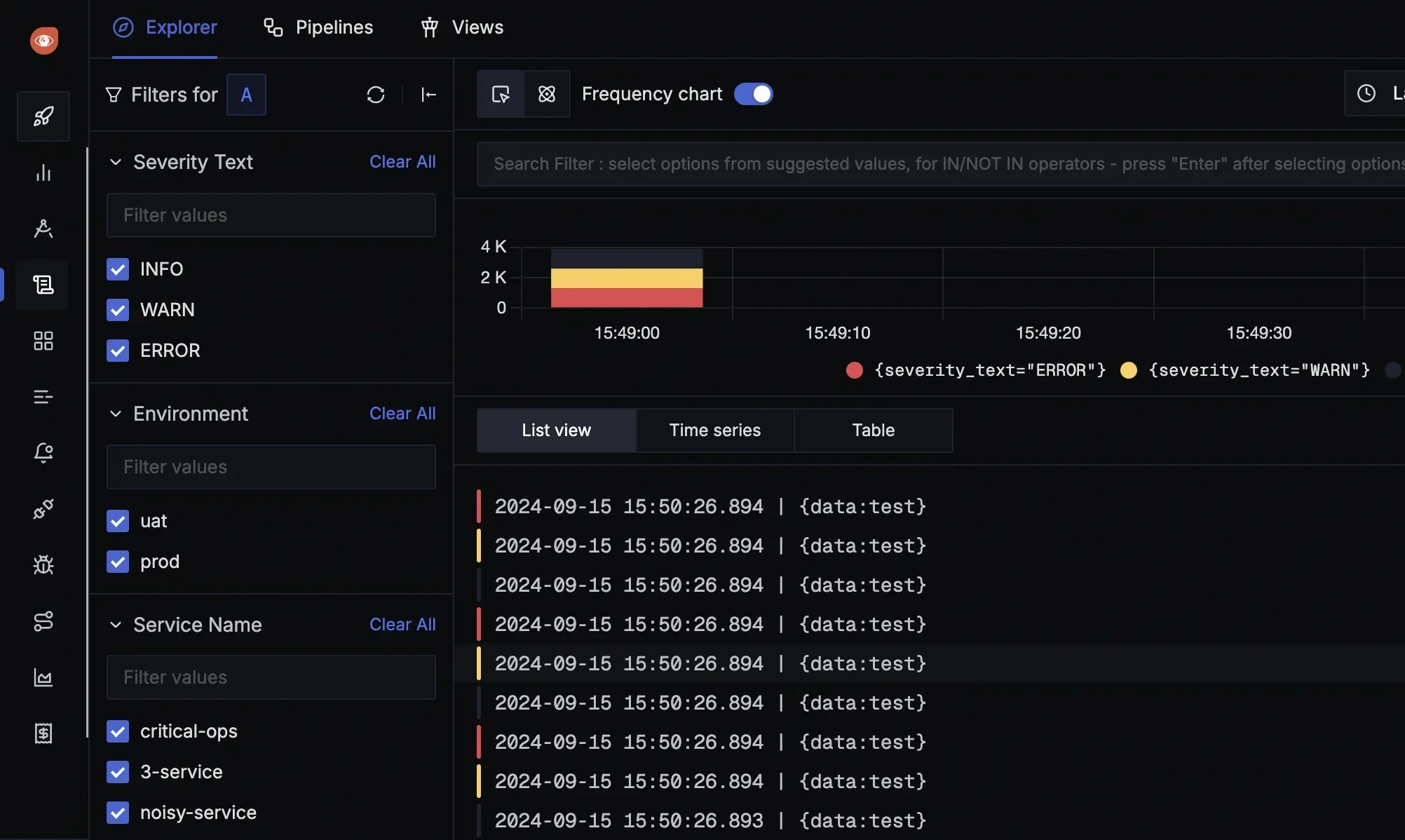
SigNoz's filtering capabilities - Real-Time Log Monitoring: Monitor logs in real-time to promptly detect and address issues as they occur, ensuring system reliability and performance.
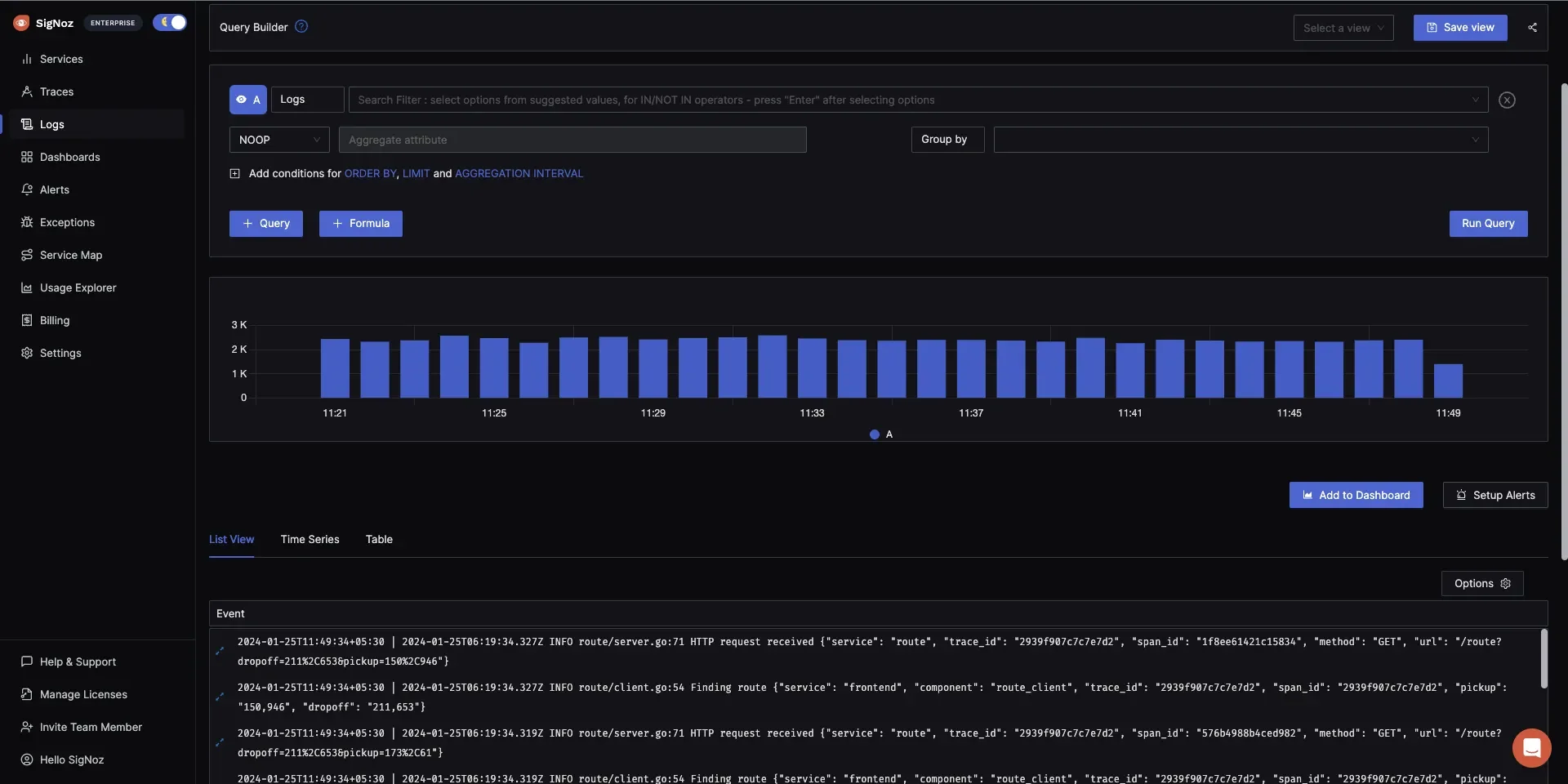
Logs management in SigNoz - Seamless Integration with OpenTelemetry: Built on open standards like OpenTelemetry, SigNoz ensures seamless instrumentation and compatibility with various data sources.
In addition to its robust features, SigNoz has demonstrated impressive performance in log management. Benchmark tests indicate that SigNoz ingests logs 2.5 times faster than the ELK stack while utilizing 50% fewer resources. For aggregate queries, SigNoz outperforms ELK by being 13 times faster. Additionally, SigNoz requires approximately half the storage space compared to ELK for the same volume of log data.
How SigNoz Compares to Graylog and Loki
Here's a comparison table showcasing how SigNoz, Graylog, and Loki differ based on key parameters that users care about:
| Parameter | SigNoz | Graylog | Loki |
|---|---|---|---|
| Primary Focus | Unified observability with logs, metrics, and traces in one platform. | Log management with strong search and alerting features. | Log aggregation and query performance in cloud-native environments. |
| Data Types Supported | Logs, metrics, and traces. | Logs only. | Logs only (optimized for label-based indexing). |
| Architecture | Built on OpenTelemetry and CNCF standards, leveraging ClickHouse for efficient storage. | Relies on Elasticsearch/OpenSearch and MongoDB for indexing and storage. | Lightweight with label-based indexing; stores logs in object storage like S3. |
| Scalability | Efficient scaling for large datasets with minimal resource usage. | Requires scaling Elasticsearch nodes and Graylog servers, which can be resource-intensive. | Horizontally scalable with low overhead using object storage. |
| Search Capabilities | Combines attribute filtering with advanced querying for logs, metrics, and traces. | Advanced Lucene-based search with full-text indexing. | Label-based searches with LogQL; limited full-text search capabilities. |
| Ease of Deployment | Streamlined deployment with Kubernetes and Docker support. | Moderate complexity; requires Elasticsearch, MongoDB, and Graylog server configuration. | Easy to deploy in Kubernetes and cloud environments using Promtail/Fluentd. |
| Cost Efficiency | Cost-efficient, combining unified observability with minimal overhead. | High costs due to Elasticsearch storage and compute requirements. | Cost-effective, leveraging object storage for scalability. |
Key Takeaways:
- Graylog is ideal for users who need powerful log management and advanced search capabilities but are willing to manage complex infrastructure. You can explore some alternatives to Graylog here as well.
- Loki suits teams operating in cloud-native environments with a focus on cost-effective log aggregation and querying. Explore some alternatives to Loki to see if they better suit your needs.
- SigNoz is the best fit for those seeking full-stack observability (logs, metrics, and traces) with modern deployment flexibility and lower total cost of ownership.
Get Started with SigNoz
- You can easily deploy SigNoz using Docker or Helm (for Kubernetes setups).
- Start by instrumenting your applications with OpenTelemetry to send logs, metrics, and traces to SigNoz for full observability.
- To get started with monitoring your applications with SigNoz, you need to begin with SigNoz.
SigNoz Cloud is the easiest way to run SigNoz. Sign up for a free account and get 30 days of unlimited access to all features.
You can also install and self-host SigNoz yourself since it is open-source. With 24,000+ GitHub stars, open-source SigNoz is loved by developers. Find the instructions to self-host SigNoz.
Making the Right Choice
Choosing the right log management tool between Graylog and Loki depends on various factors, including your infrastructure, team expertise, specific use cases, and integration needs. Here's a breakdown of key decision factors to help you make the best choice:
1. Infrastructure and Future Scalability Needs
- Graylog is often preferred in traditional, on-prem environments where you need advanced search and log analytics capabilities. It can scale with more resources (Elasticsearch nodes) but can become resource-heavy with high log volumes.
- Loki, on the other hand, is built for cloud-native, containerized environments. It scales efficiently with horizontal scaling, making it ideal for cloud-based or Kubernetes setups.
2. Team Expertise and Learning Curve
- Graylog might require a steeper learning curve, especially if your team is unfamiliar with Elasticsearch or Lucene queries. If your team is used to these technologies, Graylog will be a natural fit.
- Loki, being part of the Prometheus/Grafana stack, is a great choice if your team is already familiar with those tools. Its label-based query system (LogQL) can be easier to use, especially for teams accustomed to Prometheus.
3. Specific Log Analysis Requirements
- If your log analysis needs involve advanced transformations, complex search queries, and security analytics, Graylog might be a better fit, thanks to its powerful indexing and search capabilities.
- Loki, with its label-based queries, works best for simpler searches and is optimized for storing and querying large volumes of ephemeral logs (e.g., container logs), making it ideal for cloud-native environments.
4. Integration with Current Monitoring Stack
- If you're already using Prometheus and Grafana, Loki integrates seamlessly with them, offering a unified monitoring solution for logs, metrics, and traces.
- If you're looking for an all-in-one observability platform that handles logs, metrics, and traces in one system, SigNoz could be an alternative to consider, especially for modern cloud-native setups.
By carefully evaluating these factors, you can select the log management tool that best fits your organization's needs and future growth plans.
Key Takeaways
- Graylog is a powerful choice for enterprise-level environments requiring advanced search capabilities, but it demands heavier infrastructure (Elasticsearch and MongoDB) and incurs higher total costs of ownership.
- Loki is optimized for cloud-native and containerized environments, offering a scalable and cost-effective solution with efficient storage and horizontal scaling capabilities. However, its minimal indexing approach is better suited for label-based queries than full-text searches.
- Scalability and Cost: Organizations with high log volumes or distributed systems should weigh the scalability and storage efficiency of Loki against the powerful analysis features of Graylog, keeping long-term infrastructure costs in mind.
- Integration and Ecosystem Fit: Graylog integrates seamlessly with traditional enterprise stacks, while Loki shines in Kubernetes and microservices-based architectures.
- Consider Alternatives: Explore tools like SigNoz, which provide a holistic observability stack, integrating logs, metrics, and traces for unified monitoring, potentially reducing operational complexity.
FAQs
Can Loki handle the same volume of logs as Graylog?
Yes, Loki can handle large volumes and often scales more cost-effectively. However, for advanced text search at massive scale, Graylog's indexing approach may be more suitable.
Which tool offers better integration with Kubernetes environments?
Loki is natively designed for Kubernetes (through Promtail) and works seamlessly with Grafana. While Graylog can be deployed in Kubernetes, Loki is often the preferred choice for containerized logs.
Is it possible to migrate from Graylog to Loki or vice versa?
Migration is possible but can be complex. You'll need to reconfigure log shippers, adjust queries, and consider data re-indexing or re-ingestion strategies. It's often easier to start fresh with a new tool and migrate gradually.
How do retention policies differ between Graylog and Loki?
Graylog manages retention through Elasticsearch index lifecycle policies, while Loki uses retention periods set on streams or tenants. Loki's approach can be more cost-effective for long-term storage in cloud object stores.
