The 5 Phases of Incident Response - A Complete Guide
Cybersecurity incidents are inevitable, making a robust incident response strategy essential for organizations. The incident response cycle, as outlined by the National Institute of Standards and Technology (NIST), provides a structured framework to effectively detect, manage, and resolve these incidents. A well-structured incident response cycle is your best defense against these threats. This guide breaks down the five crucial phases of incident response, providing you with the knowledge and tools to protect your digital assets effectively.
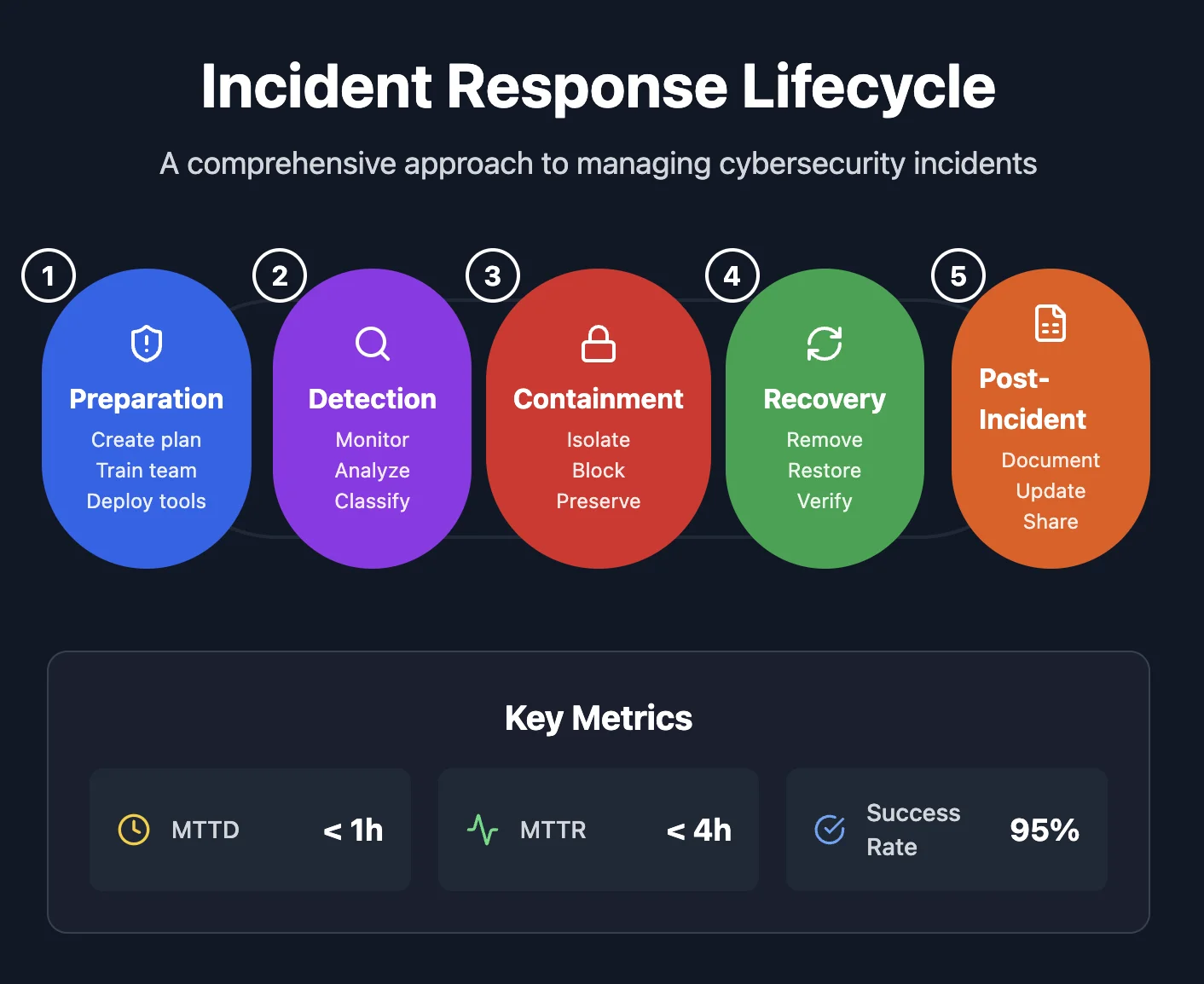
What is the Incident Response Cycle?
The incident response cycle is a systematic approach to managing and mitigating cybersecurity incidents. It serves as a vital framework for organizations to prepare for, detect, contain, and recover from security breaches. Developed by the National Institute of Standards and Technology (NIST), this framework—known as the Incident Response Lifecycle—is widely recognized for its structured and repeatable methodology. By dividing incident response into five clear phases—Preparation, Detection and Analysis, Containment, Eradication and Recovery, and Post-Incident Activity—this approach ensures a systematic and comprehensive way to mitigate damage and prevent future occurrences.
Why is a Structured Approach Crucial?
A structured incident response process is essential for organizations to:
- Respond Quickly – Minimize delays in addressing security incidents.
- Reduce Impact – Limit damage and shorten recovery time.
- Enhance Resilience – Improve security defenses through lessons learned.
Overview of the Five Phases
The NIST lifecycle divides incident response into five interconnected phases as follows:
.webp)
NIST lifecycle Phases
Preparation – Building readiness through planning and training.
Preparation ensures the team is ready to handle incidents. The organization conducts regular cybersecurity training and has incident response playbooks. Backup systems are configured for data protection. For example, endpoint detection tools flagged unusual activity during the attack.
Detection and Analysis – Identifying incidents and understanding their scope.
This phase involves detecting and analyzing the threat. Security alerts reveal suspicious activity, and analysts confirm it’s ransomware. For instance, network logs showed the malware was triggered by an employee clicking a malicious email link.
Containment – Limiting the spread and impact of threats.
Containment focuses on stopping the threat from spreading. Affected systems are isolated, and firewalls block attacker communication. For example, firewalls were reconfigured to prevent further spread of the ransomware.
Eradication and Recovery – Eliminating threats and restoring normalcy. The threat is removed, and systems are restored. Infected devices are wiped, backups are restored, and vulnerabilities are patched. For example, encrypted data was recovered from offline backups.
Post-Incident Activity – Learning from incidents to strengthen defenses. Post-incident reviews focus on improving future responses. Security measures, like multi-factor authentication, are added, and employees receive additional training. For example, email security systems were upgraded to prevent similar attacks.
Together, these phases form a robust strategy to tackle cybersecurity incidents efficiently and effectively. Let's dive into each phase to understand how they work together to create a robust incident response strategy.
Phase 1: Preparation - Building Your Incident Response Foundation
Preparation is the first and most critical phase of the incident response cycle. It focuses on creating a strong foundation to handle incidents effectively when they occur.
Key Actions in the Preparation Phase
- Developing a Comprehensive Incident Response Plan
- Outline clear policies and procedures for managing incidents.
- Define the scope of incidents covered, from minor breaches to major attacks.
- A ransomware incident policy should include containment and restoration steps from secure backups.
- Assembling and Training an Incident Response Team
- Form a dedicated team with clearly assigned roles, such as incident commander, forensic analyst, and communications officer.
- Provide regular training, including hands-on simulations and threat-specific exercises.
- Assign team members based on expertise, such as IT security for technical analysis and PR for external communications.
- Establishing Communication Protocols and Escalation Procedures
- Set up clear communication channels for reporting and handling incidents.
- Define an escalation matrix to involve the right stakeholders at the appropriate time.
- Use a secure chat group and automated alerts for quick response during breaches.
- Implementing Necessary Tools and Technologies
- Deploy monitoring and alerting systems like SIEM tools for real-time detection.
- Ensure the availability of forensic tools, secure backups, and access controls.
- Use SIEM tools like Splunk for real-time alerts and off-site backups for data recovery.
Key Components of an Effective Incident Response Plan
Your incident response plan should include:
- Clearly defined roles and responsibilities: Assign specific tasks to team members, ensuring everyone knows their part in the response process.
- Incident classification and prioritization framework: Create a system to categorize incidents based on severity and potential impact.
- Documentation and reporting templates: Prepare standardized forms to ensure consistent and thorough incident documentation.
- Regular testing and updating: Conduct periodic reviews and simulations to keep your plan current and effective.

SigNoz can help with tracking application performance and monitoring metrics, ensuring your systems are ready for potential incidents. Additionally, tools like Splunk and Tanium can assist with log management and endpoint visibility to enhance preparation.
Phase 2: Detection and Analysis - Identifying and Understanding Threats
In the Detection and Analysis phase, the focus is on identifying potential incidents quickly and understanding their scope to formulate an effective response. This phase is critical for minimizing damage and preventing further escalation.
Quick and accurate threat detection is crucial for minimizing damage. This phase involves:
- Implementing Robust Monitoring and Alerting Systems - Deploy advanced tools like SIEM, EDR, IDS, and network analyzers to monitor and analyze activities in real-time, ensuring comprehensive threat visibility.
- Techniques for Quick and Accurate Incident Detection - Utilize machine learning models and baseline activity patterns to identify anomalies and flag potential incidents swiftly and accurately.
- Conducting Initial Triage and Incident Classification - Categorize and prioritize incidents based on severity to allocate resources effectively and streamline response efforts.
- Performing In-Depth Analysis - Analyze logs, network data, and system artifacts to identify the root cause, entry point, and potential impact of the incident.
Common Challenges in Detection and Analysis
- False Positives and Alert Fatigue
- Problem: Overwhelmed teams waste resources on benign alerts.
- Solution: Use adaptive machine learning to refine detection accuracy and prioritize high-risk alerts.
- Identifying Sophisticated or Zero-Day Attacks
- Problem: These threats evade traditional detection methods.
- Solution: Employ advanced behavior-based detection tools to spot unusual activity patterns.
- Correlating Data from Multiple Sources
- Problem: Disparate systems generate fragmented data, complicating analysis.
- Solution: Utilize SIEM platforms to aggregate and correlate data, enabling a unified view of incidents.
- Balancing Speed and Thoroughness
- Problem: Rushing to contain incidents may overlook critical details.
- Solution: Implement a tiered approach—conduct rapid triage followed by detailed investigation for significant incidents.
SigNoz can help you detect application performance issues in real-time. Pairing it with tools like Elasticsearch for log analysis, Prometheus for infrastructure monitoring, and CrowdStrike for endpoint threat detection will ensure a comprehensive detection and analysis process.
Phase 3: Containment - Limiting the Damage
Once an incident is detected, swift action is needed to prevent further spread. Containment strategies include:
- Immediate actions: Quickly halt the incident's progression by disconnecting compromised systems or disabling affected accounts.
- Short-term containment: Isolate impacted systems to continue operations while deploying patches or temporary fixes.
- Long-term containment: Strengthen defenses by addressing vulnerabilities and implementing enhanced security measures.
- System isolation and shutdown: Make informed decisions to balance operational continuity with security needs.
Containment Strategies for Different Types of Incidents
- Malware outbreaks:
- Isolate infected systems from the network
- Block known malicious IP addresses and domains
- Deploy updated antivirus signatures across the organization
- Data breaches:
- Revoke compromised credentials
- Implement additional authentication measures
- Monitor for unusual data access or exfiltration attempts
- Denial of Service (DoS) attacks:
- Work with ISPs to filter malicious traffic
- Employ load balancers to distribute traffic
- Use Content Delivery Networks (CDNs) to absorb attack volume
- Insider threats:
- Revoke access privileges for suspected individuals
- Monitor and log all user activities
- Implement data loss prevention (DLP) tools
During containment, SigNoz can provide continuous monitoring to track the impact of incident isolation. For securing the network, Palo Alto Networks and Fortinet are ideal for firewall management, while Apex One offers endpoint protection to prevent further damage.
Phase 4: Eradication and Recovery - Removing the Threat and Restoring Operations
With the incident contained, it's time to eliminate the threat and return to normal operations. This phase includes:
- Identifying and eliminating the root cause: Investigate to find the origin of the incident, such as compromised accounts or security gaps, and fully address it to prevent recurrence.
- Removing malware and other malicious artifacts: Clear infected systems of any malware, backdoors, or other harmful elements to ensure no remnants remain.
- Patching vulnerabilities and strengthening security controls: Apply necessary patches and update security protocols to close any weaknesses that were exploited during the attack.
- Restoring systems and data from clean backups: Recover affected systems and data from verified, uninfected backups to return to normal operations securely.
Best Practices for Secure Recovery
- Verify backup integrity: Before restoration, ensure your backups are clean and uncorrupted.
- Use hash values to confirm backup integrity
- Test backups in an isolated environment before full restoration
- Implement additional security measures: Use the recovery process as an opportunity to enhance your defenses.
- Deploy multi-factor authentication across all systems
- Update and patch all software to the latest versions
- Implement network segmentation to limit potential damage from future incidents
- Conduct thorough testing: Before returning systems to production, verify their security and functionality.
- Perform vulnerability scans on restored systems
- Conduct penetration testing to identify any remaining weaknesses
- Monitor for reinfection: Stay vigilant for signs that the threat may still be present.
- Implement enhanced logging and monitoring on recovered systems
- Use file integrity monitoring tools to detect unauthorized changes
SigNoz continues to monitor the system’s recovery process. Tools like Carbon Black are great for eradicating malware, while Veeam ensures secure backup and recovery, and Puppet can automate patching and configuration to strengthen defenses during recovery.
Phase 5: Post-Incident Activity - Learning and Improving
The incident response cycle doesn't end with recovery. Post-incident activities are crucial for continuous improvement:
- Conducting a comprehensive post-incident review: Assess the entire response process, from detection to recovery, to identify strengths and weaknesses.
- Documenting lessons learned and updating the incident response plan: Capture insights gained during the incident and update the response plan to reflect these lessons.
- Identifying areas for improvement in security posture: Review security practices and tools to enhance defenses and prevent similar incidents in the future.
- Sharing relevant information with stakeholders and the wider security community: Communicate key findings, recommendations, and improvements to stakeholders, and consider sharing anonymized data with the security community to improve collective defenses.
Measuring the Effectiveness of Your Incident Response
To ensure your incident response process is continually improving, consider these key performance indicators (KPIs):
- Mean Time to Detect (MTTD): MTTD refers to the time it takes for your team to detect an incident after it occurs. It measures how quickly an incident is identified from the moment it starts impacting your systems. A lower MTTD means your team can detect incidents faster, which allows for quicker action and minimizes the potential damage caused by the attack.
- Mean Time to Respond (MTTR): MTTR is the time it takes from detecting an incident to mitigating or resolving it. It measures how quickly your team can respond to and contain the threat. A shorter MTTR indicates a well-prepared team that can quickly control the situation and prevent it from escalating further.
- Incident resolution rate: This metric tracks the percentage of incidents that are successfully resolved by your team. It reflects the overall effectiveness of your incident response plan and the team's ability to address and mitigate the threats. A high incident resolution rate signifies that your incident response processes and team are effective. It also highlights areas where your team may need additional training or resources to address specific types of incidents more efficiently.
- Cost per incident: CPI refers to the financial impact of each incident on your organization. This includes direct costs, such as recovery efforts, legal fees, and compensation, as well as indirect costs like lost productivity and reputational damage. Lowering CPI means your team is responding efficiently to incidents, reducing both the operational and financial costs.
Regularly conduct tabletop exercises and simulations to test your team's readiness and identify areas for improvement. Track and analyze incident trends over time to spot patterns and adjust your strategy accordingly.
SigNoz helps analyze post-incident data, highlighting performance issues. You can also use JIRA to track follow-up actions, New Relic for deeper performance analysis, and Sumo Logic for trend analysis and reporting to fine-tune your incident response strategies.
Enhancing Your Incident Response with SigNoz
As you refine your incident response cycle, integrating SigNoz, an open-source application performance monitoring (APM) and observability tool, can significantly enhance your incident detection and analysis capabilities.
Key Features of SigNoz:
- Real-time Monitoring: Visualize application and infrastructure metrics as they happen.
- Distributed Tracing: Pinpoint root causes by tracking requests across services.
- Customizable Dashboards: Create tailored views of key performance indicators.
- Alerting Mechanisms: Proactively notify your team of potential incidents.
SigNoz Cloud is the easiest way to run SigNoz. Sign up for a free account and get 30 days of unlimited access to all features.
You can also install and self-host SigNoz yourself since it is open-source. With 24,000+ GitHub stars, open-source SigNoz is loved by developers. Find the instructions to self-host SigNoz.
Using SigNoz for Incident Response
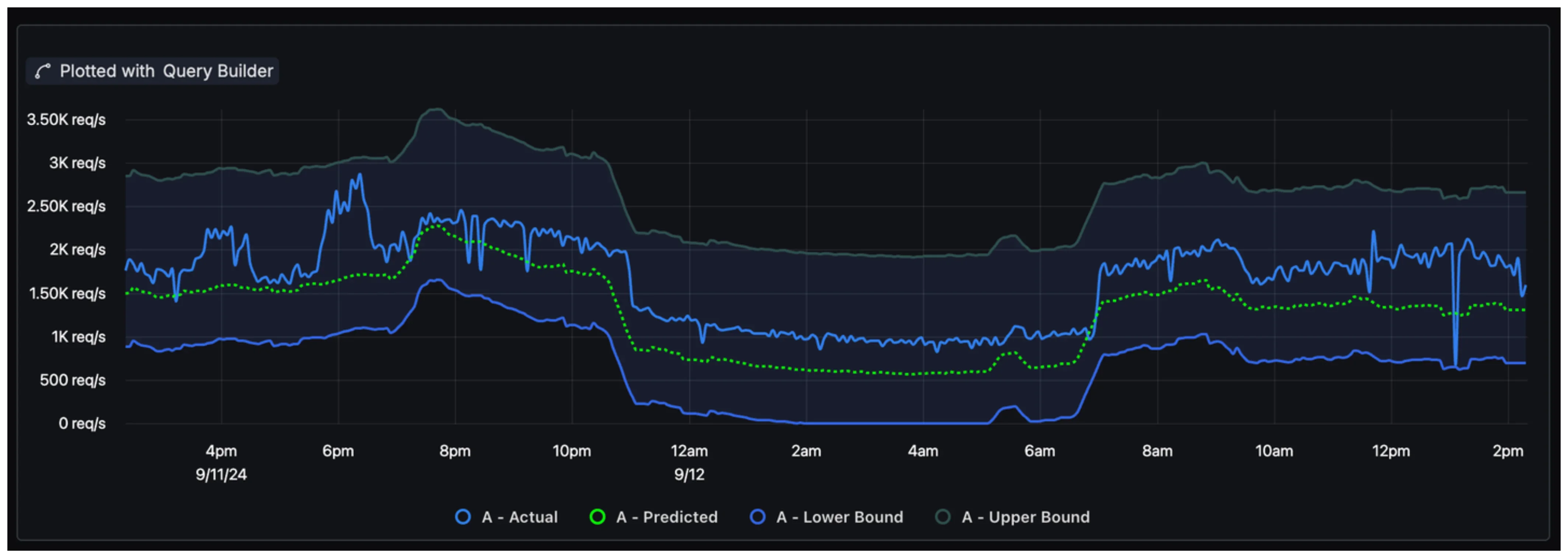
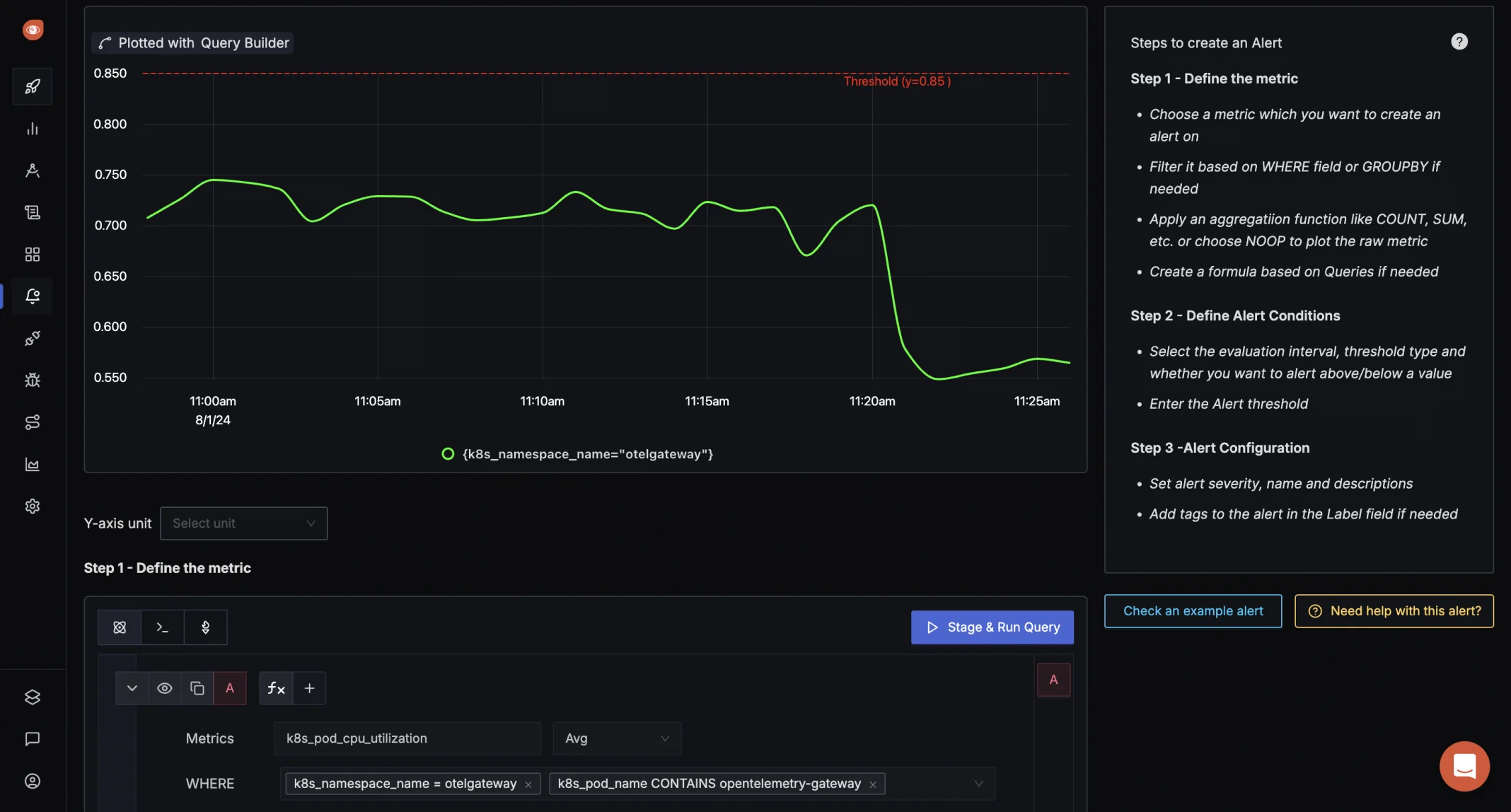
Step 1: Detect the Anomaly SigNoz provides a real-time monitoring dashboard where you can visualize application and infrastructure metrics.SigNoz enable users to create smarter alerts based on dynamic metrics, moving beyond traditional fixed-threshold alerts.
For example, if your application is experiencing high latency, the SigNoz dashboard might show a sudden spike in response time.
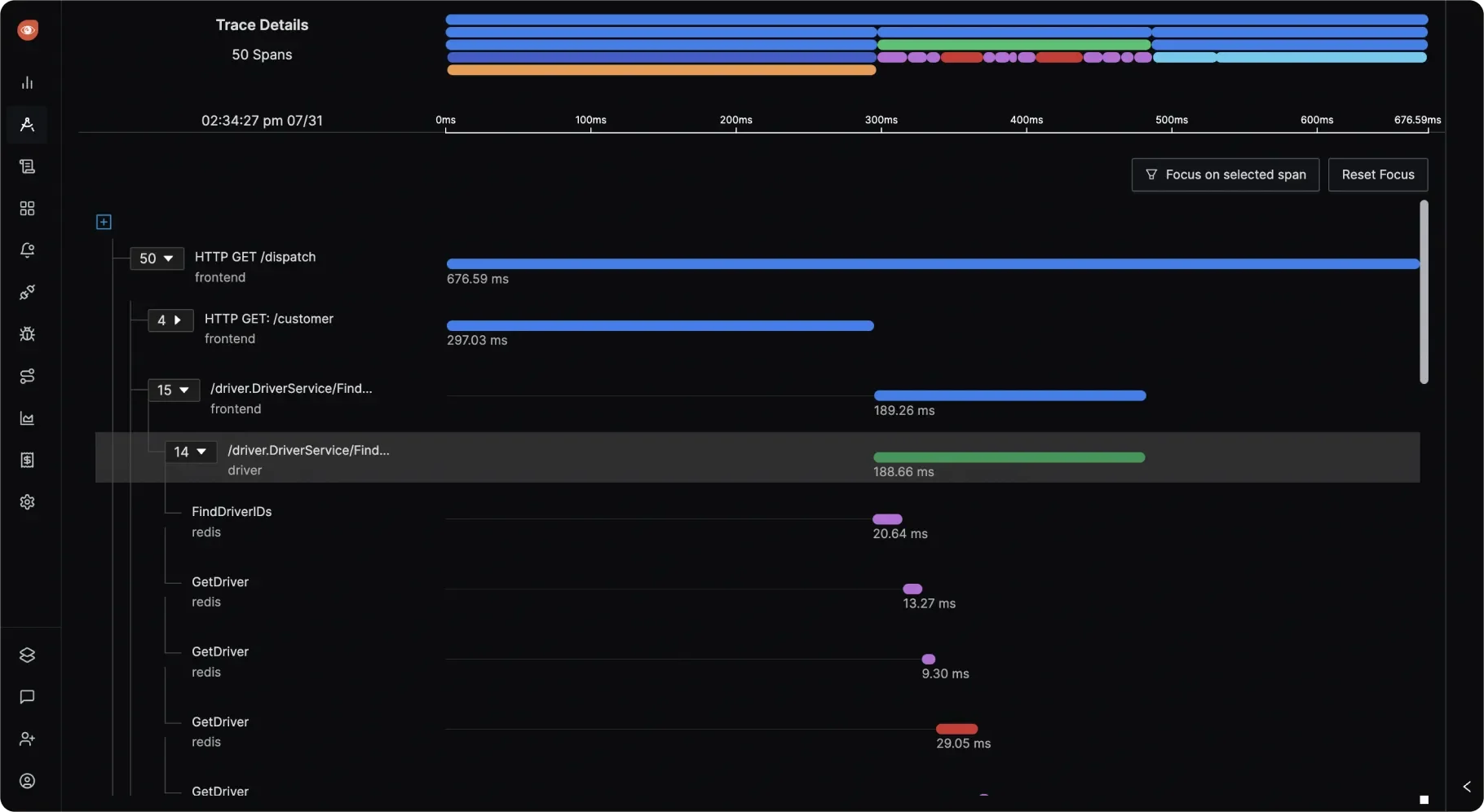
Step 2: Analyze the Root Cause with Distributed Tracing Navigate to the distributed tracing view to investigate the root cause. Traces reveal that one microservice takes significantly longer to respond due to a database query issue.
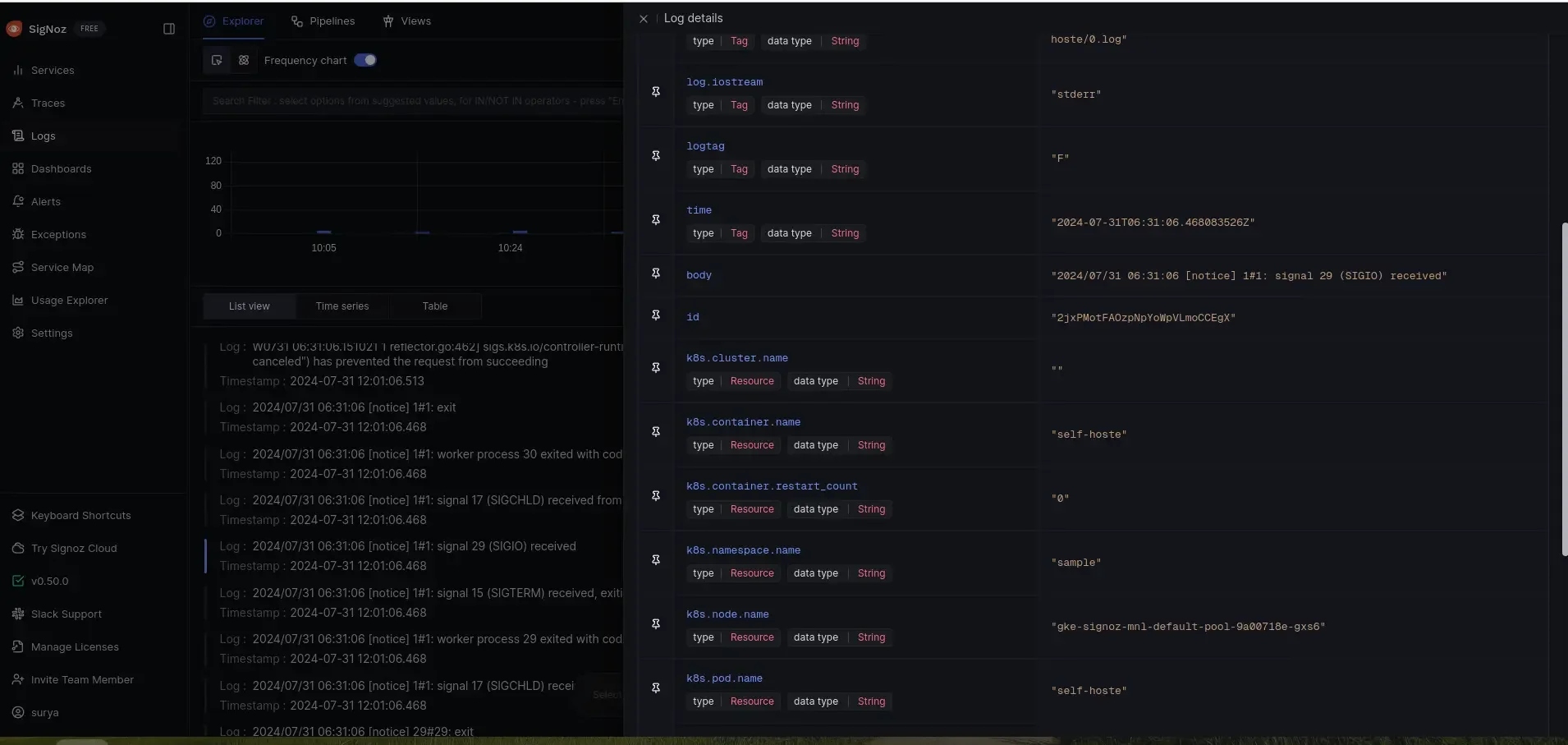
Step 3: Correlate Performance Metrics with Logs Using SigNoz's integrated logging and correlation features, filter logs related to the problematic service during the incident timeframe. The logs indicate a slow SQL query causing the delay.
Step 4: Set Up Alerts to Prevent Future Incidents Create an alert in SigNoz to monitor response time thresholds for the affected service. This ensures your team is notified immediately if latency issues arise again.
Benefits of the Workflow
- Accelerated Incident Detection: Real-time monitoring helps identify problems early.
- Efficient Root Cause Analysis: Distributed tracing pinpoints service-level bottlenecks.
- Proactive Prevention: Alerts ensure similar issues are detected before escalating.
- Comprehensive Insights: Logs and metrics together create a detailed incident narrative.
By following this structured approach with SigNoz, your incident response process becomes more efficient, reducing downtime and improving system reliability.
Key Takeaways
- The incident response cycle provides a structured approach to managing cybersecurity threats.
- Preparation is crucial — develop a comprehensive plan and assemble a trained team.
- Quick detection and thorough analysis are essential for minimizing damage.
- Containment strategies must be tailored to different types of incidents.
- Secure recovery involves not just restoration, but also strengthening defenses.
- Post-incident activities drive continuous improvement in your security posture.
- Tools like SigNoz can enhance your incident detection and analysis capabilities.
FAQs
What is the difference between the NIST and SANS incident response frameworks?
While both frameworks cover similar ground, the NIST framework (discussed in this article) is more comprehensive and detailed. The SANS framework simplifies the process into six phases: Preparation, Identification, Containment, Eradication, Recovery, and Lessons Learned. NIST's approach provides more granular guidance, especially in the areas of detection and analysis.
How often should an organization review and update its incident response plan?
At a minimum, review and update your incident response plan annually. However, it's best to treat your plan as a living document. Update it after each significant incident, when new threats emerge, or when your organization undergoes major changes in infrastructure or business processes.
What are some common mistakes organizations make during incident response?
Organizations often fail to communicate effectively, rush to address threats without understanding their scope, neglect to preserve evidence, overlook human factors skip post-incident reviews, missing critical learning opportunities.
How can small businesses implement an effective incident response process with limited resources?
Small businesses can prioritize key risks, use cloud-based tools, outsource to managed service providers, collaborate with peers, and rely on free or open-source tools to build a cost-effective incident response process.
